Baidu Cloud Compute Security Description
Security risks
Brute-force attacks
Log in to the Baidu AI Cloud console to check the security protection status of servers under your account on the Security > Host Security > Login Management page. Click "Login Details" on the far right of each server to view brute-force attack events. Baidu AI Cloud automatically protects against brute-force attacks; six consecutive login failures within a short period trigger automatic IP blocking. Most events listed are cases intercepted by the Baidu AI Cloud platform. A screenshot is provided below. You can also select the "Success" filter under Login Status to check if any attacks were successful. For flagged IPs, click "One-click Blacklist Source IP" for complete access restriction.
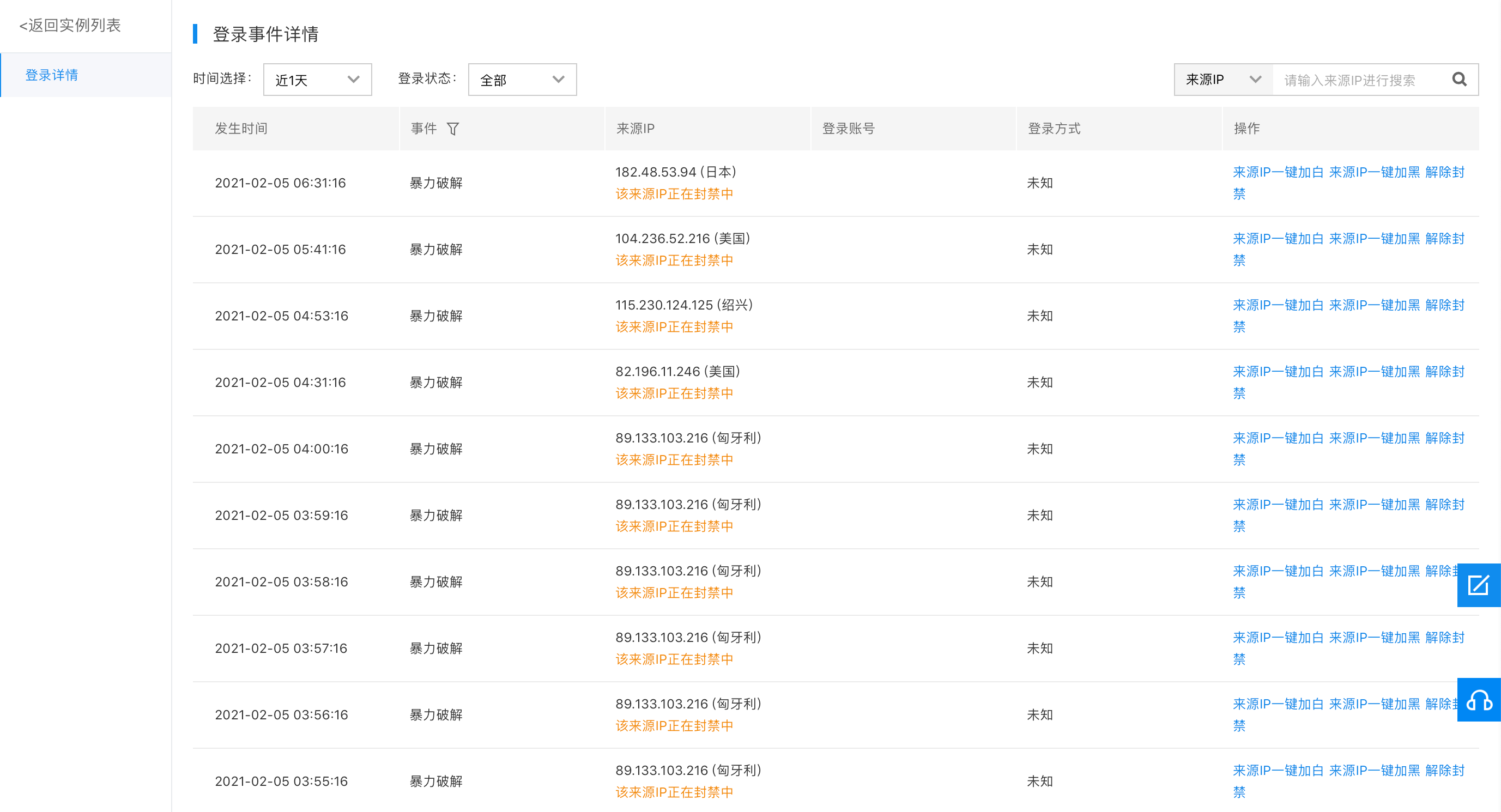
Virtual machine hacked
After a server is hacked, malicious scripts are often implanted. On a Linux system, you can use the crontab -l command to check for unusual CronJobs. Additionally, intruders might modify or delete system files, such as altering subdirectory files under /usr, clearing files in /usr/bin and /usr/sbin, or changing configuration files in /etc., including tampering with /etc/passwd and /etc/shadow. On Windows systems, suspicious programs might exist in system files, or system logs may show unusual error messages. To address such issues, it is recommended to roll back the data with snapshots or reinstall the operating system to thoroughly clean the system.
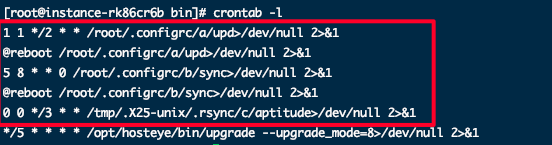
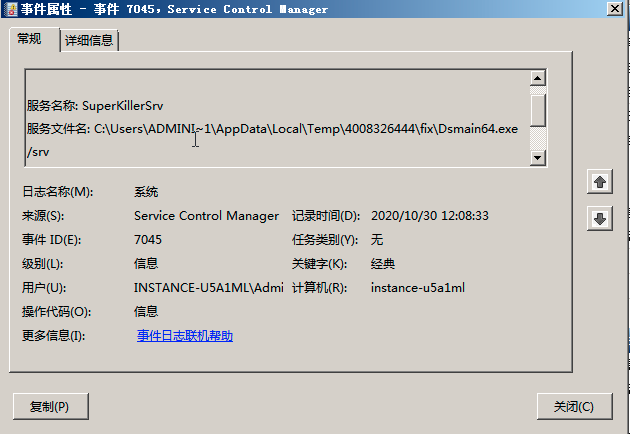
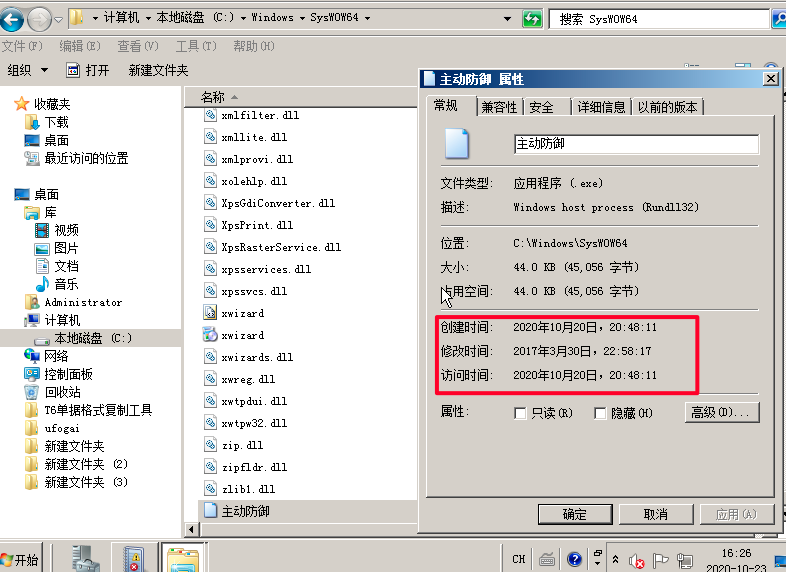
Common viruses
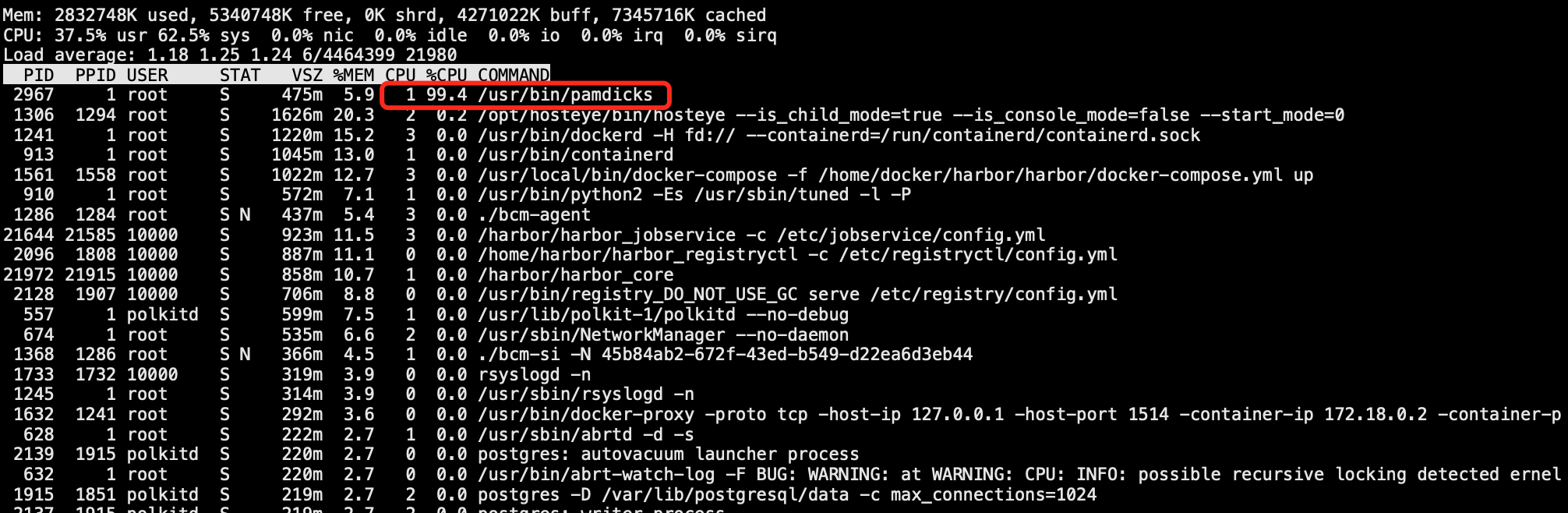
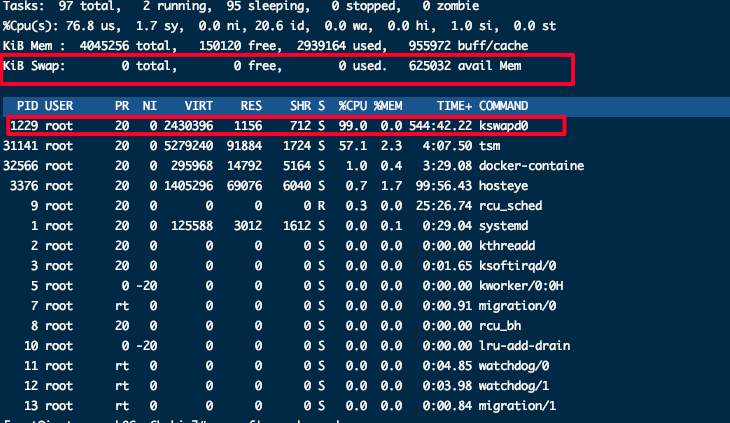
Crypto miner virus
The term "mine" refers to virtual currencies, which include various types such as Bitcoin and Monero. These currencies function as digital money with considerable value in the virtual world. Crypto miner viruses are sophisticated Trojans implanted by attackers into compromised devices, leveraging the computational power of these devices to mine virtual currency for profit. A common symptom of crypto miner virus infection is unexplained, sustained 100% CPU usage, which prevents other programs from functioning properly. Typically, crypto miner virus processes hide or disguise themselves as system processes, making them difficult to completely eradicate once detected. To resolve such issues, it is recommended to roll back the data with snapshots or reinstall the operating system to thoroughly clean the system.
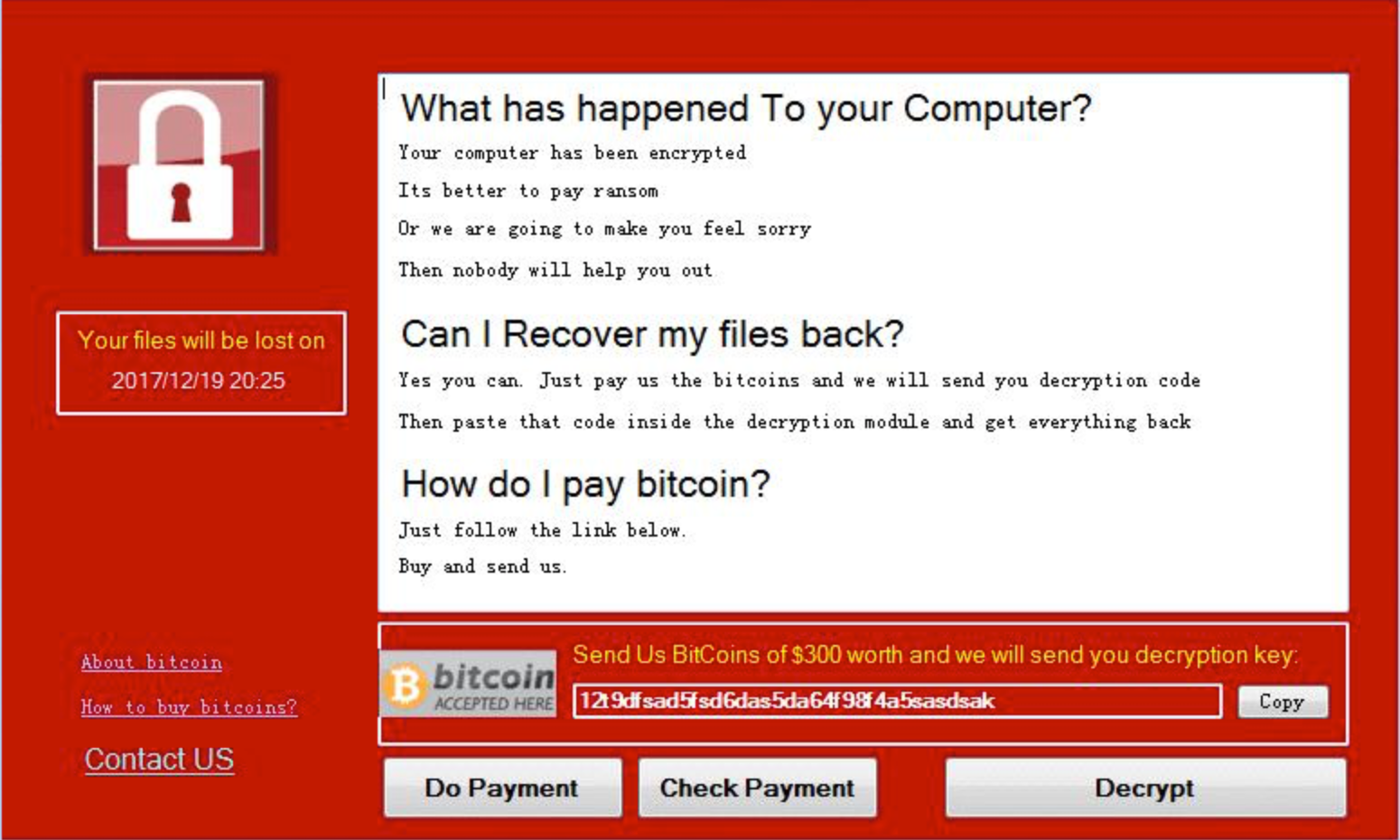
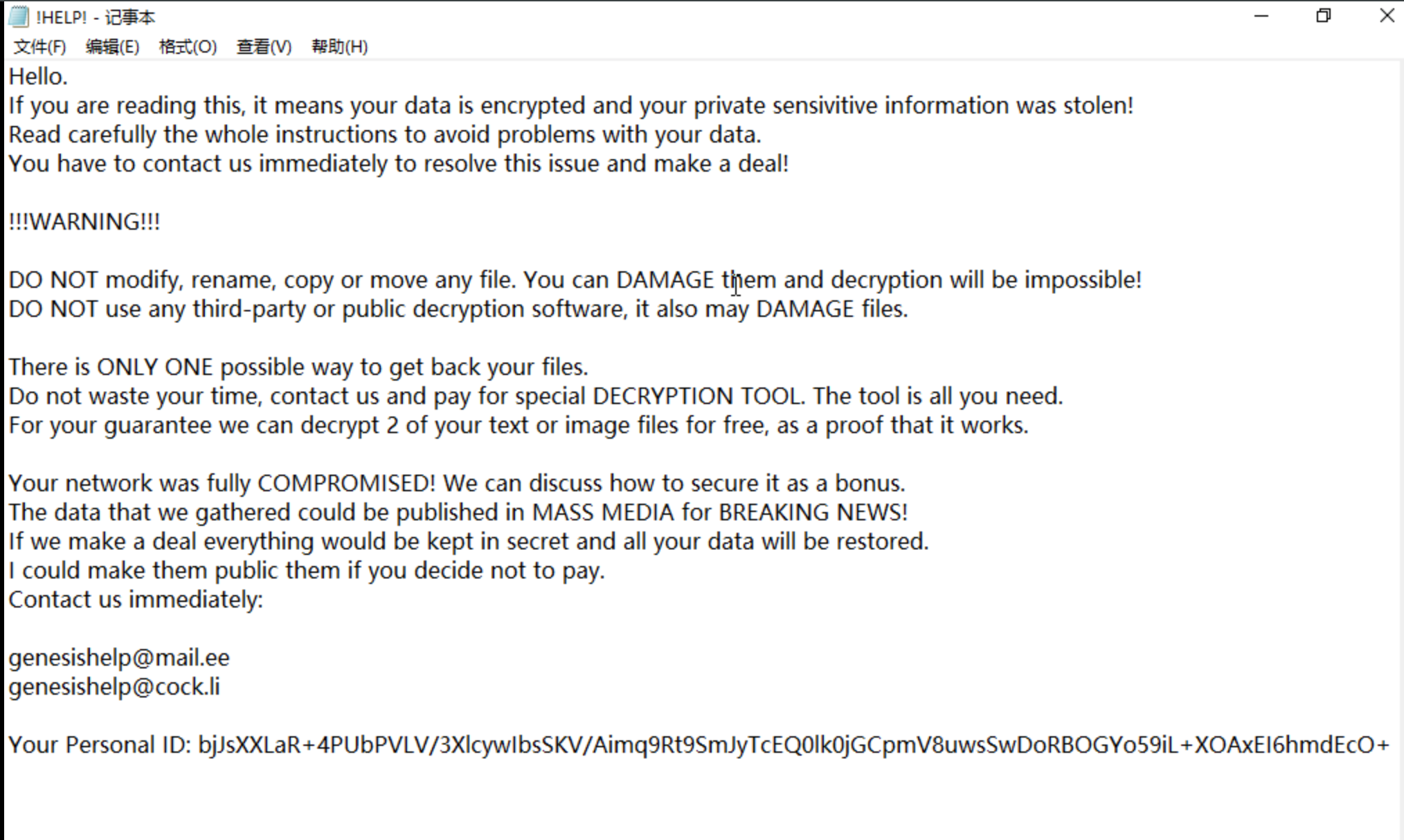
Ransomware
Ransomware primarily spreads through emails, Trojan programs, and malicious web code attacks. This virus employs various encryption algorithms to lock files, leaving victims unable to decrypt them without the corresponding private key. Ransomware is highly destructive and creates significant harm. Once infected, users may face irreversible data loss as reverse decryption is nearly impossible. After encrypting files, the virus typically changes the wallpaper and generates ransom note files on the desktop or other prominent locations, instructing users to pay for decryption. Additionally, ransomware variants evolve quickly and are resistant to standard antivirus software. To address such issues, it is recommended to roll back the data with snapshots or reinstall the operating system.
Security reinforcement measures
Restrict publicly accessible IPs and ports using security groups or ACLs.
Configure security groups in the Management Console to allow access only from specific IPs and ports, or use ACLs to block particular IPs, IP ranges, and ports.
For creation and configuration of security groups, refer to: Create Security Group
For creation of ACL rules, refer to: ACL Introduction
Modify the default remote port
Attackers often scan default ports over the public network before launching brute-force attacks based on the results. Changing the default remote port number can be an effective preventive measure.
For Windows OS, refer to: Modify the Default Remote Port on Windows Servers
For Linux OS, refer to: Modify Default Remote Connection Port in Linux
Reasonable password policy
It is advised to use complex passwords that combine letters, numbers, and special characters. Avoid weak or easily guessable passwords like admin@123 or 1qaz!QAZ, and ensure passwords are changed regularly.
Use snapshots and images
Baidu AI Cloud Platform provides two data backup options: snapshots and images. Snapshots can be created for all cloud disk servers, whereas images are limited to system disks. Users can back up server data regularly and recover it via rollback in case of security risks, offering a simple and efficient solution. However, note that snapshots are currently chargeable, while images are free of cost.
For creation of snapshot, refer to: Manual Snapshots
For creation of custom images, refer to: Create Custom Images
For snapshot prices, refer to: Charge Type of Snapshots
Use the host security tools provided by Baidu AI Cloud
Hosteye, a host security product offered by Baidu AI Cloud, ensures continuity for services running on user servers. It is characterized by its high stability, lightweight design, and ease of deployment, allowing small- and micro-sized enterprises to establish host security systems quickly. It also supports private and hybrid deployment scenarios for large- and medium-sized enterprises based on their specific needs.
Official product documentation: {-1-}Introduction to Hosteye Product](https://cloud.baidu.com/doc/HOSTEYE/s/Ujwvxjssw)[
Login management
Regularly review the Hosteye Client - Login Management - Login Details section on the console for malicious IPs from brute-force attacks. These can be blacklisted with a single click, permanently blocking their access.
For detailed usage, refer to: Login Management
Virus scanning and killing
Real-time protection can be enabled for specific directories, allowing instant alerts for malicious processes. Monitored directories include /home, /root, /bin, /sbin, \windows\system, \windows\system32, and others.
For detailed usage, refer to: Virus Scanning and Killing
Website backdoor
All website backdoors detected through real-time protection require enabling the real-time protection feature. Note that real-time protection is only applicable to web directories.
For detailed usage, refer to: Website Backdoor
Alarm settings
Users can configure alert notification methods and set reminder times for security events such as "Brute Force Attack Succeeds" and "Remote Login Behavior.\
For detailed usage, refer to: System Management
Security Risk Detection (SRD)
Security Risk Detection (SRD) is a security risk analysis service provided by Baidu AI Cloud that identifies common web vulnerabilities such as SQL injection and XSS cross-site scripting, along with system software security flaws. SRD helps users quickly detect issues within their systems, supports timely fixes, and enhances overall business security and stability.
Official product documentation: Security Risk Detection (SRD)
Cloud Advisor
The Cloud Advisor product enables customers to use Baidu AI Cloud services more securely, reliably, and cost-effectively. Based on Baidu AI Cloud’s extensive operational and maintenance experience, this product systematically inspects and reports potential risks or issues encountered by customers while using Baidu AI Cloud, providing resolutions and technical support. Cloud Advisor can be likened to a "health check report" for Baidu Cloud Compute, offering customers a comprehensive understanding of potential server risks.
Official product documentation: Cloud Advisor ACA
