How to Enable or Disable Intel CPU Vulnerability Patch in Linux Image
Overview
This document focuses on how to enable or disable mitigation measures for vulnerabilities like Meltdown, Spectre, MDS, and others in Linux Images.
Meltdown and Spectre
Vulnerability details
Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5715/CVE-2017-5753) are security vulnerabilities found in Intel processor chips, caused by hardware-level design flaws. These flaws may result in OS kernel information leaks or unauthorized applications accessing kernel data.
Vulnerability ID:
CVE-2017-5753
CVE-2017-5715
CVE-2017-5754
The Linux kernel community has introduced mitigation measures for these vulnerabilities. However, some of these measures can significantly reduce system performance. Currently, to ensure GuestOS performance, Baidu AI Cloud disables Meltdown and Spectre vulnerability fixes by default in GuestOS.
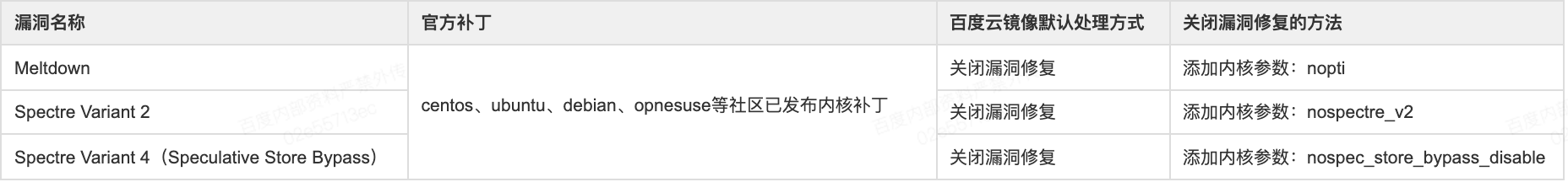
SRSO
Vulnerability details
SRSO (CVE-2023-20569) is a security vulnerability present in AMD processor chips. It relates to speculative execution mechanisms and return stack buffer overflows, potentially causing data leaks or system damage.
Many modern OS kernel versions include default SafeRET measures to mitigate the AMD SRSO vulnerability. However, these measures can noticeably degrade processor performance.
According to the AMD official document Options and Considerations for SRSO Vulnerability Mitigation Measures for Public Cloud Users, AMD considers the overall security risk related to SRSO low in typical production environments. For cloud users employing common side-channel protections in typical production environments, AMD deems it reasonable to disable SafeRET during OS configuration.
To maintain GuestOS performance, Baidu AI Cloud disables the SRSO mitigation measures by default in public images (by adding spec_rstack_overflow=off to the kernel boot parameters). Users can determine whether to enable the mitigation measures (by removing spec_rstack_overflow=off) based on their specific security needs.
MDS
Vulnerability details
Intel "Micro Architectural Data Sampling (MDS)" is a vulnerability that may allow unauthorized sensitive data leakage through side-channel attacks.
Vulnerability ID
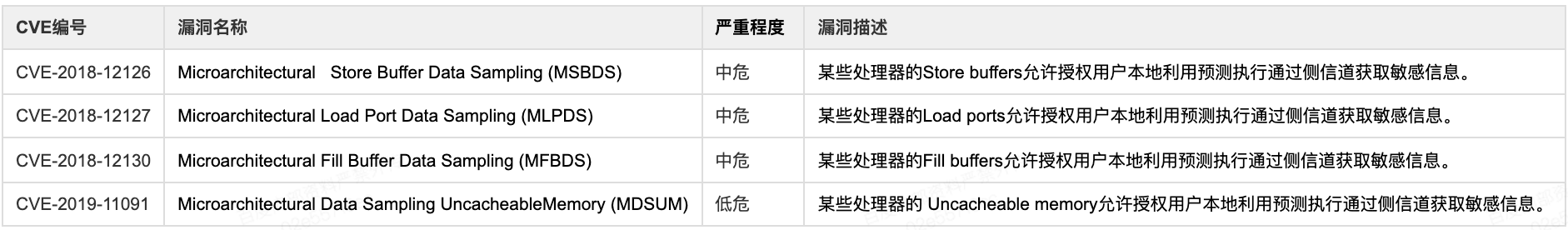
Scope of impact
For detailed information about affected Intel CPU models, refer to the Intel Security Bulletin.
How to enable or disable MDS vulnerability fixes
The Linux community has addressed these processor vulnerabilities by updating kernel patches for MDS.
The following images are involved public images:
- centos 7 / 8
- debian 9 /10
- ubuntu 16.04 / 18.04 Ubuntu 20.04 Kernel Unaffected
- opensuse 15
Mitigating these vulnerabilities may cause a notable decline in performance. Users with tight performance requirements can disable these fixes to enhance system speed.
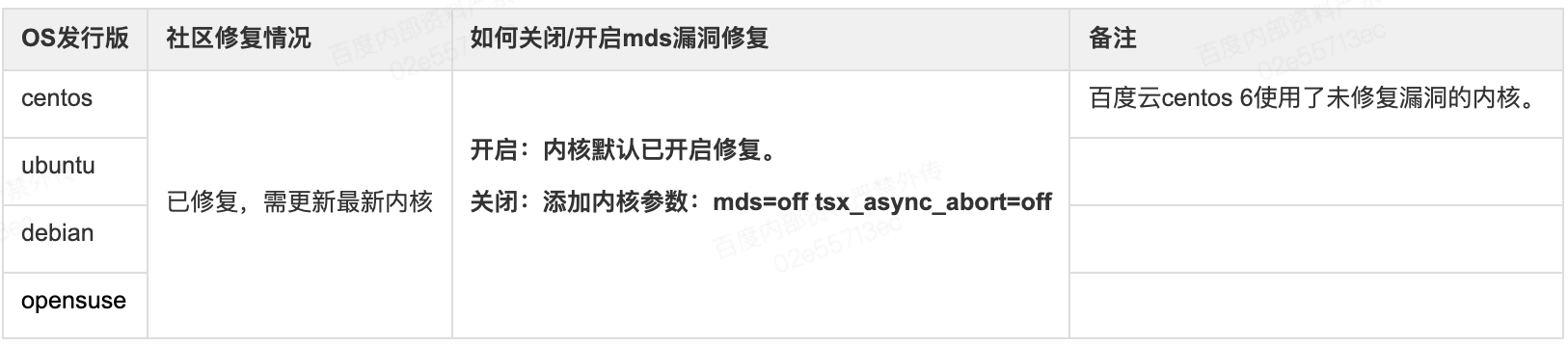
Community fixes status
| OS | Distribution version | Fixed kernel version | Community |
|---|---|---|---|
CentOS | 6 | kernel-2.6.32-754.14.2.el6 | https://access.redhat.com/errata/RHSA-2019:1169 |
| 7 | kernel-3.10.0-957.12.2.el7 | https://access.redhat.com/errata/RHSA-2019:1168 | |
| 8 | kernel-4.18.0-80.1.2.el8_0 | https://access.redhat.com/errata/RHSA-2019:1167 | |
Ubuntu | 16.04 ESM (Xenial Xerus) | Released (4.4.0-148.174) | |
| 18.04 LTS (Bionic Beaver) | Released (4.15.0-50.54) | ||
| 20.04 LTS (Focal Fossa) | Not vulnerable (5.4.0-9.12) | ||
| Debian |
