Configure IAM Custom Permission Policy
The system authorization policy provided by the Cloud Container Engine (CCE) has relatively broad granularity. If this level of authorization doesn't suit your needs, you can create a custom policy. For instance, to manage operational permissions for a specific cluster, you can use a custom policy to achieve fine-grained access control.
Operation steps
Create via visual editor
- Sign in to the Baidu AI Cloud official website and enter the management console.
- Click Identity and Access Management in the personal information section at the upper-right corner of the console to enter the Identity and Access Management console page.
- Go to Policy Management in the left-hand menu to access the Permission Policy List page.
-
Click Create Policy, and select Create via visual editor in the Select Policy Creation Method pop-up box.
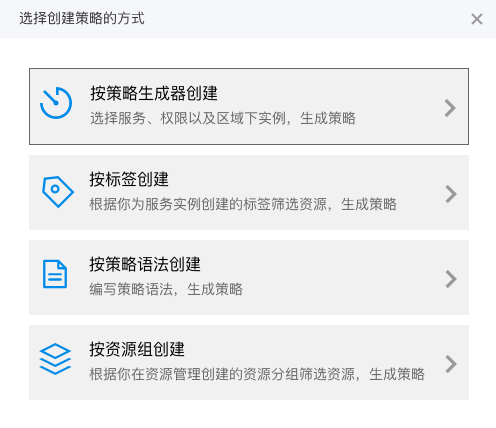
- Fill in the policy name and configure the permissions on the "Create Permission Policy" page.
-
Click Add Permission and complete the permission configuration in the pop-up box. Here, granting read-only permissions for a cluster in the Hong Kong region is used as an example:
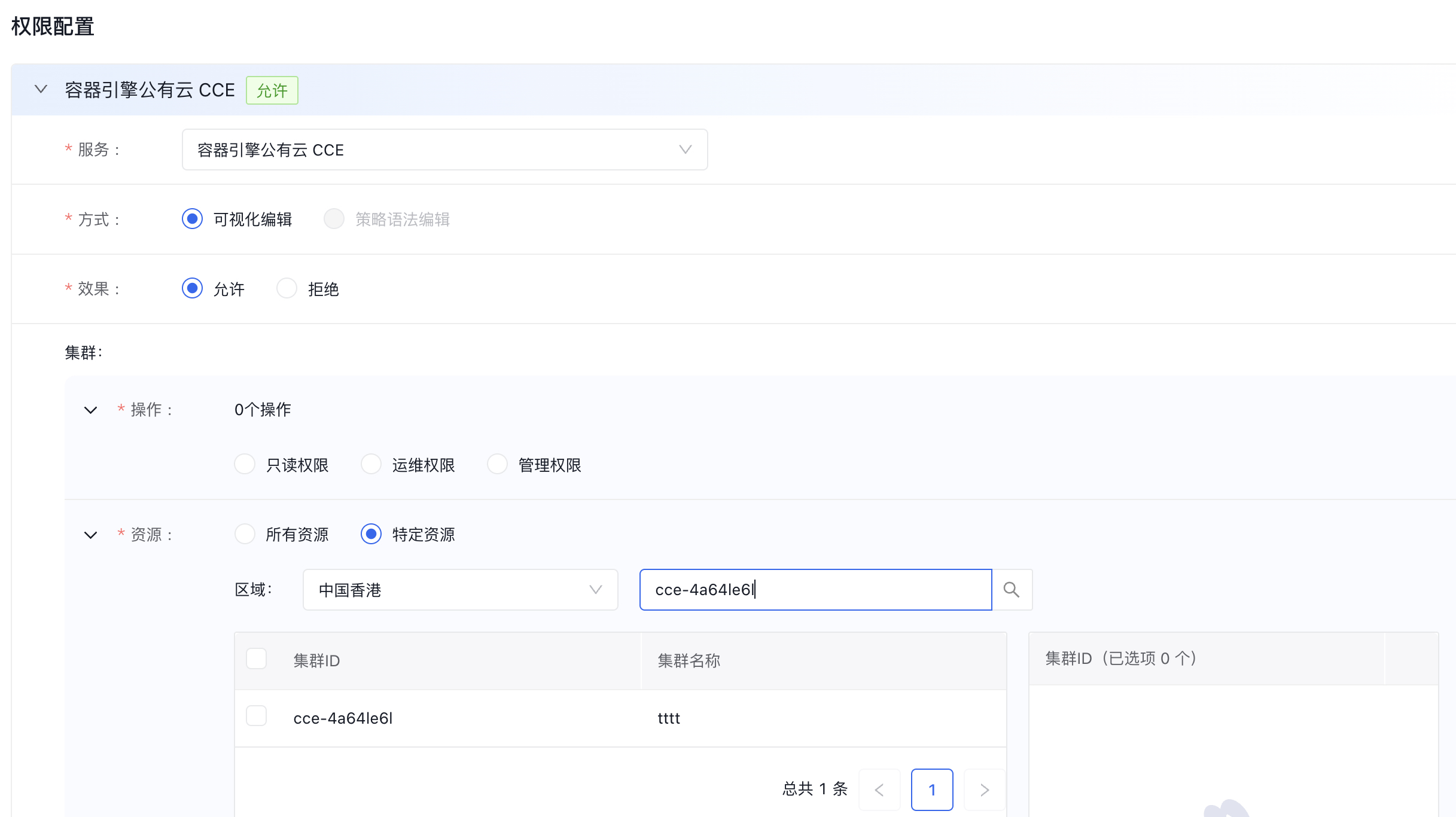
| ConfigMap | Required/Optional | Configuration |
|---|---|---|
| Select service | Required | Choose the applicable service. In this case, select Cloud Container Engine (CCE). |
| Permission effectiveness | Required | Select whether to Allow or Deny the operation. Here, choose Allow. |
| Cluster | Required | Select the cluster permissions, and in this case, pick Read-only. |
| Select the resource. | Required | Specify the cluster resources you want to operate on. Here, select "Specific Resources," choose the Hong Kong, China region, and check the clusters within this region. If you wish to operate on all clusters, select "All Resources." |
1>**Description**
2>
3>* Read-only permission: Have read-only permission for all clusters associated with the selected tag.
4>* Operation and maintenance permission: Have full read-write permissions for all clusters associated with the selected tag but be unable to delete the cluster
5>* Management permission: Have full read-write permissions for all clusters associated with the selected tag and be able to delete the cluster
6>
7>* If you have higher configuration requirements, more information can be found in [Manage IAM Policies](https://cloud.baidu.com/doc/IAM/s/Xjxlkojqq).- Click the OK button to complete the creation. You can view the created policy on the Permission Policy List page.
- Grant the custom permission policy to the target IAM user. For specific steps, refer to IAM User Authorization.
Create via ACL
When creating a custom authorization policy, you need to understand the basic structure and syntax of the authorization policy language. For more information, please refer to ACL Description.
- Sign in to the Baidu AI Cloud official website and enter the management console.
- Click Identity and Access Management in the personal information section at the upper-right corner of the console to enter the Identity and Access Management console page.
- Go to Policy Management in the left-hand menu to access the Permission Policy List page.
- Click Create Policy, and select Create via ACL in the Select Policy Creation Method pop-up box.
- On the Create Permission Policy page, compose the custom authorization policy content. Here, granting full control permissions for all clusters across all regions is used as an example:
1{
2 "version": "v1",
3 "accessControlList": [
4 {
5 "service": "bce:cce",
6 "region": "*",
7 "resource": [
8 "*"
9 ],
10 "effect": "Allow",
11 "permission": [
12 "CLUSTER_CREATE",
13 "CLUSTER_DELETE",
14 "CLUSTER_MANAGE",
15 "CLUSTER_READ",
16 "CLUSTER_LIST"
17 ]
18 }
19 ]
20}Where:
-
regionspecifies the region to be authorized, with the following possible configurations:- Permission granted to all regions
1 "region": "*"
2 ```
3 * Permission granted to a single region, e.g., Beijing (bj)
4 ```
5 "region": "bj"
6 ```
7 >**Description**
8 >
9 >A single `accessControl` can only specify one region. To specify multiple regions, multiple instances must be created.
10 >
11
12* `resource` specifies the resources to be authorized, with the following possible configurations:
13 * Permissions granted to all clusters1"resource": [
2 "*"
3 ]
4```
5* Permission granted to a single cluster
6```
7"resource": [
8 CCE_Cluster/cluster ID
9 ]
10```
11* Permission granted to multiple clusters
12```
13"resource": [
14 CCE_Cluster/cluster ID
15 CCE_Cluster/cluster ID
16 ]
17```
18 >**Description**
19 >
20 >`Cluster ID` should be replaced with the actual cluster ID requiring authorization.
21 >-
actionspecifies the cluster operation permissions to be granted:- You can select different permission combinations based on actual needs
1 "permission": [
2 CLUSTER_CREATE, # permissions granted to create a cluster
3 "CLUSTER_DELETE", # Permissions granted to delete the cluster
4 CLUSTER_MANAGE, # permissions granted to manage the cluster
5 "CLUSTER_READ", # Permissions granted to only read the cluster
6 CLUSTER_LIST # permissions granted to cluster list
7 ]- Click Finish to complete the creation of a custom policy.
- Grant the custom permission policy to the target IAM user. For specific steps, refer to IAM User Authorization.
Custom authorization policy example
The following policies do not include permissions for associating clusters with cloud services (e.g., Baidu Cloud Compute (BCC), Baidu Load Balancer (BLB)). If required, separately grant IAM users the respective permissions for these products.
- Grant read-only permission for a single cluster to the IAM user, such as cluster ID cce-xxxx
1{
2 "version": "v1",
3 "accessControlList": [
4 {
5 "service": "bce:cce",
6 "region": "*",
7 "resource": [
8 "CCE_Cluster/cce-xxxx"
9 ],
10 "effect": "Allow",
11 "permission": [
12 "CLUSTER_READ",
13 "CLUSTER_LIST"
14 ]
15 }
16 ]
17}- Grant full control permission for a single cluster to the IAM user, such as cluster ID cce-xxxx
1{
2 "version": "v1",
3 "accessControlList": [
4 {
5 "service": "bce:cce",
6 "region": "*",
7 "resource": [
8 "CCE_Cluster/cce-xxxx"
9 ],
10 "effect": "Allow",
11 "permission": [
12 "CLUSTER_DELETE",
13 "CLUSTER_MANAGE",
14 "CLUSTER_READ",
15 "CLUSTER_LIST"
16 ]
17 }
18 ]
19}