Password-Free Pull of Container Image
This document describes how to pull images from CCR private repositories by installing and configuring the cce-image-plugin, thereby eliminating the repetitive work of explicitly configuring ImagePullSecret in the cluster resource YAML. For the mechanism, refer to Configure imagePullSecrets for Pods via serviceAccount
Preparation
- Create a dedicated IAM user
To use the cce-image-plugin, configure your AK (Access Key) and SK (Secret Key). It's recommended to apply for a dedicated IAM user and use its AK and SK to better manage permission scopes.
- Add permissions to the IAM user
The IAM user must have access permissions for the CCR service, with a minimum policy level of CCROperatePolicy.
For details, refer to: How to Add Permission Policies for IAM Users
- Enable CCR service (create a CCR account)
Navigate to the CCR page on the console and create a CCR account as prompted. For details, refer to: Enable CCR Service
- Add image registry permissions
Grant namespace permissions to the IAM user. For details, refer to: Add Image Permissions
- Create an ak and sk
Create an AK and SK for the IAM user. Refer to the diagram below for detailed instructions on the operation path.
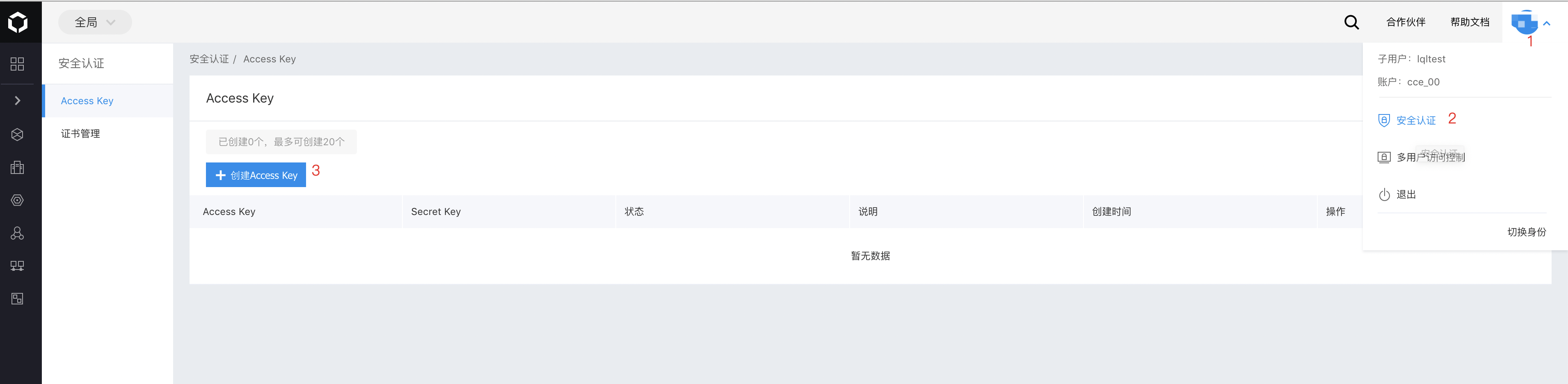
Enabling steps
Deploy plugins
- Select in sequence: Cloud Container Engine (CCE) ->Helm Template ->Baidu AI Cloud Template
- Search for the template by the template name
cce-image-plugin - Click Install and fill in the corresponding parameters
1*Instance name: name of the plugin instance (e.g., imagepull);
2 *Deployment cluster: Select the cluster where the image plugin needs to be deployed;
3 *accessKey: ak of the IAM user;
4 *secretKey: sk of the IAM user;
5 *serviceAccount: The serviceAccount that the plugin acts on;
6 *namespace: The cluster namespace where the plugin acts.
7 Pods created in the specified namespace and using the specified serviceAccount will automatically set the spec.imagePullSecrets field.
8 If a resource itself specifies imagePullSecrets, the secret generated by the plugin will not be injected into that resource, meaning that the resource cannot enable the password-free pulling function.