Secret Management
Secret
Secret is a K8S API resource used to store sensitive information like passwords, OAuth tokens, and SSH keys. Users can manage secret resources in CCE via the console or kubectl.
Prerequisites
- A K8S Cluster CCE has been created. For specific operations, refer to Create a K8S Cluster CCE.
- A namespace has been created. For specific operations, refer to Basic Operations of Namespaces.
Manage secret via the console
Create secret
- Sign in to the Baidu AI Cloud management console. Navigate to Product Services - Cloud Native - Cloud Container Engine (CCE). Click Cluster Management - Cluster List, then select the target cluster to enter the Cluster Details page. In the sidebar, click Configuration Management - Secret.
-
On the secret list page, click Create Secret, and the system will pop up a secret pop-up box where you can configure the relevant parameters.
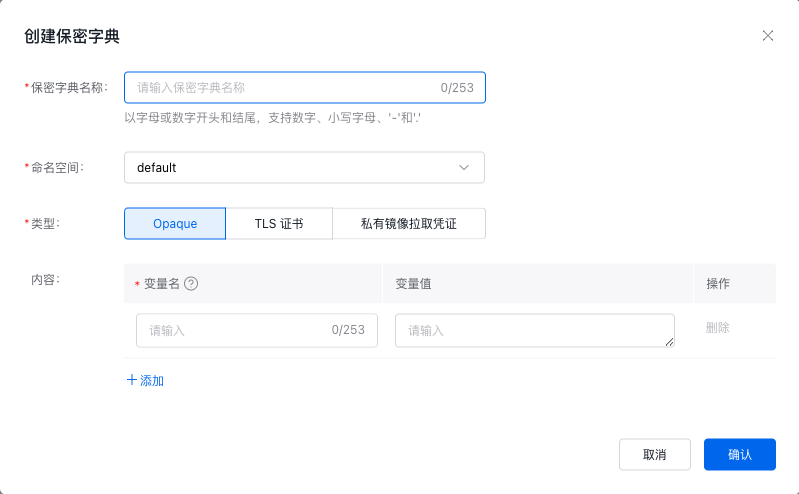
| ConfigMap | Required or not | Description |
|---|---|---|
| Secret name | Required | Please enter a custom name. |
| Namespace | Required | Indicate the namespace where the created resources are located. |
| Types | Required | Opaque, TLS certificate, and private image pull access credential types are provided. Please select according to actual needs. Opaque: Suitable for storing key certificates and configuration files. Value will be encoded in base64 format. TLS certificate: Suitable for storing TLS certificates and private keys. Private image pull access credential: Suitable for storing certification information for private docker registry. |
| Content | Required | When the secret type is set to opaque, variable names and values must be configured, with support for adding multiple entries. |
| Cert | Required | When the secret type is set to TLS certificate, the certificate must be added or the certificate file must be imported. |
| Key | Required | When the secret type is set to TLS certificate, the private key must be added or the private key file must be imported. |
| Image registry address | Required | When the secret type is set to private image pull access credential, the image registry access address must be entered. |
| Username | Required | When the secret type is set to private image pull access credential, the user name for signing in to the Image Registry must be entered. |
| Password | Required | When the secret type is set to private image pull access credential, the password for signing in to the Image Registry must be entered. |
| Confirm password | Required | When the secret type is set to private image pull access credential, the password for signing in to the Image Registry must be entered again. |
- Click the OK button to complete the creation.
Query secret
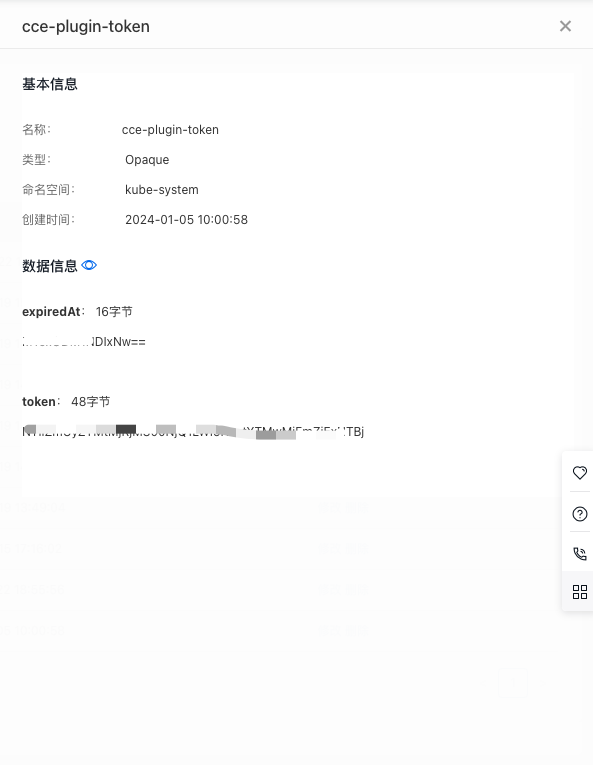
Click the target secret name in the list page to open the secret details page in the right sidebar, which includes:
- Basic information: name, namespace, type, creation time, and data information
- Data Information: There is a "Hide" button available, which allows you to toggle the visibility of the data information details.
Edit secret
On the secret list page, select the secret to be edited, click the Edit button, make modifications, and then click the OK button to complete the editing.
Delete secret
On the secret list page, select the secret to be deleted, click the Delete button, and then click OK in the pop-up box to complete the deletion.
Manage secret via kubectl
Secret YAML example:
1apiVersion: v1
2kind: Secret
3metadata:
4 name: baidu-secret
5data:
6 username: dXNlcm5hbWU= # echo -n "username" | base64
7 password: cGFzc3dvcmQ= # echo -n "password" | base64Use secret as a file in Pod:
1apiVersion: apps/v1
2kind: Deployment
3metadata:
4 name: app-nginx
5 labels:
6 app: nginx
7spec:
8 selector:
9 matchLabels:
10 app: nginx
11 template:
12 metadata:
13 labels:
14 app: nginx
15 spec:
16 containers:
17 - name: nginx
18 image: hub.baidubce.com/cce/nginx-alpine-go:latest
19 volumeMounts:
20 - name: foo
21 mountPath: "/etc/foo"
22 readOnly: true
23 volumes:
24 - name: foo
25 secret:
26 secretName: baidu-secretThe file corresponding to the secret baidu-secret will be located in /etc/foo of Pod:
1# Enter container using exec -it
2# ls /etc/foo/
3password username