Use K8S_Ingress via CCE
Ingress is a Layer 7 traffic ingress method provided by Kubernetes, which manages traffic by connecting external load balancers with internal container services. Compared to LoadBalancer Service, Ingress simplifies the management of externally exposed ports while leveraging the capabilities of external load balancers to provide more comprehensive routing and security rules. For details, refer to the official website: Kubernetes Ingress.
Ingress mainly consists of two parts:
- Ingress resource object: Define the Kubernetes ingress object, which can be created and managed using YAML to map services to domain names.
- Ingress Controller: A public component deployed within the cluster that translates ingress resource object configurations into external load balancer settings, ensuring the management and updating of load balancers.
CCE offers an implementation of the CCE Ingress Controller using Baidu AI Cloud's load balancer services. When utilizing ingress, users can simultaneously create, configure, and manage Baidu AI Cloud's Load Balancer (Application BLB) and Elastic IP (EIP), facilitating external traffic management for the cluster. The use of ingress aligns with native Kubernetes functionality. Users can manage and create ingress through the Baidu AI Cloud console or YAML files.
Prerequisites
- The CCE Ingress Controller component has been installed for the cluster. For more information, see CCE Ingress Controller Description.
Operation steps
- Sign in to the Baidu AI Cloud official website and enter the management console.
- Select Product Tour - Containers - Cloud Container Engine and click to enter the CCE management console.
- Click Cluster Management - Cluster List in the left navigation bar.
- Click on the target cluster name in the Cluster List page to navigate to the cluster management page.
- On the cluster management page, click Network - Route to enter the route page.
- Click the Create Ingress button to enter the Create Ingress page for basic information configuration:
| ConfigMap | Required/Optional | Configuration |
|---|---|---|
| Ingress name | Required | Specify the name of the ingress. |
| Namespace | Required | Select the namespace where the ingress is located. Note that ingress can only forward traffic to services within its own namespace. |
| Load balancer | Required | Currently selecting Application BLB, the system will create or bind an application BLB instance for the ingress. |
| Access type | Required | Specify the service access type, supporting public network and intranet. |
| Specify BLB | Required | Choose to create a new application BLB or specify an existing one. Important: A BLB can only be associated with a single ingress and cannot be reused. |
| Specify EIP | Required | Configuration is supported only when Access Type is set to Public Network, and you can create a new EIP or specify an existing EIP. Note: One EIP can only be used for one ingress and cannot be reused. |
| Specify VPC subnet | Required | Select the subnet to which the BLB associated with the ingress belongs. If an existing BLB is chosen instead of creating a new one, this setting will not apply. |
- Set up forwarding rules.
| ConfigMap | Required/Optional | Configuration |
|---|---|---|
| Update strategy | Optional | Enable full configuration updates for the BLB. By default, only the forwarding rule configurations of the associated BLB listener are updated during ingress updates. When this option is enabled, all BLB configurations (e.g., listeners, certificates, health checks, and security groups) and related EIP settings (e.g., public network bandwidth) will be updated synchronously. |
| Listener port | Required | HTTP:80 is the default selection, with HTTPS:443 available as an alternative. |
| Certificate | Required | Configuration is supported only when HTTPS:443 is selected in Listener Port, to bind certificates for HTTPS listeners. |
| Extended domain name | Optional | Add multiple extended domain names for the HTTPS listener. |
| Forwarding rules | Required | Support configuring multiple forwarding rules. |
- Perform advanced configurations as needed.
| ConfigMap | Required/Optional | Configuration |
|---|---|---|
| Timeout duration | Required | Set the timeout duration for ingress to wait for responses from backend servers. |
| HTTP redirection | Required | Toggle HTTP redirection to automatically redirect HTTP requests to HTTPS ports. This configuration is only necessary when HTTPS is enabled. |
| Labels | Optional | Attach Kubernetes labels to the ingress resource. |
| Annotations | Optional | Add K8S annotations to ingress. For CCE-defined annotations, refer to BLB Ingress Annotation Description. |
- Click Complete button to complete creation.
Description:
- The newly created ingress will initially appear as "NotReady" on both the detail and forwarding rule pages. After a few minutes, once the configuration is complete, the ingress status will update to "Ready" and it will become operational.
Ingress usage example
Use the following YAML content to create deployment and service resource examples respectively:
1 apiVersion: apps/v1
2 kind: Deployment
3 metadata:
4 name: ingress-nginx-deployment
5 labels:
6 app: ingress-nginx
7 spec:
8 replicas: 2
9 selector:
10 matchLabels:
11 app: ingress-nginx
12 template:
13 metadata:
14 labels:
15 app: ingress-nginx
16 spec:
17 containers:
18 - name: nginx
19 image: hub.baidubce.com/cce/nginx-ingress
20 ports:
21 - containerPort: 80
22 ---
23 kind: Service
24 apiVersion: v1
25 metadata:
26 name: hello-service
27 spec:
28 selector:
29 app: ingress-nginx
30 type: NodePort
31 ports:
32 - protocol: TCP
33 port: 8000
34 targetPort: 80
35 ---
36 kind: Service
37 apiVersion: v1
38 metadata:
39 name: world-service
40 spec:
41 selector:
42 app: ingress-nginx
43 type: NodePort
44 ports:
45 - protocol: TCP
46 port: 9000
47 targetPort: 80- Create an ingress resource and configure the following forwarding rules:
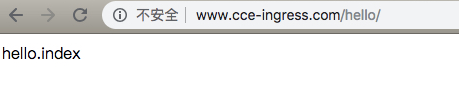
- www.cce-ingress.com/hello/* -> hello-service:8000/hello/
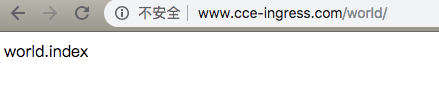
- www.cce-ingress.com/world/* -> world-service:9000/world/
Note:
- The backend service corresponding to the service must support the forwarding policy URI. To ensure compatibility in all scenarios, set it to /*.
- Modify the local /etc/hosts to point www.cce-ingress.com to the EIP (e.g., 106.12.52.80):
- Access test: