Using NetworkPolicy Network Policy
Updated at:2025-10-27
The Network Policy feature in Kubernetes defines pod-specific network isolation policies with custom rules for pod-to-pod communication. This guide explains enabling Network Policy in a K8S CCE cluster and offers common configuration examples.
Preparation description
- Only CCE standard independent clusters and managed clusters are supported. Enabling network policy may impact cluster network performance to some degree.
- Network Policy relies on network plugins for implementation, with varying behaviors across different network configurations. When eBPF enhancement is not enabled for cluster, the Network Policy plugin is implemented by Calico-felix (only supporting veth network mode). When eBPF enhancement is enabled for cluster, the Network Policy plugin is implemented by Cilium (only supporting veth network mode). For Network Policy plugin behavior, please refer to the community document. It is recommended to thoroughly understand and verify before enabling Network Policy.
Operation steps
Enable Network Policy when creating a cluster
- Sign in to the Cloud Container Engine Consoleand select Cluster List from the navigation bar at the left side.
- On the "Cluster List" page, click Create to enter the cluster creation page.
- In the "Network Configuration" of the "Create Cluster" page, select Enable Network Policy Support to configure.
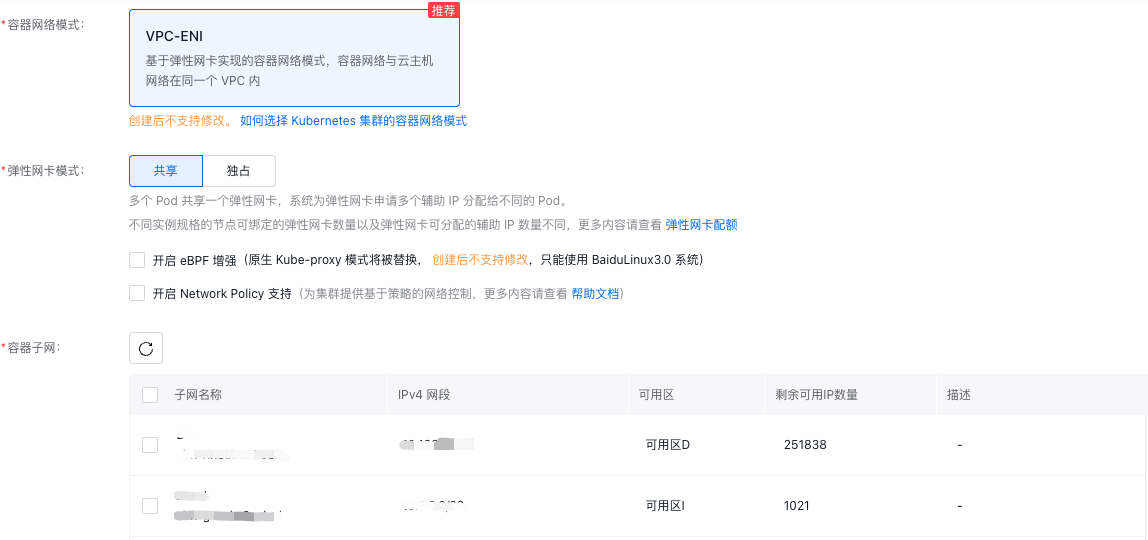
Note
Checking the box of supporting Network Policy cluster will support policy-based network control by default (if eBPF enhancement is not checked, Network Policy plugin is implemented by Calico-felix; if eBPF enhancement is checked, network plugin is implemented by Cilium)
Network Policy configuration examples
Example
- Deny access to pods within the staging namespace.
Plain Text
1 apiVersion: networking.k8s.io/v1
2 kind: NetworkPolicy
3 metadata:
4 name: default-deny
5 namespace: staging
6 spec:
7 podSelector: {}
8 policyTypes:
9 - Ingress- Permit access to pods within the staging namespace.
Plain Text
1 apiVersion: networking.k8s.io/v1
2 kind: NetworkPolicy
3 metadata:
4 name: allow-all
5 namespace: staging
6 spec:
7 podSelector: {}
8 ingress:
9 - {}
10 policyTypes:
11 - Ingress- Block outbound traffic from pods in the production namespace.
Plain Text
1 apiVersion: networking.k8s.io/v1
2 kind: NetworkPolicy
3 metadata:
4 name: default-deny
5 namespace: production
6 spec:
7 podSelector: {}
8 policyTypes:
9 - Egress- Allow outbound traffic from pods in the production namespace.
Plain Text
1 apiVersion: networking.k8s.io/v1
2 kind: NetworkPolicy
3 metadata:
4 name: allow-all
5 namespace: production
6 spec:
7 podSelector: {}
8 egress:
9 - {}
10 policyTypes:
11 - Egress- Restrict all inbound and outbound traffic for all pods.
Plain Text
1 apiVersion: networking.k8s.io/v1
2 kind: NetworkPolicy
3 metadata:
4 name: default-deny
5 spec:
6 podSelector: {}
7 policyTypes:
8 - Ingress
9 - EgressSemantic description
| Parameters | Description |
|---|---|
| PodSelector | Check the pod to be isolated |
| policyTypes | Define the policy type. NetworkPolicy distinguishes traffic as ingress (inbound) or egress (outbound). If left unspecified, no restrictions will be applied. |
| ingress | Defines an allow list for inbound traffic. Requires specifying from (traffic source) and ports (destination locations). from supports three types: ipBlock, namespaceSelector, and podSelector |
| egress | Defines an allow list for outbound traffic. Similar to ingress, egress requires specifying to (traffic destination) and ports (destination locations) |
