Configure Predefined RBAC Permission Policy
CCE provides a Kubernetes RBAC-integrated authorization model, enabling fine-grained access control for IAM users. This guide explains how to configure RBAC permissions for IAM users to manage permissions over the K8S Cluster CCE and namespaces.
Announcement
K8S Cluster CCE service has upgraded the RBAC cluster permission management system:
- Restrict IAM users who have not completed RBAC permission authorization from accessing cluster resources. Please contact the root account promptly to complete the RBAC authorization process to avoid any disruptions in production.
- IAM users will only retain the cluster access permissions explicitly granted to them; their original default access permissions will be removed.
Authorization instructions
-
Only the following accounts/users/roles can be provided with cluster RBAC permissions:
- Root account for Baidu AI Cloud
- IAM users or IAM roles with RBAC management permissions for specified clusters, and holding either the IAMReadOnlyAccessPolicy or IAMFullControlAccessPolicy.
- IAM users and IAM roles are granted administrative permissions by default for the clusters they create.
Prerequisites
- A cluster has been created. For specific operations, please refer to Create Cluster
- IAM users have completed the relevant permission configuration on the CCE side. For detailed operations, please refer to Configuring IAM Preset Permission Policies and Configuring IAM Custom Permission Policies.
- An IAM role has been created. For detailed operations, refer to Create Role.
Permission
CCE includes three levels of RBAC permissions, as follows:
| Permissions | Permission |
|---|---|
| Administrator | All operational permissions for the cluster |
| Operation and maintenance & development | With read-write permissions for resources under the namespace, and read-only permissions for nodes, namespaces, persistent volumes, and storage classes |
| Read-only | With read-only permissions for resources under the namespace only |
Configure RBAC authorization for IAM users
- Log in to the Baidu AI Cloud Management Console, go to Products & Services > Cloud Container Engine (CCE), then click on Cluster Management > Permission Management in the left navigation bar to open the Permission Management page.
- Select the IAM user to authorize from the IAM user list, click RBAC Authorization, and enter the RBAC Authorization page.
-
Click Authorize at the top left of the RBAC authorization list to pop up the Authorize configuration dialog. Select the permissions to be configured, as well as the corresponding cluster and namespace.
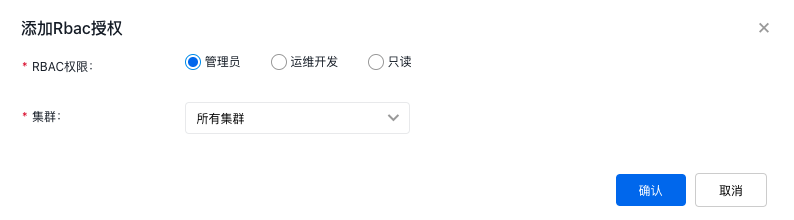
Description
- If no CCE permissions are granted to an IAM user in IAM, the authorization will not take effect.
- When "All Clusters" is selected as the scope, it only includes the clusters currently created. Any newly created clusters will require additional authorization.
- Once authorization is successful, you can view the authorization list.
Configure RBAC authorization for IAM roles
- Log in to the Baidu AI Cloud Management Console, navigate to Products & Services > Cloud Container Engine (CCE), then click on Cluster Management > Permission Management in the left navigation bar to access the IAM Role Tab page.
- Enter the name of the IAM role to which RBAC permissions need to be granted, then click on Manage Role Permissions.
- On the Role Permission Management page, click Authorize in the upper-left corner to open the authorization configuration dialog. Select the necessary permissions along with the corresponding cluster and namespace.
- Click OK to finalize the RBAC permission settings for the IAM role.
FAQ
As an IAM user, what prerequisites are required to grant role ggg RBAC administrator permissions for K8S Cluster CCE A and K8S Cluster CCE B?
- The current IAM user has IAM permissions for target Cluster A and Cluster B
- The current RBAC user has administrator permissions for target Cluster A and Cluster B
- The current IAM user has IAMReadOnlyAccessPolicy or IAMFullControlAccessPolicy permissions
