CCE Credential Controller Description
Updated at:2025-10-27
Prerequisites
- Create an enterprise instance of Cloud Container Registry (CCR). For specific operations, please refer to Create Enterprise Instance.
- Configure the virtual private cloud where the K8S Cluster CCE is located to the CCR enterprise instance. For querying the virtual private cloud of the K8S Cluster CCE, please refer to View Cluster. For configuring virtual private cloud access for the CCR enterprise instance, please refer to Configure Virtual Private Cloud Access.
Component introduction
The CCE Credential Controller component provides the ability to pull container images from the CCR enterprise instance in the K8S Cluster CCE without requiring passwords.
- Upon installing the password-free component in the K8S Cluster CCE, the system will automatically generate image access credentials for the CCR enterprise instance, associating them with the namespaces and ServiceAccounts where the component is active.
- When creating workloads with ServiceAccounts in namespaces where the password-free component is active, ImagePullSecret will automatically be set up by default to pull images from the CCR enterprise instance, enabling the use of CCR images without manually configuring repository secrets.
Application scenarios
- According to K8S specifications, when deploying workloads using private images, it is necessary to configure access credentials for the private images for the workloads. For more information about using private images in K8S Cluster CCE, please refer to Pull Images from Private Repositories.
- After installing the password-free component in the K8S Cluster CCE, image access credentials for the CCR enterprise instance are automatically created. Users do not need to explicitly configure ImagePullSecret while creating workloads and can pull private images via the intranet from the CCR enterprise instance, simplifying image configuration and enhancing service deployment efficiency in the K8S Cluster CCE.
Limitations
- Only virtual private cloud domain names of CCR instances are supported for password-free pull, while public domain names do not support password-free pull.
- Only Kubernetes clusters version 1.18 and above are supported, and clusters with an ARM architecture are not supported.
- The Cloud Container Registry (CCR) is unavailable in the Nanjing region, so the password-free component cannot be used in the K8S Cluster CCE located there.
Note
- Component Installation: During the password-free component installation, several resource objects will be created in the K8S Cluster CCE. Ensure you use a user with K8S Cluster CCE management permissions to perform the installation.
- Component Configuration: In the cluster's kube-system namespace, the password-free component associates ImagePullSecret only with the ServiceAccount named "default" by default. To enable password-free access for other ServiceAccounts in the kube-system namespace, you need to manually specify those ServiceAccounts.
- Component operation: After configuring the password-free component, do not manually configure ImagePullSecret when submitting workloads. Manual configuration will overwrite the default ImagePullSecret, failing to pull images from the CCR instance using automatic access credentials.
- Component uninstallation: After uninstalling the password-free component, the originally automatically-configured ImagePullSecret will expire within 24 h, and existing associated workloads will no longer be able to pull images from CCR without passwords.
Install component
- Sign in to the Baidu AI Cloud official website, enter the management console, navigate to Cloud Container Engine (CCE) > Cluster Management > Cluster List > Component Management, and switch to the Image tab; in the component management list, select the CCE Credential Controller component and click Install.
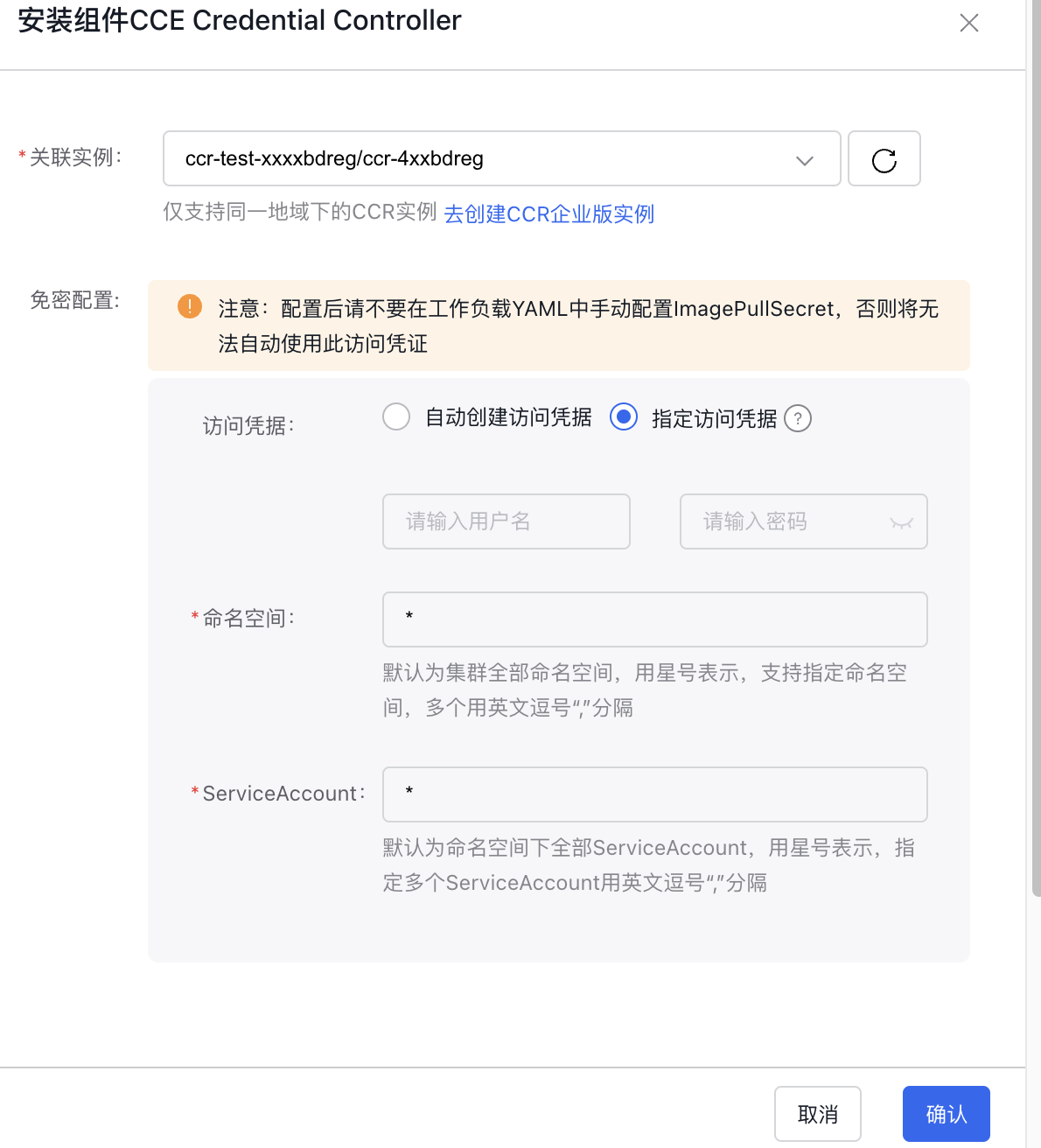
- Fill in the component installation parameters:
- Associated instance: The CCR instance to be associated only supports CCR instances in the same region. If no CCR instance has been created, click Create CCR Enterprise Instance.
-
Access credentials
- Automatically create access credentials: The password-free component automatically obtains the temporary password of the CCR instance and creates ImagePullSecret. It also supports automatically updating the temporary password before expiration to ensure the validity of ImagePullSecret.
- Specify access credentials: You need to provide the fixed username and password for accessing the associated CCR instance (Note: This username and password refer to the ones configured in the CCR console for docker login, not the login credentials of Baidu AI Cloud account). The password-free component will use this username and password to configure image access credentials. Due to the inability to verify validity and automatically update fixed passwords, please ensure that the user password and access credentials remain valid; otherwise, images cannot be pulled.
- Automatically create access credentials: The password-free component automatically obtains the temporary password of the CCR instance and creates ImagePullSecret. It also supports automatically updating the temporary password before expiration to ensure the validity of ImagePullSecret.
- Namespace: The namespaces where the password-free component is active. By default, "*" signifies that it applies to all namespaces. You can specify multiple namespaces separated by commas.
- ServiceAccount: The ServiceAccounts where the password-free component takes effect. The default * indicates that all are effective. Specify multiple ServiceAccounts separated by commas.
- Click on the "Install" button and wait until the component is successfully installed.
Submit workloads using the password-free component
After the password-free component is successfully installed, image access credentials for the CCR instance will be automatically injected when creating workloads using ServiceAccounts in the active namespaces.
- Note: If neither ImagePullSecret nor ServiceAccount is explicitly specified in a workload, Kubernetes will attempt to fetch a matching ImagePullSecret from the default ServiceAccount within the current namespace.
Deployment status
For installing the CCE Credential Controller component, the following objects will be deployed in the K8S Cluster CCE
| Object name | Belonging to namespace | Resource usage | Types |
|---|---|---|---|
| cce-credential-controller | kube-system | cpu:500m memory: 500Mi |
Deployment |
| cce-credential-controller | kube-system | - | ServiceAccount |
| cce-credential-controller | kube-system | - | Secret |
| cce-credential-controller | kube-system | - | ConfigMap |
| f0ec2fe2.baidubce.com | kube-system | - | ConfigMap |
| cce-credential-controller | kube-system | - | Service |
| cce-credential-controller | kube-system | - | MutatingWebhookConfiguration |
| cce-credential-controller | - | - | ClusterRole |
| cce-credential-controller | - | - | ClusterRoleBinding |
| cce-credential-controller | - | - | CCEImageCredential |
Version records
| Version No. | Cluster version compatibility | Update time | Update content | Impact |
|---|---|---|---|---|
| 1.0.1 | CCE/v1.18+ | 2024.09.10 | First release | - |
