Create CCE_Ingress via YAML
This guide explains how to create and manage CCE ingress using YAML.
This document mainly includes the following content:
- Deploy CCE Ingress Controller
- Create deployment and service
- Create CCE ingress
Note: A CCE ingress can only use one BLB, and a BLB can only be used by one CCE ingress
Deploy CCE Ingress Controller
CCE ingress is implemented with Baidu Cloud's Baidu Load Balancer (BLB), commonly referred to as BLB-type ingress.
Using CCE ingress requires the deployment of the CCE Ingress Controller component within the cluster.
CCE does not preinstall the Ingress Controller for clusters by default. Users can manually install this component from the component management section.
- Navigate to Component Management - Network in the cluster console and locate the
CCE Ingress Controllercomponent.
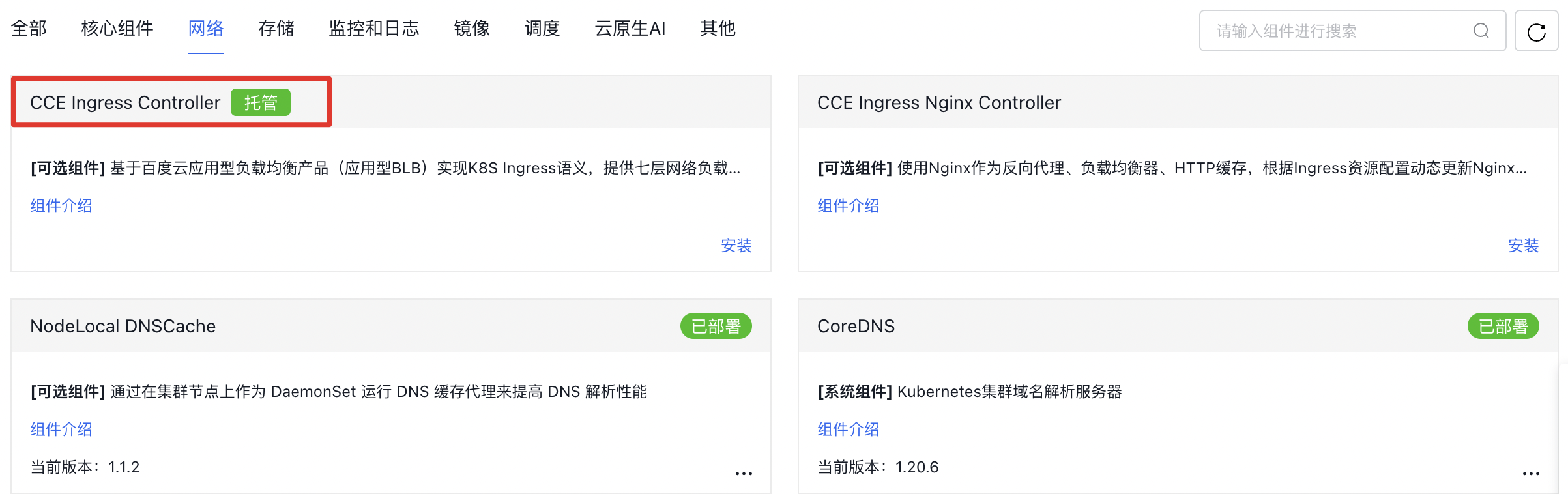
- Click Install and confirm the action.
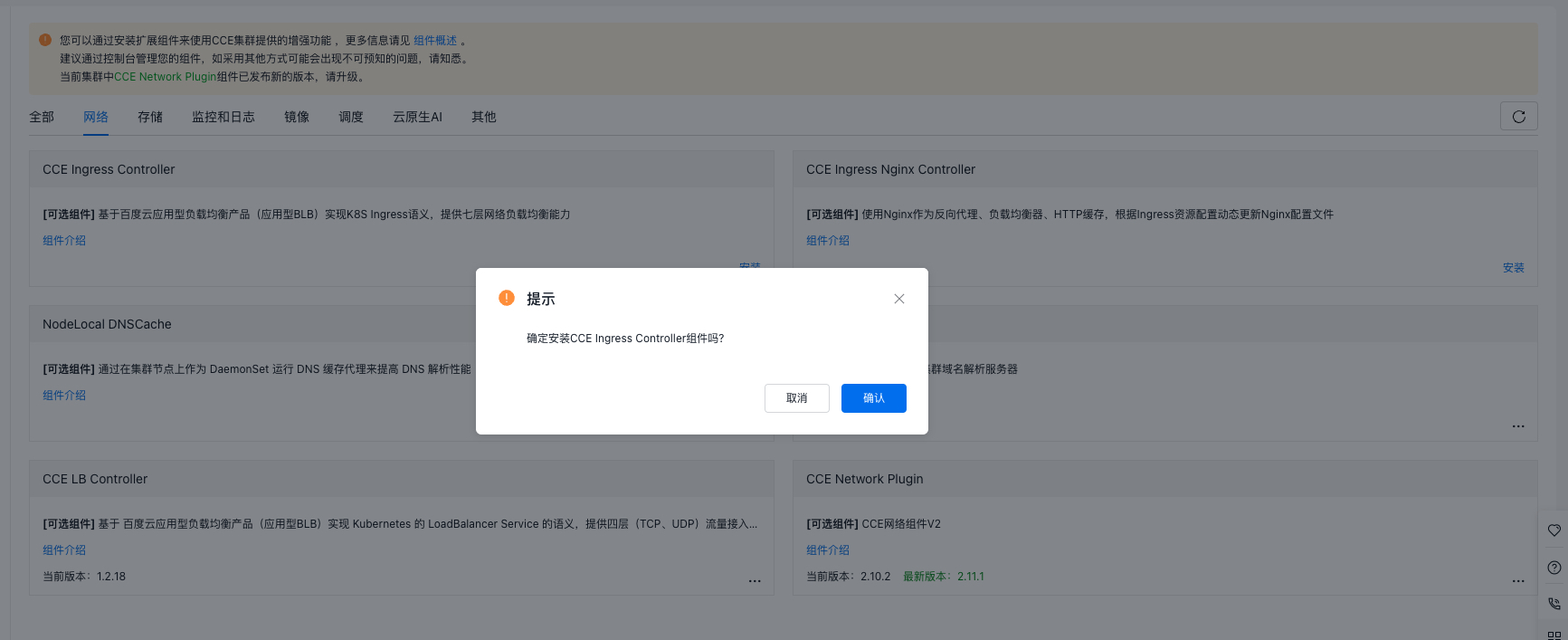
- Wait for the
CCE Ingress Controllercomponent to display Current Version, indicating successful installation.
Create deployment and service examples
1apiVersion: apps/v1
2kind: Deployment
3metadata:
4 name: ingress-nginx-deployment
5 labels:
6 app: ingress-nginx
7spec:
8 replicas: 2
9 selector:
10 matchLabels:
11 app: ingress-nginx
12 template:
13 metadata:
14 labels:
15 app: ingress-nginx
16 spec:
17 containers:
18 - name: nginx
19 image: hub.baidubce.com/cce/nginx-ingress
20 ports:
21 - containerPort: 80
22---
23kind: Service
24apiVersion: v1
25metadata:
26 name: hello-service
27spec:
28 selector:
29 app: ingress-nginx
30 type: NodePort
31 ports:
32 - protocol: TCP
33 port: 8000
34 targetPort: 80
35---
36kind: Service
37apiVersion: v1
38metadata:
39 name: world-service
40spec:
41 selector:
42 app: ingress-nginx
43 type: NodePort
44 ports:
45 - protocol: TCP
46 port: 9000
47 targetPort: 80Create ingress object
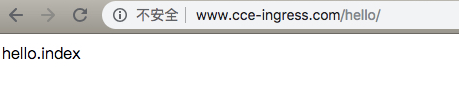
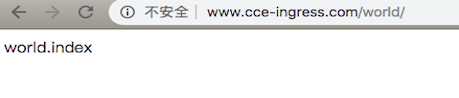
Use the following YAML content to create an ingress object named helloworld and configure ingress forwarding rules:
- www.cce-ingress.com/hello/ -> hello-service:8000/hello/
- www.cce-ingress.com/world/ -> world-service:9000/world/
Ingress can be configured using parameters in ingress annotations, such as specifying BLB or EIP.
The backend service associated with the service must accommodate the forwarding policy URI. To cover all scenarios, it is advised to set it to /*. Be aware that the URI path has stringent requirements here, especially for "/".
1apiVersion: networking.k8s.io/v1
2kind: Ingress
3metadata:
4 annotations:
5 cce.ingress.blb-backup-content: ""
6 kubernetes.io/cce.ingress.blb-cert-id: ""
7 kubernetes.io/cce.ingress.blb-id: ""
8 kubernetes.io/cce.ingress.eip: ""
9 kubernetes.io/cce.ingress.http-redirect: "false"
10 kubernetes.io/cce.ingress.https: "false"
11 kubernetes.io/cce.ingress.internal: "false"
12 kubernetes.io/cce.ingress.timeout-in-seconds: "30"
13 kubernetes.io/cce.ingress.vpc-subnet-id: ""
14 kubernetes.io/ingress.class: cce
15 name: helloworld
16 namespace: default
17spec:
18 rules:
19 - host: www.cce-ingress.com
20 http:
21 paths:
22 - backend:
23 service:
24 name: hello-service
25 port:
26 number: 8000
27 path: /hello/*
28 - backend:
29 service:
30 name: world-service
31 port:
32 number: 9000
33 path: /world/*Below are important points to keep in mind when creating CCE ingress.
Ingress Class
CCE Ingress Controller only processes ingresses with the annotation kubernetes.io/ingress.class: cce. Please ensure the ingress has this annotation.
HTTPS rule configuration
By default, CCE Ingress Controller creates HTTP rules for ingress resources, and will not configure HTTPS rules for them. To configure certain rules as HTTPS, the following annotation should be present:
-
Specify the certificate to be used by the BLB.
Plain Text1kubernetes.io/cce.ingress.blb-cert-id: cert-id -
Explicitly enable HTTPS in the configuration.
Plain Text1kubernetes.io/cce.ingress.https: "true" -
Define the rules for HTTPS usage. If specific rules in the Spec require HTTPS, they must also be included in this annotation.
Plain Text1kubernetes.io/cce.ingress.https-rules: >- 2 [ 3 { "host":"ad.com", 4 "http":{ 5 "paths":[ 6 {"path":"/*","backend":{"serviceName":"service-example","servicePort":80}} 7 ] 8 } 9 } 10 ]
For complete descriptions of annotations, refer to BLB Ingress Annotation Description.
Access test
Modify the local /etc/hosts to point www.cce-ingress.com to the EIP (e.g., 106.12.52.80), and you can view the ingress information in the console or cluster:
1# kubectl get ingress
2NAME HOSTS ADDRESS PORTS AGE
3helloworld www.cce-ingress.com 10.0.3.251,106.12.52.80 80 6m34sAccess test: