Access control
Baidu AI Cloud Object Storage (BOS) offers features such as read-write permissions through ACLs, detailed custom authorization policies, allowlists for anti-hotlinking, and other tools to control and manage access to storage resources.
Read-write permissions
BOS provides ACLs (Access Control Lists) for managing permissions. ACLs are access policies that dictate permissions for buckets and objects. ACLs can be configured when creating a bucket or uploading an object, as well as modified anytime after these operations.
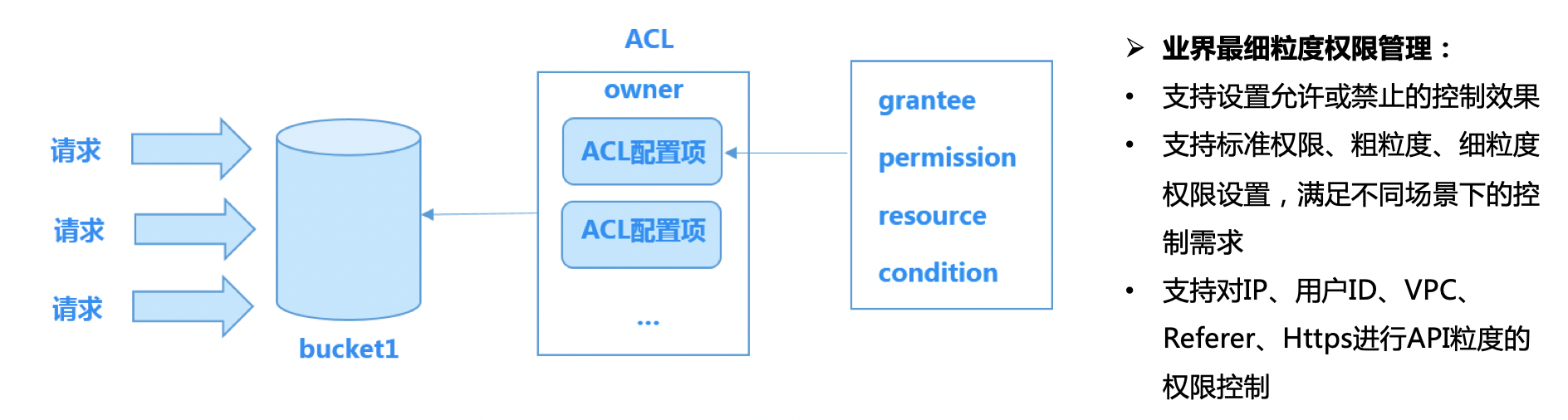
Bucket ACL
Bucket ACL refers to access control permissions at the bucket level. Currently, there are three types of permissions, with the following meanings:
- Bucket standard permission:
The commonly used permission settings in the industry include private, public read, and public read-write.
| Permission name | Permission |
|---|---|
| Private | The bucket creator has full exclusive permission to the bucket. Others cannot write data to or read from the bucket. Suitable for storing confidential files. |
| Public-read | The bucket creator has full exclusive permission to the bucket. Others can read its contents but cannot write data to it. Suitable for storing files requiring public access, such as notifications or advertisements. Note: Enabling this permission allows all internet users to access and read files in the bucket. Please enable it with caution. |
| Public-read-write | Anyone, including the bucket creator, can access and write files. Note: Enabling this permission allows all internet users to read and write files in the bucket. Please enable it with caution. |
When the above simple standard permissions cannot meet your customized permission management needs, you may use the following customized permission management
- Coarse-grained custom permissions: More fine-grained permissions than standard ones allow setting READ, LIST, WRITE, FULL_CONTROL, and MODIFY permissions for specific users, and specifying accessible resources, IP addresses, and referer allow lists. For more information, please refer to Permission Introduction - Coarse-Grained Custom Permission Definition.
- Fine-grained custom permissions: BOS provides API-level fine-grained customized permissions. Configurable API categories include 18 types, such as GetBucket, GetObject, PutObject and DeleteObject. You can customize the corresponding permission for each category. For more information, please refer to Permission Introduction - Fine-Grained Custom Permission Definition.
Object ACL
Object ACL pertains to access control at the object level. Presently, there are two types of permissions, described as follows:
| Permission name | Permission |
|---|---|
| Private | The object owner has both read and write permissions for the object, while all other users are denied access. |
| Public-read | All users have read-only permissions for the object, whereas the object owner retains read and write permissions. |
Details:
- If no specific permissions are set for an object, the object ACL is null and defaults to the bucket's permissions.
- Object ACL overrides bucket ACL. For instance, if an object is set to public-read, it will remain accessible regardless of the bucket's permissions.
- Currently, object ACL authentication applies to four APIs: GetObjectMeta, GetObject, CopyObject, and UploadPartCopy.
For more information, please refer to Object Permission Control.
IAM primary-IAM user access control
Under your Baidu AI Cloud account, you can create IAM users with own AccessKeys via IAM. Your Baidu AI Cloud account is referred to as the root account, and the created accounts are called IAM users. Using the AccessKey of IAM user only allows operations and resources authorized by the root account. BOS has integrated the IAM user system, allowing to create IAM users through the console multi-user access control. The primary user authorizes IAM users by associated policies, which are essentially JSON files. In ACL, permission and resource is used to define permissions and resources. For more details, please refer to IAM Primary-IAM User Access Control.
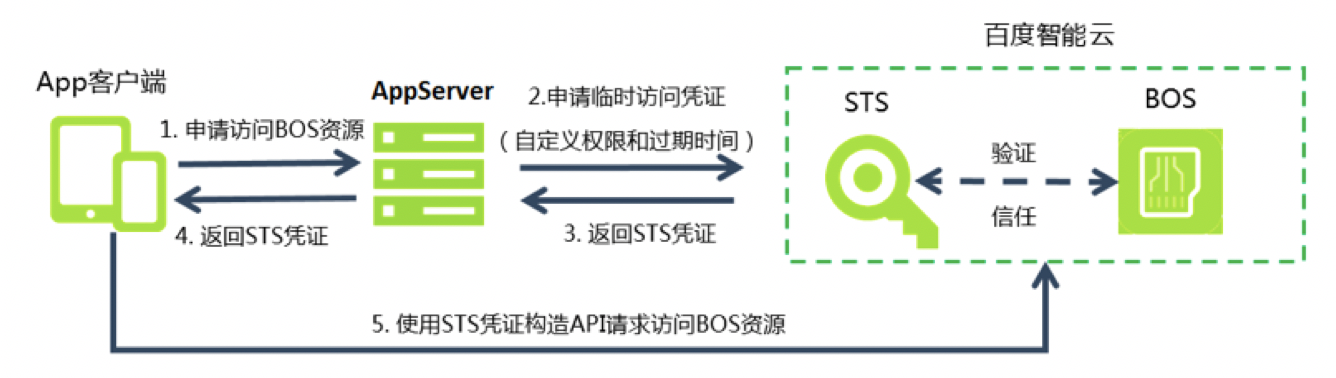
STS temporary authorization
BOS enables temporary third-party access authorization through the STS mechanism. STS (Security Token Service) is a temporary authorization service provided by Baidu AI Cloud. Through STS, you can issue access credentials with customized validity periods and permissions to third-party users. Third-party users can use these credentials to directly call Baidu AI Cloud APIs to access cloud resources. For more information, please refer to Temporary Authorization Access.
Anti-hotlinking allow list
Baidu AI Cloud Object Storage (BOS) charges based on usage. To avoid unauthorized hotlinking of your BOS-stored data and the potential for increased costs, BOS offers anti-hotlinking mechanisms based on the referer field in HTTP/HTTPS headers.
You can configure an anti-hotlinking allow list to restrict BOS resource access to specified domain names or only allow requests with referer fields in HTTP/HTTPS headers. For public read or public read-write buckets, anti-hotlinking allow lists can effectively prevent hotlinking and protect your legal rights. For details, please refer to Set Referer Allow List.
