Data encryption
Baidu AI Cloud Object Storage (BOS) offers both server-side and client-side encryption options, along with HTTPS encrypted transmission via SSL/TLS, effectively minimizing potential security risks for cloud data.
Server-side encryption
BOS provides server-side encryption to secure uploaded data. When data is uploaded, BOS encrypts it before storing it persistently. During downloads, BOS automatically decrypts the stored data and delivers the original content to users while indicating in the HTTP request header that the data underwent server-side encryption.
BOS ensures static data protection through server-side encryption, making it ideal for scenarios demanding high security or compliance in file storage, such as storing deep learning sample files or collaborative document data. BOS offers two server-side encryption options tailored to different needs: BOS-managed keys and KMS-managed keys.
- BOS-managed keys: Choosing this option enables unified encryption for all data uploaded to a bucket using BOS-managed keys. When retrieving data, the system automatically decrypts it, requiring no user intervention for a seamless experience.
- KMS service managed keys: You need to activate Baidu AI Cloud Key Management Service and create self-managed KMS keys. KMS will generate the corresponding Data Keys based on your created KMS master key. Data is automatically encrypted during upload using these Data Keys.
When uploading files, you can configure an encryption method. BOS applies server-side encryption based on the encryption parameters provided. For greater convenience, server-side encryption can be enabled at the bucket level. Once enabled, all new data uploaded to the bucket will be encrypted by default.
For more information, please refer to Server-Side Encryption in the BOS Operation Guide.
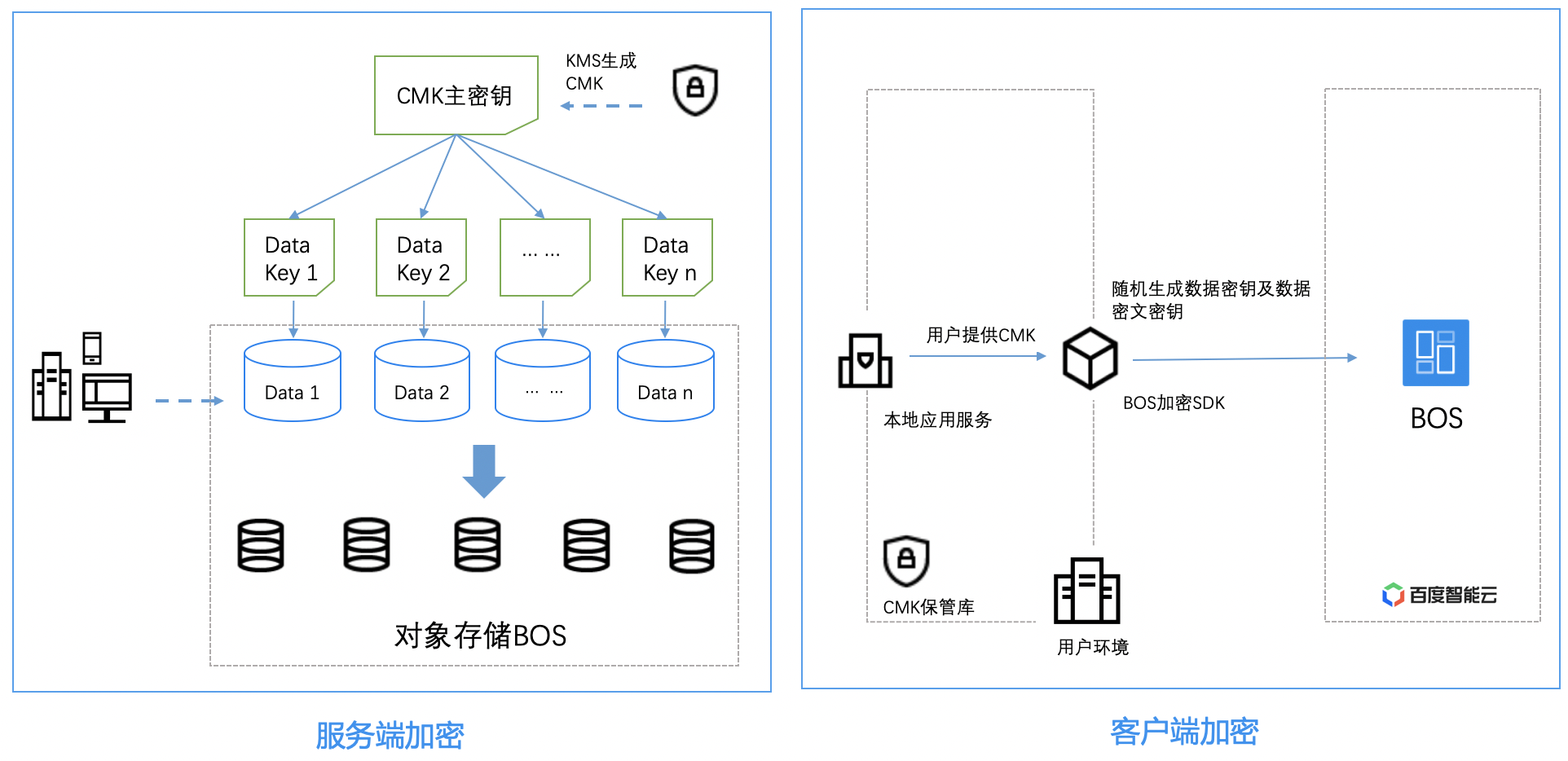
Client-side encryption
Client-side encryption involves encrypting files (objects) locally before uploading them to Baidu AI Cloud Object Storage (BOS). With this method, BOS handles the processes of uploading, storing, and downloading files but does not participate in encryption or decryption. The user retains the plaintext key locally, ensuring enhanced file security. Even if the file is leaked, it cannot be decrypted without the key. However, users must safeguard their keys, as losing the plaintext key makes file recovery impossible. Ensure the master key's integrity and accuracy.
With client-side encryption, a random data encryption key is generated for each object, which is then used to symmetrically encrypt the object's data in plaintext. The master key is used to generate random data encryption keys, and the encrypted content will be stored as object metadata on the server. During decryption, first decrypt the encrypted random key using the master key, and then decrypt the object data using the decrypted random data encryption key. The master key is only used to local client-side computations and is neither transmitted over the network nor stored on the server, to ensure the data security of the master key. We provide you with Client-Side Encryption best practices for your reference.
HTTPS encrypted transmission based on SSL/TLS
BOS is accessible via HTTP or HTTPS. You can also set to permit only HTTPS (TLS) access to BOS resources in the granular Access Control in buckets, to ensure more secure data transmission. The Transport Layer Security (TLS) protocol provides confidentiality and data integrity between two communicating applications. For more details, please refer to HTTPS Transmission Encryption Practices.
