Identity and Access Management
Introduction
The RDS Identity and Access Management (IAM) refers to the operation privileges assigned by the original user as the master account of the sub-account for assigning relevant products or instances to the sub-account, making possible the granular privilege management. For example, you can assign the front-line operators (like DBA) product- or instance-level RDS OPS privileges, and others (except operators) product- or instance-level RDS view privileges.
The IAM is suitable for the following scenarios:
- Medium- and large-sized enterprises: Grant multiple employees the authorization for management in the enterprise;
- Technology-based vendors or SAAS platform providers: Perform resource management and access control for proxy customers;
- Small and medium developers or small-sized enterprises: Add project members or collaborators to perform resource management.
Create an IAM user
- After the primary account user logs in to the account, the user selects the "Identity and Access Management" in the console to enter the user administration page.
- Click "User Management" in the left Navbar, and click "Create IAM user" on the "IAM user" page.
- In the pop-up "New User" dialog box, enter and confirm the "User Name", and then return to the "IAM user Administration List" area to view the created IAM user.
Configuration policies
The RDS supports both the system policies and user-defined policies to realize product-level and instance-level privilege control of the RDS respectively.
System Policies
The system policy is the RDS product-level privilege. The RDS has three system policies, i.e., product-level management privilege, product-level OPS privilege, and product-level read-only privilege. The scope of the privilege is as follows:
| Privilege | Privilege Scope |
|---|---|
| RDS product-level management privilege. | RDS Instance's all operation privileges: |
| RDS product-level OPS privileges. | Includes the privileges for access to and operation of the RDS instances under all master accounts, but excludes the privileges for creating master instances/read-only instances/proxy instances, cloning an instance, changing the configuration, topping-up, tagging, changing billing mode, and releasing an instance. |
| RDS product-level read-only privilege. | Includes privileges for viewing the RDS instance lists, and for viewing, monitoring, and logging the instance details, and excludes operation privileges. |
Custom policies
The IAM user can add a custom policy to achieve instance-level access control by clicking "Policy Management > Create Policy". The custom policies can be added in two ways, namely, "Create by Policy Generator" and "Create by Tag". The user can set and modify the policy content according to specific privileges.
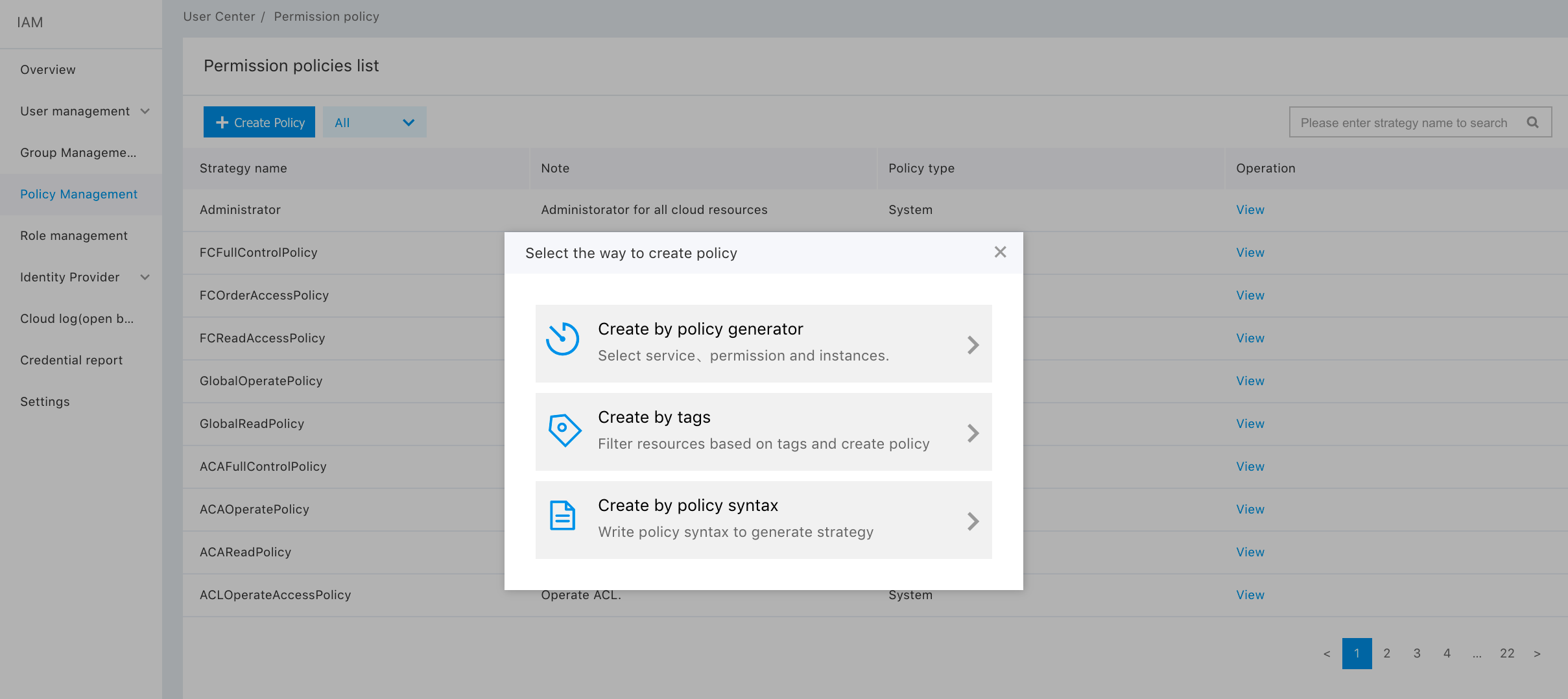
- Create by policy generator: after selecting "Create by Policy Generator", the user can carry out privilege configuration by clicking "Add Privilege" on the page.
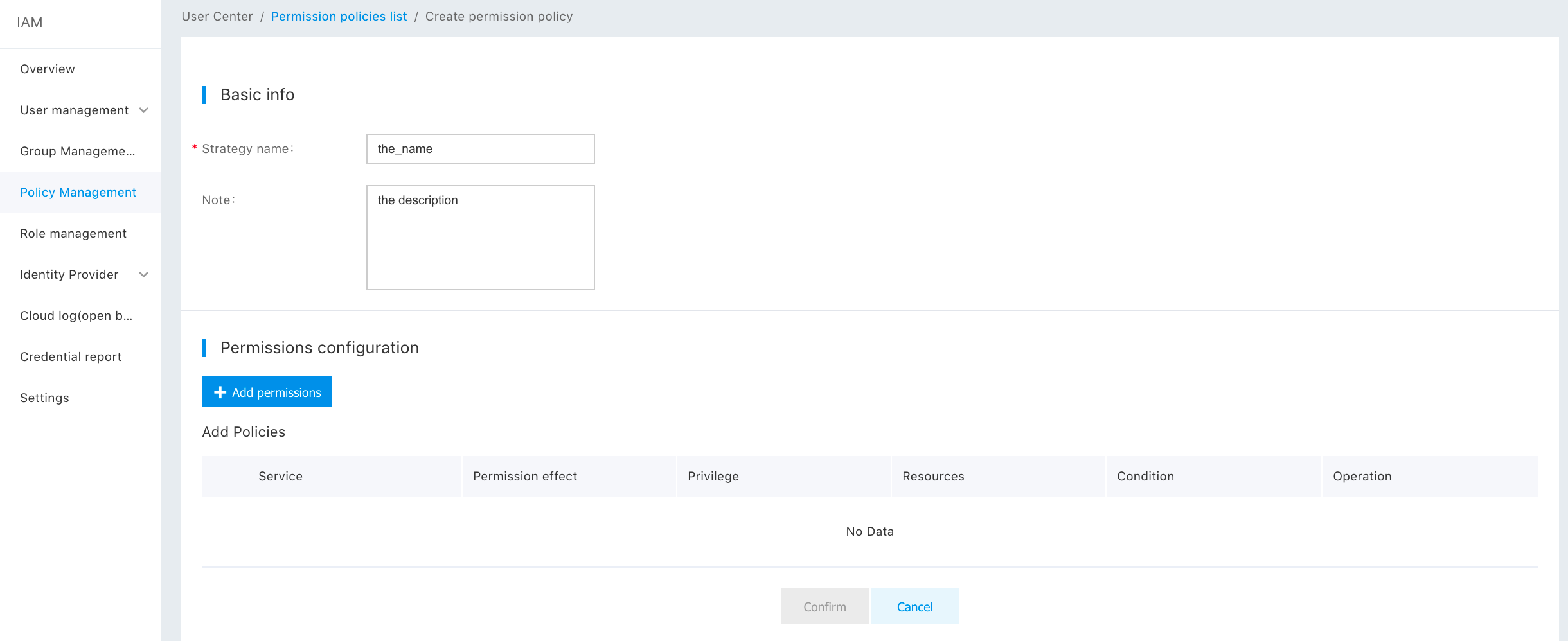
In the pop-up window, select the service "RDS", and carry out privilege configuration by "Policy Generator" and "Edit Policy File". (1) When selecting "Policy Generator", the user can select privilege effectiveness and instance operation, in addition to adding custom policy by configuring the resource zone. After clicking "Finish", the created policy appears in the custom policy list.
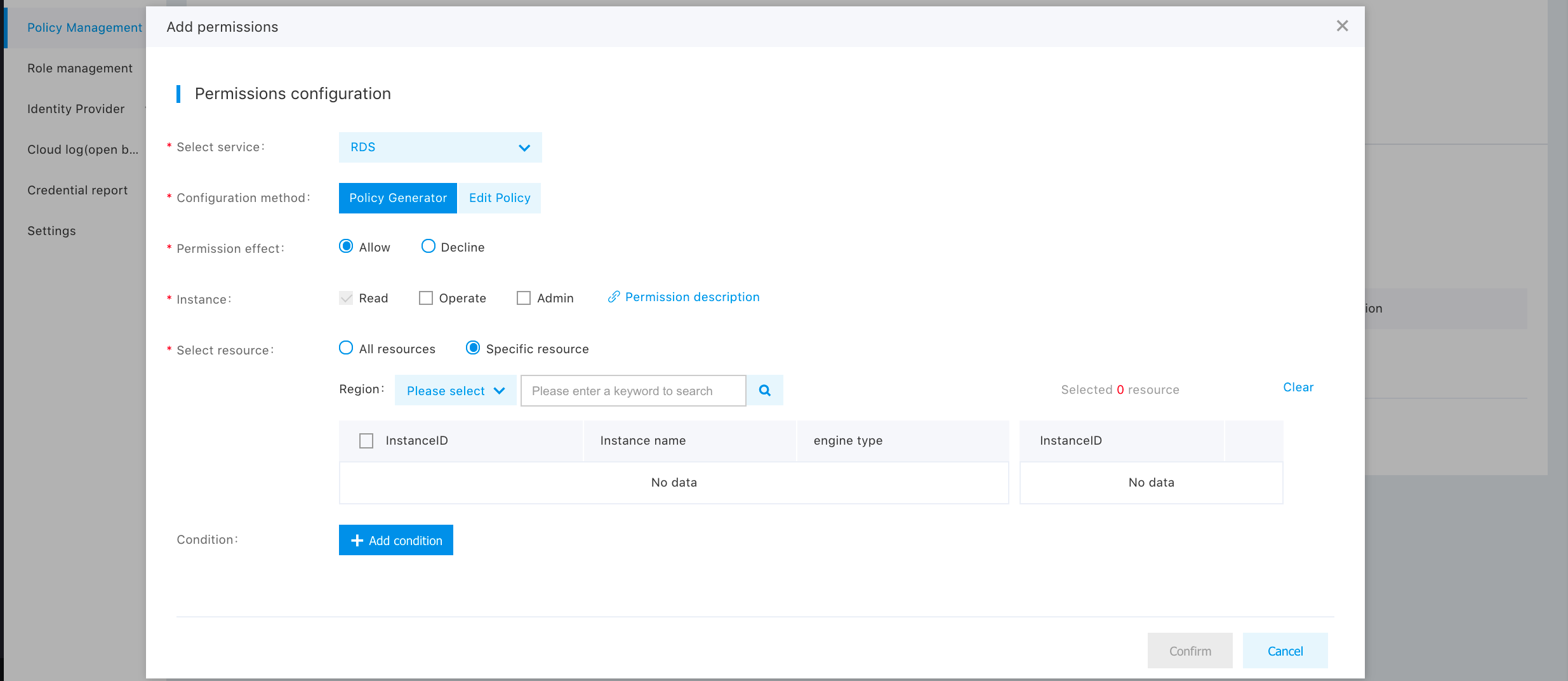
(2) When selecting "Edit Policy File" ,the user can add custom policy by editing the policy file. The policy file, in essence, is a JSON file, and both the system policy and the user-defined policy are mapped into a JSON string of ACL in the end.
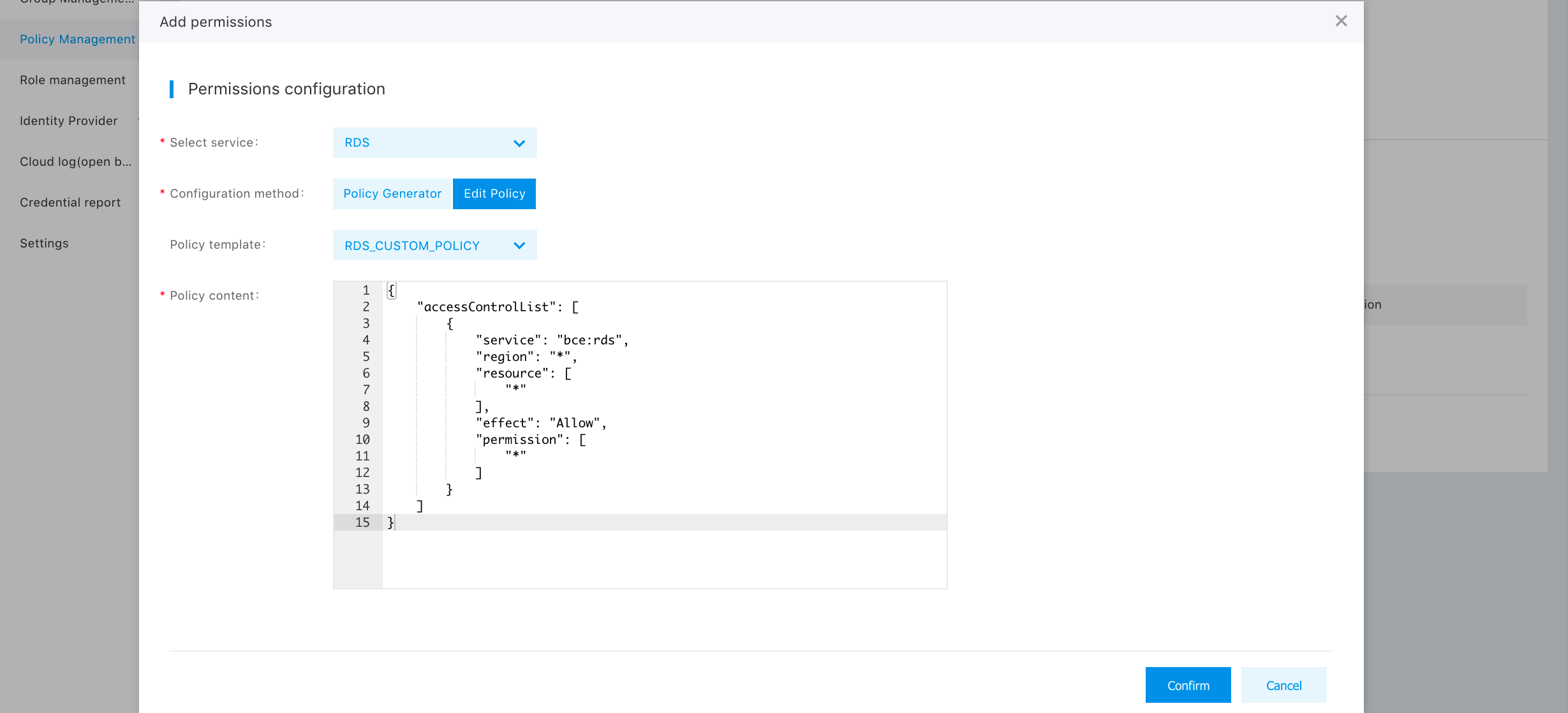
With the ACL policy configuration file, users can define a privilege policy very flexibly but need to understand the meaning of ACL strings. For the syntax used in editing ACL privilege policy, see the documentation [Policy Syntax]. Permission and resource in the file are used to define the privileges and resources.
Implications of fields specified in the policy file are as follows:
| Field | Data Type | Note | Required? | Father node |
|---|---|---|---|---|
| accessControlList | list | The initial part of identity "acl" is composed of one or multiple groups of "acl" configuration items, of which, "acl" configuration item is composed of "service+region+effect+permission+resource". | Yes | No |
| +service | string | Service component influenced by "acl" configuration item, and cloud database RDS is set as "bce:rds"。 | Yes | accessControlList |
| region | string | Regions influenced by acl configuration item, with value range including "bj", "gz", "su", "hk” and "?". Herein, "bj" denotes the Beijing region," gz" denotes the Guangzhjou region, "su" denotes the Suzhou region, "h" denotes Hong Kong region,and "?" denotes all regions. You should write the value in the quotation marks, and must use English punctuation marks. | Yes | accessControlList |
| +effect | string | Specify if Request, which matches current "acl" configuration item, can be performed, and the value is "Allow" or "Deny" 。" "Allow" denotes "Yes" and "Deny" denotes "No". | Yes | accessControlList |
| +permission | list | Privilege influenced by ACL configuration item, and the value is "READ" and asterisk wildcard "?". READ denotes read-only privilege, and "?" denotes OPS privilege. | Yes | accessControlList |
| +resource | list | Resources influenced by ACL configuration item, supporting asterisk wildcard "?"and specific instance ID. "?" represents all instances, and multiple instance IDs can be configured, with the values written within English quotation marks, and separated by English comma. | No | accessControlList |
- Create by Tag
IAM user configure policies using "Create by Tab"
The RDS custom instance-level privilege scope is explained as follows:
| Privilege | Privilege Scope |
|---|---|
| RDS instance-level management privilege. | Includes all operation privileges for the RDS instances (excluding created master instances): |
| RDS instance-level OPS privilege. | Includes all operation privileges of the selected RDS instances (including correlated read-only and proxy instances), and excludes the privileges for creating master/read-only/proxy instances, and for cloning instances, changing configuration, topping-up, tagging, changing billing modes, and releasing instances. |
| RDS instance-level read-only privilege. | Includes the privileges for viewing, monitoring, and logging the selected RDS instances (including correlated read-only and proxy instances) |
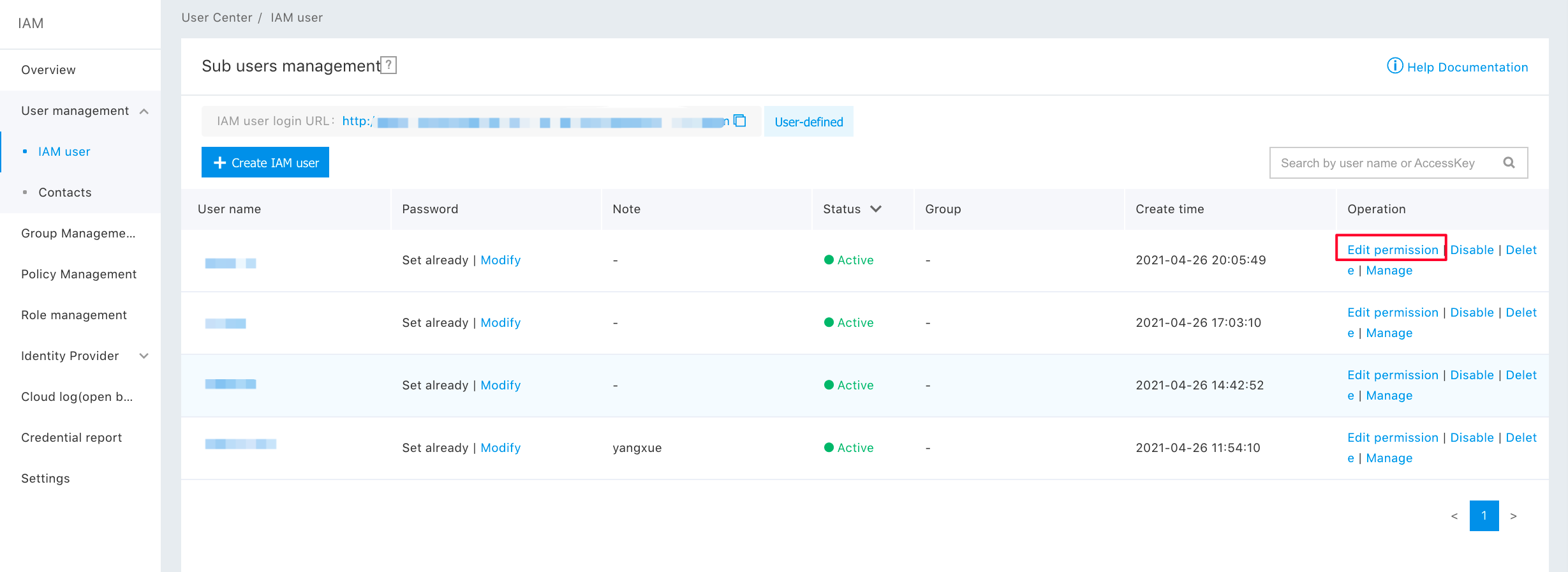
User Authorization
Select "Add Privilege" in the "Action" bar of the corresponding IAM user of "User Management -> IAM user".
In this pop-up window, select "All Policies", "System Policies", or "Custom Policies" for user authorization.
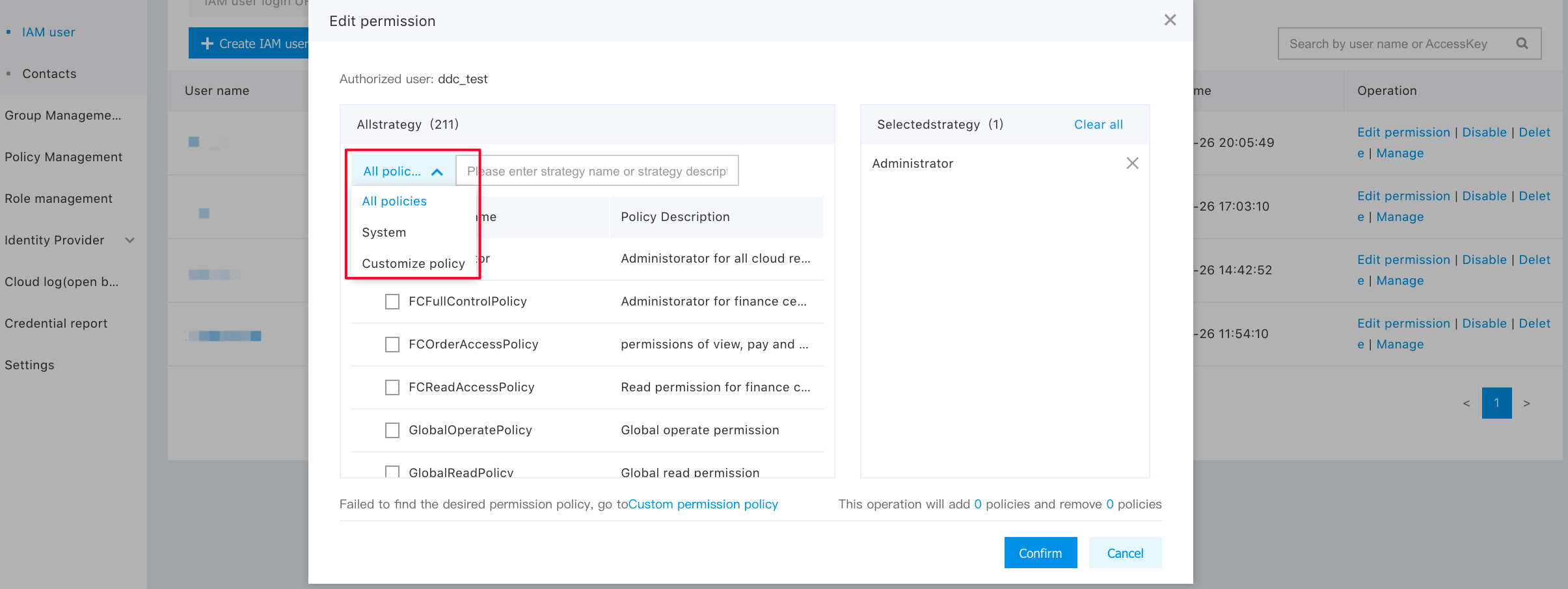
Note: If you modify the privilege of an IAM user without the existing policy rules modified, you can only delete the existing policy and add a policy. But, you cannot unselect the added privilege policy.
IAM user Login
After the primary account has authorized the IAM user, the link can be sent to the IAM user. Thus, the IAM user can log in to the management console of the primary account through the user login link, and operate and view the primary account resources based on the authorized policy.
For more information on detailed operations, please see Identity and Access Management.
