Using Keepalived in VPC to Achieve High-Availability Architecture
Overview
Keepalived is used to monitor server status and is commonly utilized to establish high-availability services, such as Nginx and MySQL.
Requirement scenarios
If the active server fails and is unable to provide services, the secondary IP address is dynamically switched to the standby server, ensuring uninterrupted service provision.
Solution overview
Typically, a high-availability active-standby cluster comprises two servers: one active server that is operational (Active status) for a specific service, and one standby server in a passive state (standby status). The active server holds a secondary IP address, which is released in case of a failure, allowing the standby server to bind the address and continue providing the service.
Example case:
Three cloud hosts are required: two for active and standby roles, and one for traffic testing. The secondary IP address for the elastic network interface is 172.16.0.100.
| Hostname | Virtual machine ID | Network interface card ID | Intranet IP | Role |
|---|---|---|---|---|
| VM1 | i-U63mWIg9 | eni-jdbx8ddgpsz1 | 172.16.0.202 | Active |
| VM2 | i-jW72IAK8 | eni-1jvkdmai1iu1 | 172.16.0.203 | Standby |
| VM3 | i-Y99AbvOF | eni-h5242i8788v0 | 172.16.0.201 | Test machine |
Configuration steps
-
Install Keepalived on both the active and standby servers using the yum package manager.
yum install keepalived -y
-
Configure default preemption settings and create a script to monitor the service. The Keepalived check script located at /tmp/check_status.sh is as follows:
#!/bin/sh if [ ! -f /tmp/down ]; then exit 1 fi exit 0
How to Obtain AKSK
Generate a POST token file post_sign.py
Generate a DELETE token file delete_sign.py
The address switching script changed_ip.sh is as follows:
1#!/bin/bash
2
3STATUS=$1
4MASTERENI=$2
5BACKUPENI=$3
6IP=$4
7
8set_master_eni_ip()
9{
10 TOKEN=`cat /proc/sys/kernel/random/uuid`
11 SIGN=`python /root/post_sign.py $MASTERENI $TOKEN`
12 curl -H "Host:bcc.bj.baidubce.com" -H "Content-Type:application/json;charset=UTF-8" -H "Authorization:$SIGN" -X POST --data '{"privateIpAddress":"'$IP'"}' "http://bcc.bj.baidubce.com/v1/eni/$MASTERENI/privateIp?clientToken=$TOKEN"
13}
14
15del_backup_eni_ip()
16{
17 TOKEN=`cat /proc/sys/kernel/random/uuid`
18 SIGN=`python /root/delete_sign.py $BACKUPENI $IP $TOKEN`
19 curl -H "Host:bcc.bj.baidubce.com" -H "Content-Type:application/json;charset=UTF-8" -H "Authorization:$SIGN" -X DELETE "http://bcc.bj.baidubce.com/v1/eni/$BACKUPENI/privateIp/$IP?clientToken=$TOKEN"
20}
21
22case "$1" in
23 master)
24 del_backup_eni_ip
25 set_master_eni_ip
26 ;;
27 backup)
28 ;;
29esacNote: changed_ip.sh $role $master_eni $backup_eni $ip
- role: The role to switch to; currently, the script only implements master
- master_eni: The network interface card requiring additional IP addresses
- backup_eni: The network interface card from which the IP needs to be removed
- ip: IP to be modified, typically an intranet IP
-
Log in to the active server, navigate to /etc/keepalived/keepalived.conf, and adjust the necessary configurations.
! Configuration File for keepalived
global_defs { notification_email { acassen@firewall.loc failover@firewall.loc sysadmin@firewall.loc } notification_email_from Alexandre.Cassen@firewall.loc smtp_server 192.168.200.1 smtp_connect_timeout 30 router_id LVS_DEVEL vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0 vrrp_gna_interval 0 }
vrrp_instance VI_1 { state MASTER interface eth0 virtual_router_id 51 priority 100 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 172.16.0.100 } unicast_src_ip 172.16.0.202 unicast_peer { 172.16.0.203 } notify_master "/usr/bin/echo master >> /tmp/keep_status;date >> /tmp/keep_status;/root/changed_ip.sh master eni-jdbx8ddgpsz1 eni-1jvkdmai1iu1 172.16.0.100;date >> /tmp/keep_status;" notify_backup "/usr/bin/echo backup >> /tmp/keep_status" notify_fault "/usr/bin/echo fault >> /tmp/keep_status" }
-
Log in to the standby server, navigate to /etc/keepalived/keepalived.conf, and adjust the necessary configurations.
! Configuration File for keepalived
global_defs { notification_email { acassen@firewall.loc failover@firewall.loc sysadmin@firewall.loc } notification_email_from Alexandre.Cassen@firewall.loc smtp_server 192.168.200.1 smtp_connect_timeout 30 router_id LVS_DEVEL vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval 0 vrrp_gna_interval 0 }
vrrp_instance VI_1 { state BACKUP interface eth0 virtual_router_id 51 priority 90 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 172.16.0.100 } unicast_src_ip 172.16.0.203 unicast_peer { 172.16.0.202 } notify_master "/usr/bin/echo master >> /tmp/keep_status;date >> /tmp/keep_status;/root/changed_ip.sh master eni-1jvkdmai1iu1 eni-jdbx8ddgpsz1 172.16.0.100;date >> /tmp/keep_status;" notify_backup "/usr/bin/echo backup >> /tmp/keep_status" notify_fault "/usr/bin/echo fault >> /tmp/keep_status" }
Description
- The firewall may be configured automatically when Keepalived starts, so consider disabling it temporarily to test traffic connectivity.
1iptables -D INPUT 1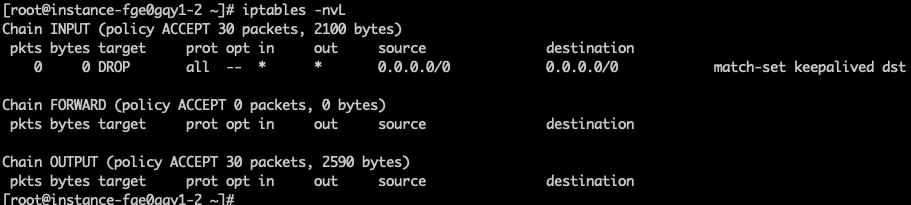
-
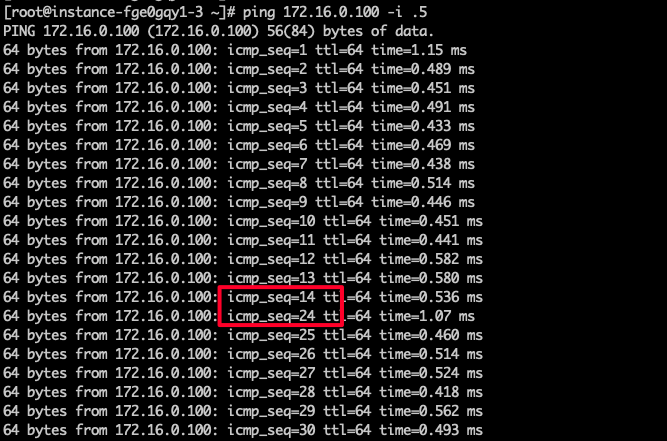
Functional verification: Generate a down file on Cloud Server 1
touch /tmp/down

Deleting this file will cause an automatic failback to the primary server, with a network disruption lasting approximately 5 seconds.