Identity and access management
Introduction
Identity and Access Management helps users manage resource access permissions within cloud accounts. It caters to various enterprise roles by granting different staff levels access to specific product permissions. For enterprises requiring multi-user collaboration for resource operations, using Identity and Access Management is recommended.
It is applicable to the following usage scenarios:
- Medium and large enterprise customers: Authorization management for multiple employees in the enterprise;
- Technology-oriented vendor or SAAS platform provider: Resource and permission management for proxy clients;
- Small and medium-sized developers or small enterprises: Add project members or collaborators for resource management.
Create User
- After logging into the root account, select Identity and Access Management from the console to access the user management page.
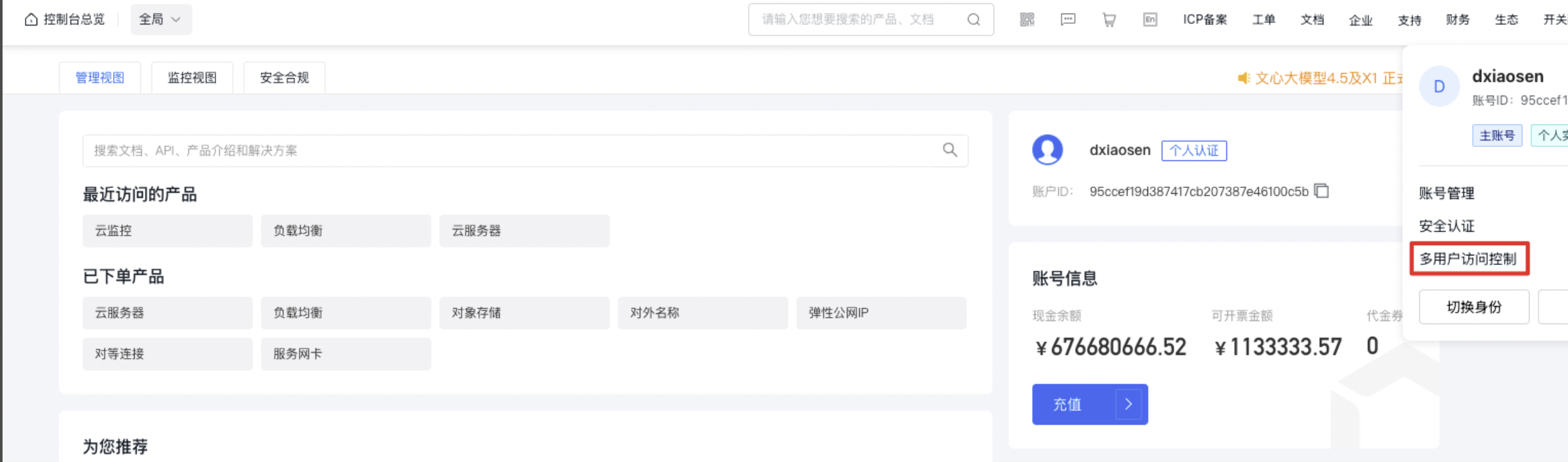
- Access User Management in the left navigation bar, and on the IAM User page, select New IAM User.
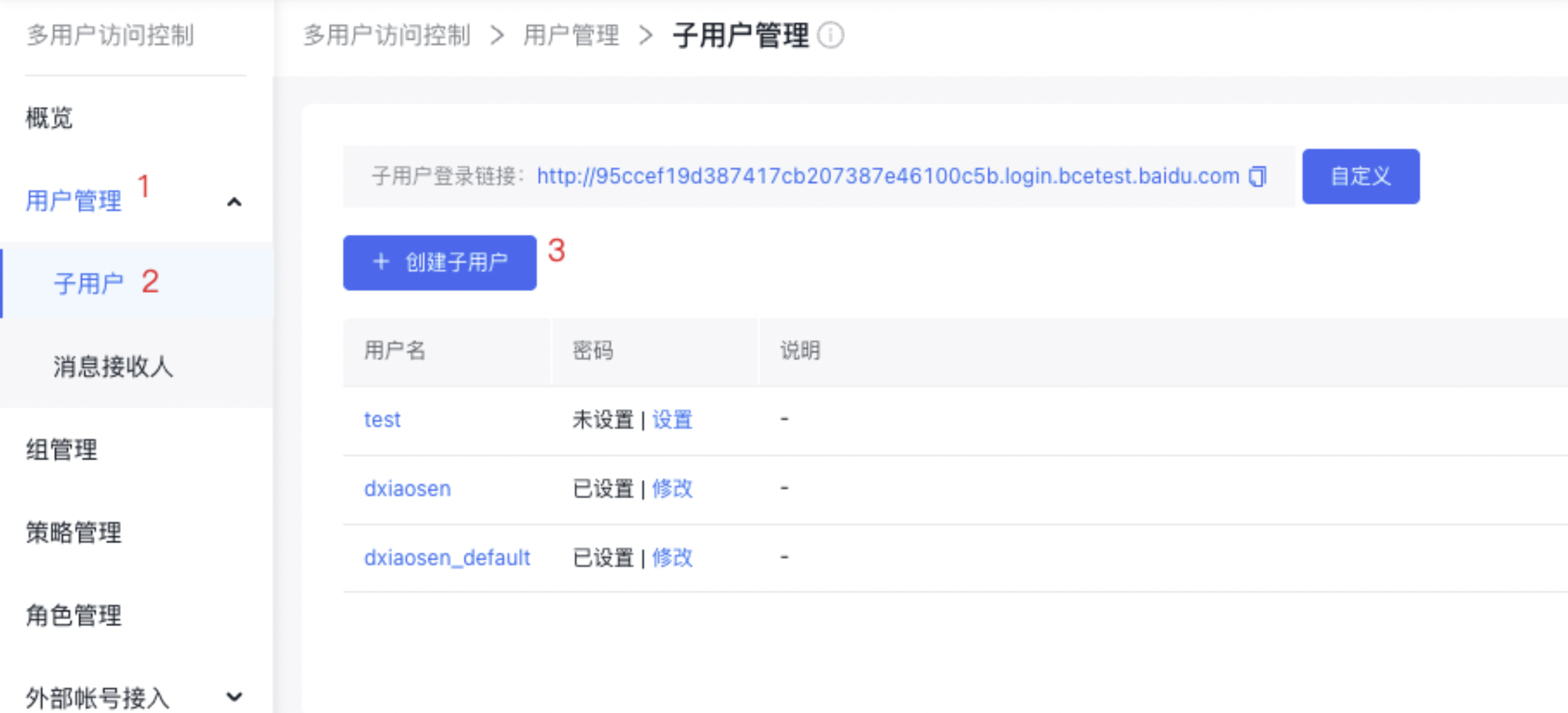
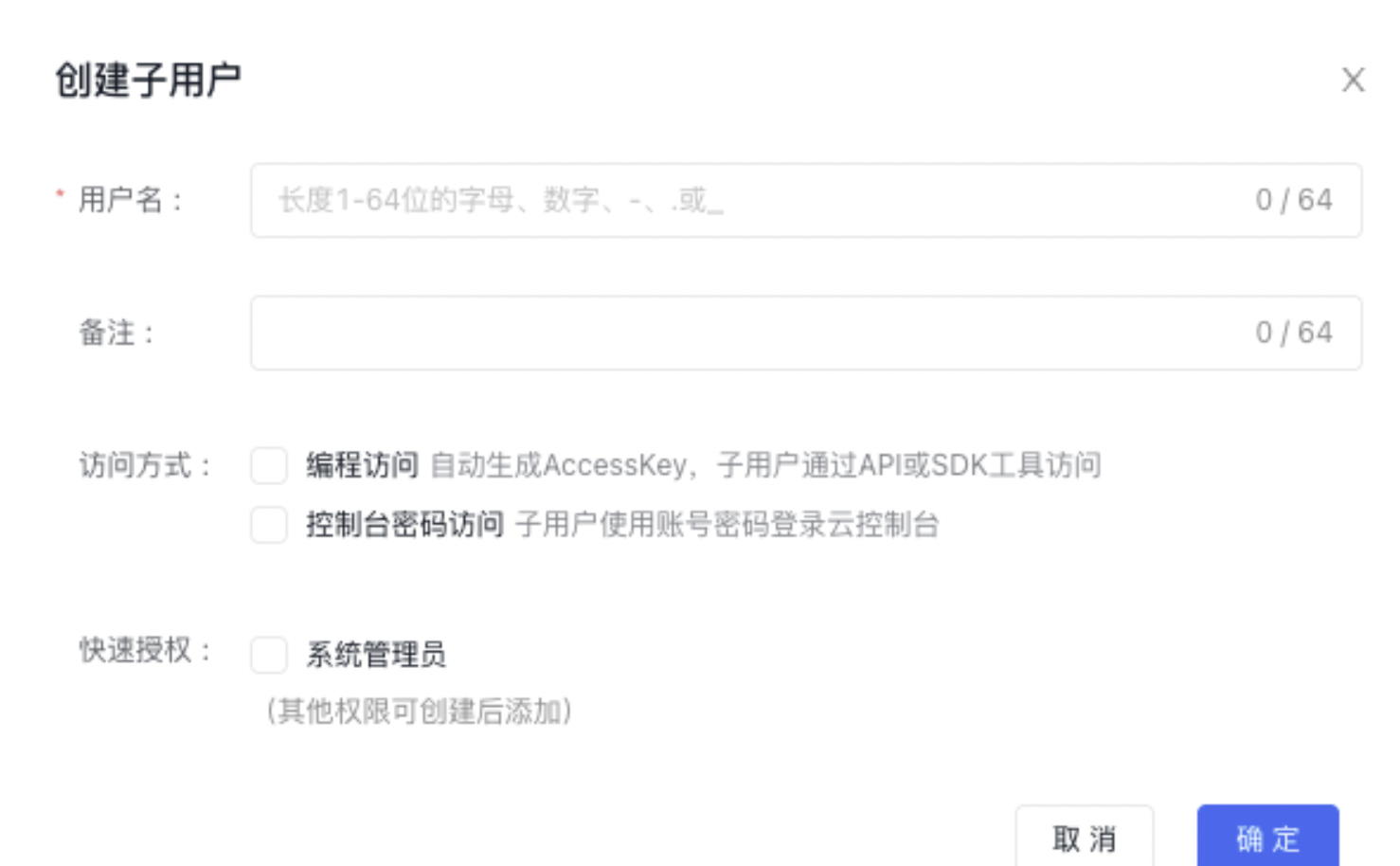
- In the Create IAM User dialog box, enter the User Name, click Confirm, and return to the IAM User Management List to view the new IAM user.
Configuration Policy
BLB and LBDC offer both system and custom policies to enable product-level and instance-level permission control.
- System policy: Permission set predefined by Baidu AI Cloud System for resource management. Such policies can be directly authorized for IAM users, and users can only use it but cannot modify it;
- Custom policy: A user-created, more granular set of permissions for resource management, allowing specific permissions to be configured for single instances. This provides flexibility to address the unique permission management needs of different users.
System Policy
The system policy includes 3 types of policies: management permission, operation and maintenance permission and read-only permission. The scope of permission is as follows:
| Policy name | Permission | Permission scope |
|---|---|---|
| BLBFullControlAccessPolicy | Permissions for full control and management of Baidu Load Balance (BLB) instances | View instance list, view instance details, modify BLB name and description, configure listener, configure real server, monitor instance, trigger instance alarm, create BLB instance, and delete BLB instance |
| BlBOperateAccessPolicy | Permission for operation and maintenance of Load Balancer (BLB) | View instance list, view instance details, modify BLB name and description, configure listener, configure real server, monitor instance, and trigger instance alarm |
| BlBReadOnlyAccessPolicy | Permissions for read-only access to Baidu Load Balance (BLB) | View instance list and view instance details |
| LBDCFullControlAccessPolicy | Permissions for full control and management of Load Balance Dedicated Cluster (LBDC) | Query dedicated cluster list, view dedicated cluster details, view associated BLB instances, monitor dedicated cluster, trigger dedicated cluster alarm, create dedicated cluster, delete dedicated cluster, and upgrade dedicated cluster |
| LBDCOperateAccessPolicy | Permission for operation and maintenance of Load Balancer Dedicated Cluster (LBDC) | Query dedicated cluster list, view dedicated cluster details, view associated BLB instances, monitor dedicated cluster, and trigger dedicated cluster alarm |
| LBDCReadAccessPolicy | Permission for read-only access to Load Balancer Dedicated Cluster (LBDC) | Query dedicated cluster list, view dedicated cluster details, and view associated BLB instance |
Custom Policy
Custom policies authorize users at the instance level, differing from system policies as they apply exclusively to selected instances.
An IAM user navigates to Policy Management in the left navigation bar, selects Create Policy, and chooses Create via Visual Editor. The user then enters the Policy Name and sets Baidu Load Balance (BLB) as the Service Type. The method remains set to Visual Editor by default and requires no changes.
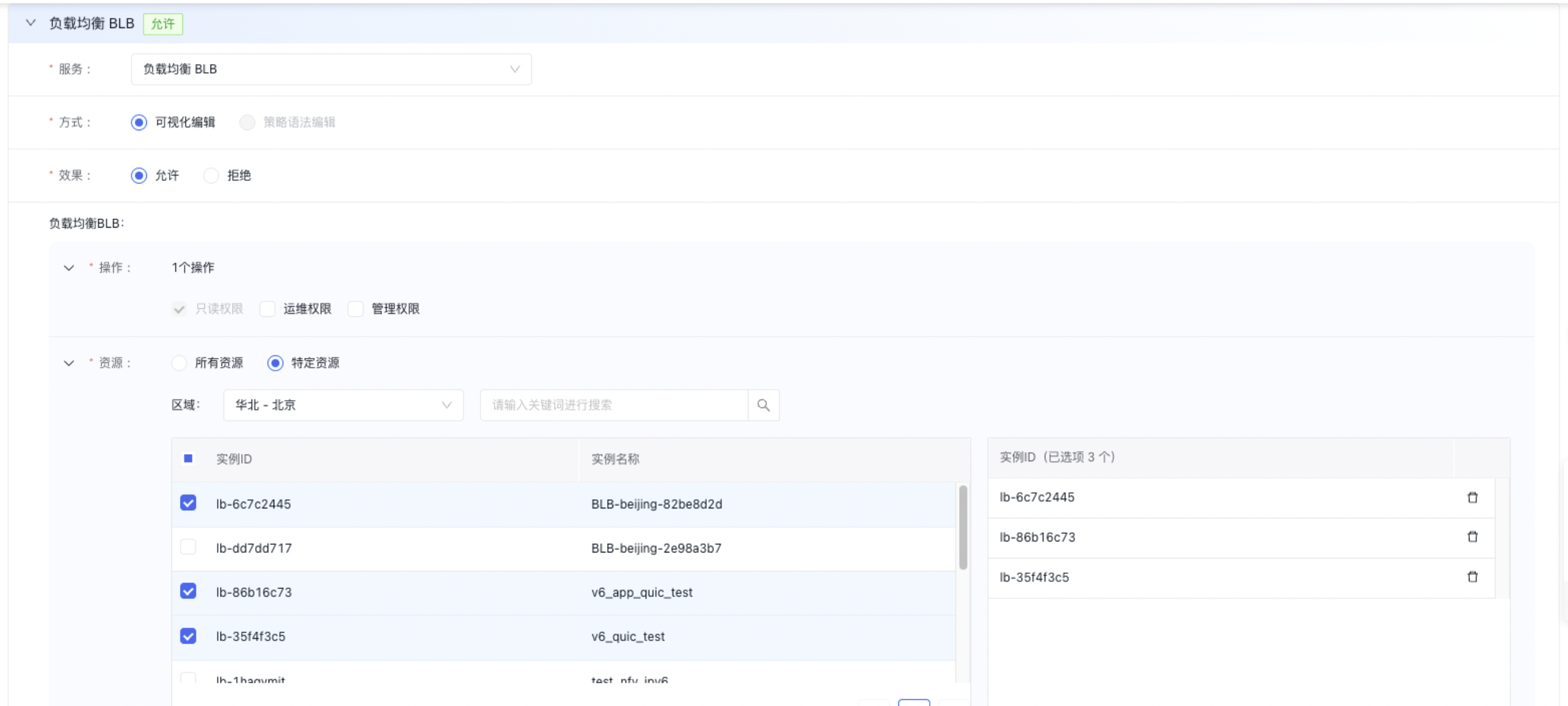 IAM users first navigate to Policy Management via the left navigation bar, then click Create Policy, fill in the policy name and select Load Balance Dedicated Cluster (LBDC) as the service type. The policy creation method defaults to Visual Editor and requires no modification.
IAM users first navigate to Policy Management via the left navigation bar, then click Create Policy, fill in the policy name and select Load Balance Dedicated Cluster (LBDC) as the service type. The policy creation method defaults to Visual Editor and requires no modification.
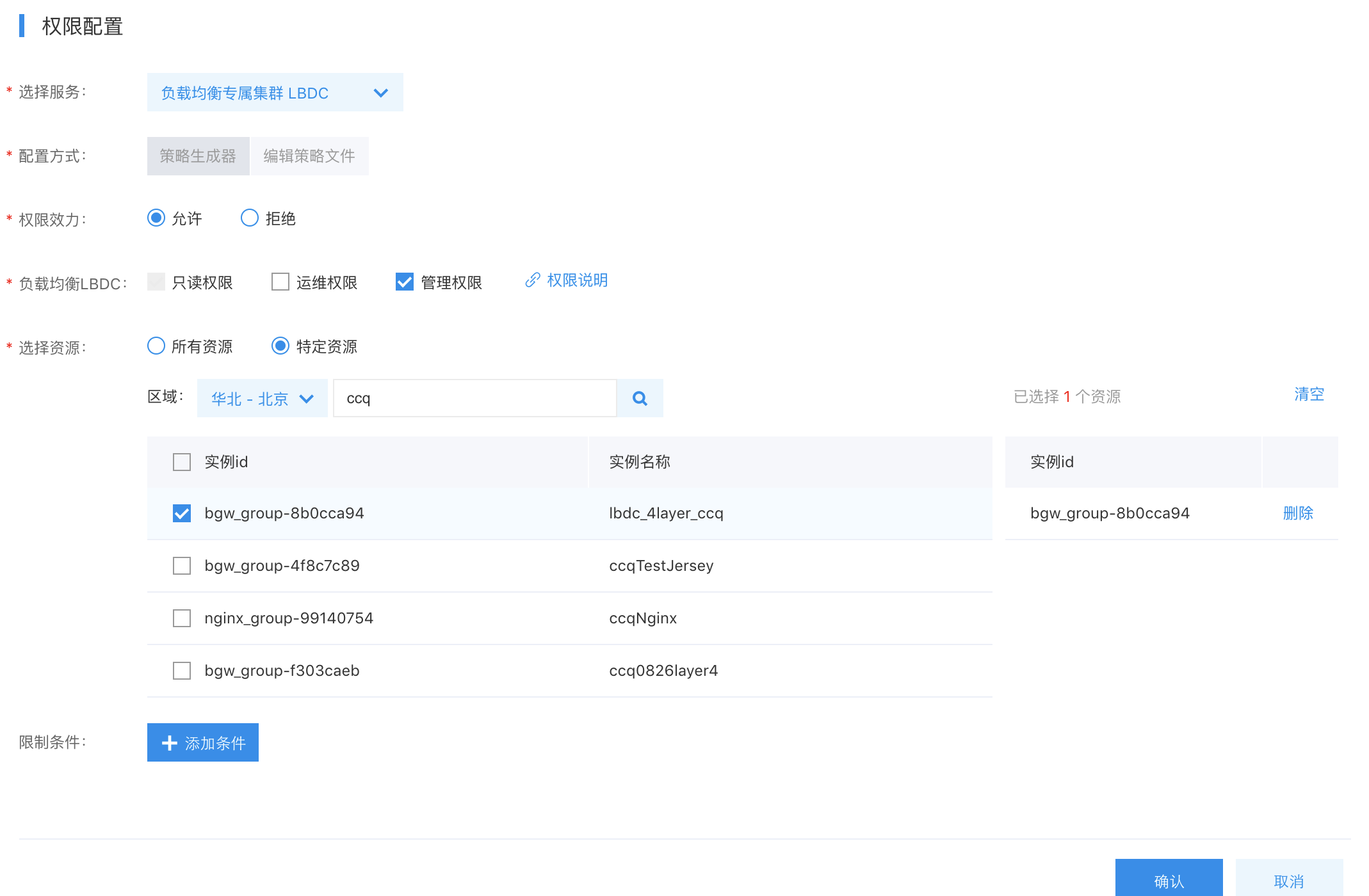
The scope of custom permission is detailed as follows:
| Products | Read-only permission | Operation and maintenance permission | Management permission |
|---|---|---|---|
| BLB | View instance list and view instance details | View instance list, view instance details, modify instance name and description, configure listener, configure real server, monitor instance, and trigger instance alarm | View instance list, view instance details, modify instance name and description, configure listener, configure real server, monitor instance, trigger instance alarm, and delete BLB instance |
| LBDC | Query dedicated cluster list, view dedicated cluster details, and view associated BLB instance | Query dedicated cluster list, view dedicated cluster details, view associated BLB instances, monitor dedicated cluster, and trigger dedicated cluster alarm | Query dedicated cluster list, view dedicated cluster details, view associated BLB instances, monitor dedicated cluster, trigger dedicated cluster alarm, create dedicated cluster, delete dedicated cluster, and upgrade dedicated cluster |
User Authorization
Under User Management -> IAM User, select Add Permission in the Operations column for the corresponding IAM user, then authorize with either System Policy or Custom Policy.
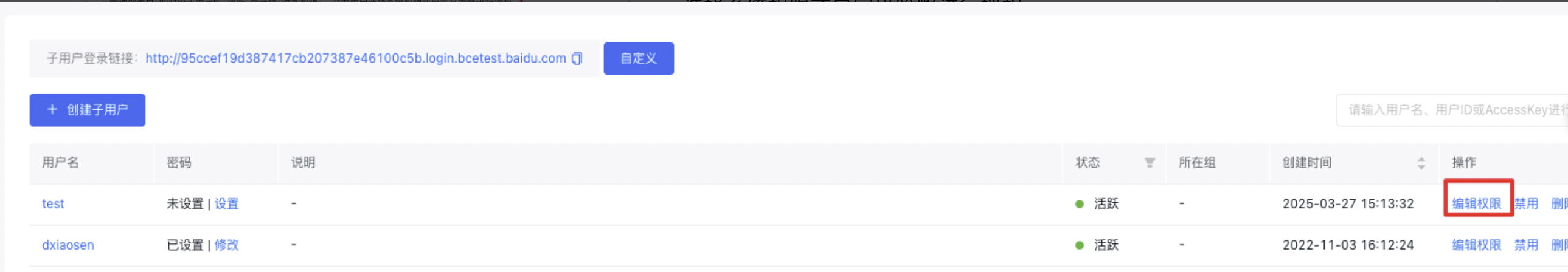
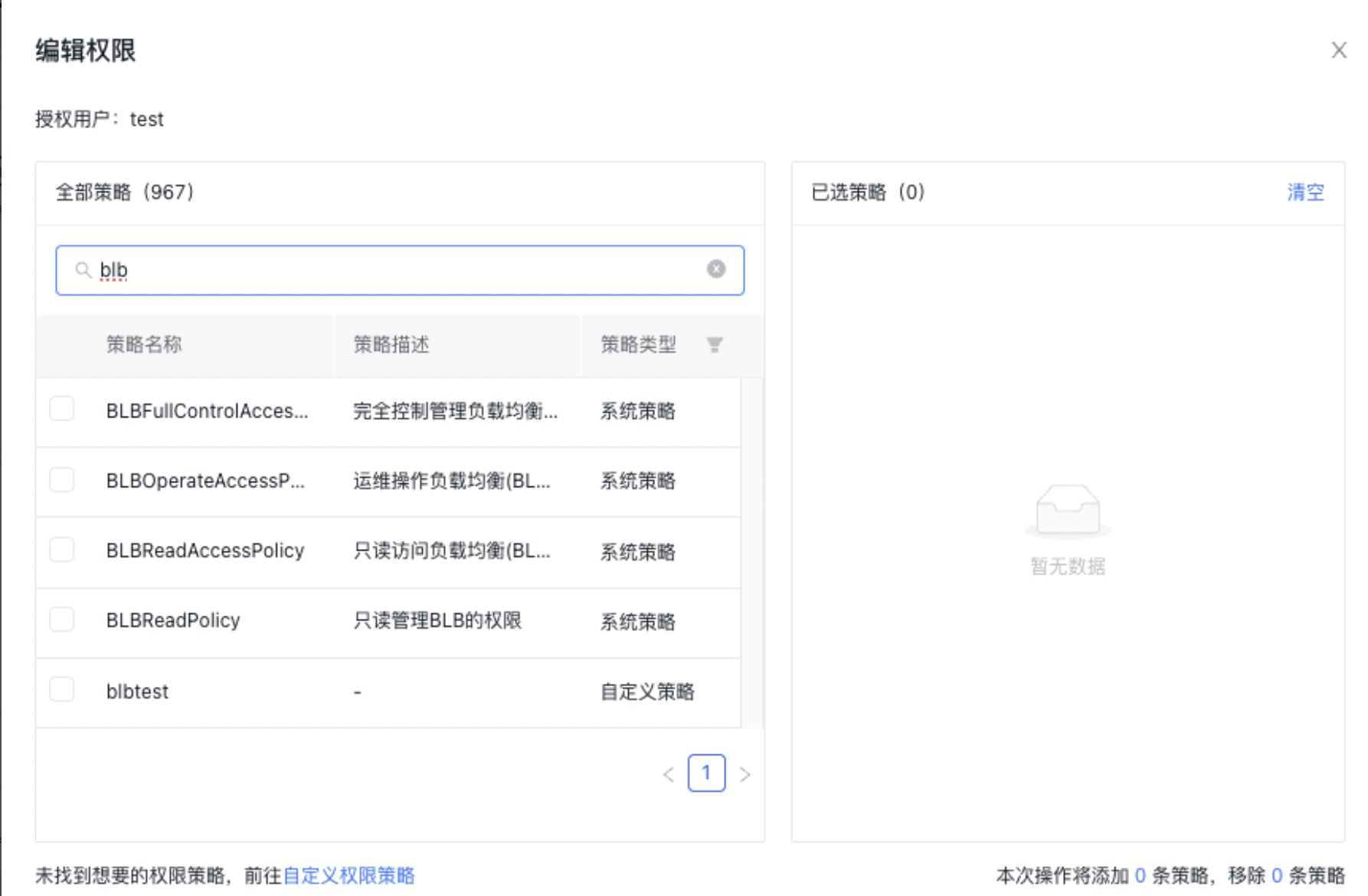
Note: To change an IAM user's permissions without modifying existing policy rules, you must delete the current policy and assign a new one since existing policy permissions cannot be unchecked or edited directly.
Sign in as IAM User
After the root account authorizes the IAM user, it can send the link to the IAM user, who can then sign in to the root account's management console via the IAM user login link and operate or view the root account's resources based on the authorized policies.
For other detailed operations, refer to: Multi-User Access Control.
