Identity and Access Management
Introductions for Identity and Access Management Products
Identity and Access Management (IAM) is mainly used for identity management and access control of Baidu AI Cloud, tackling tasks such as centralized authorization and management of Cloud account, resources sharing and multi-user collaboration. Multi-user IAM is applicable to various functional roles within enterprises. By providing privileges of products to employees, you can share the resources in your account and help them to finish their work. When your company needs collaborative working and resources sharing, recommend you to use the Multi-user IAM.
The followings are typical scenarios to which the Multi-user IAM is applicable:
- For medium and large business customers: Achieve centralized management of resources and access control of employees of different departments within the business;
- For independent software vendor (ISV) or SaaS platform vendor: Achieve centralized resources management and access control for agent clients;
- For small and medium developers or small businesses: Add project members or collaborators to conduct resources management and access control.
For more information on multi-user IAM, see IAM Documentation.
Definitions
- Privilege: Means whether access to one or several interfaces is permitted, e.g., view task details, edit tasks and so on;
- Resources: Means the entity created and maintained by the user in the service and the smallest entity accessed by the user; in BLS, any tasks, collectors and collector groups belong to resources;
- Policy: Means a combination of privileges, resources, and user identities, such as read-only policy or custom policy;
System Policy Privileges Description
The system policies of BLS include read-only privileges, OPS privileges, and management privileges. The details are as follows:
| Policy Names | Privileges Description | Privilege Scope |
|---|---|---|
| BLSReadPolicy | Read-only BLS Access Privileges | It is allowed to view task details, collector details, collectors group details and collector installation only; |
| BLSOperatePolicy | Means the BLS OPS privilege | Besides read-only privilege, it is also able to edit tasks, start/stop tasks, edit collectors, and collector groups; |
| BLSFullControlPolicy | It means the privilege for full control and management of BLS. | It has the all privileges for access to BLS; |
Description of Privileges for Custom Policies
The types of privilege operation and scope of privilege for custom policy of BLS are described in detail as follows:
| Resources Dimension | Privilege Name | Description |
|---|---|---|
| Task | View task details | No |
| Edit task | Add and delete collectors for tasks, modify task configuration information | |
| Start/stop task | No | |
| Delete task | No | |
| Collector | View collector’s detailed information | No |
| Edit collector | Add or delete tasks for collector | |
| Delete collector | No | |
| Collectors group | View detailed information of collectors group | No |
| Edit collectors group | Add or delete collector for collectors group and modify description of collectors group | |
| Delete collectors group | No |
Authorization Case
The authorization steps are as follows:
- Create a sub-user
- Create a custom policy
- Grant privileges to a sub-user
- Log in to a sub-user on the console and access the product
Create a Sub-user
Step 1: Click the user avatar at the upper right corner, and then "Multi-User IAM";
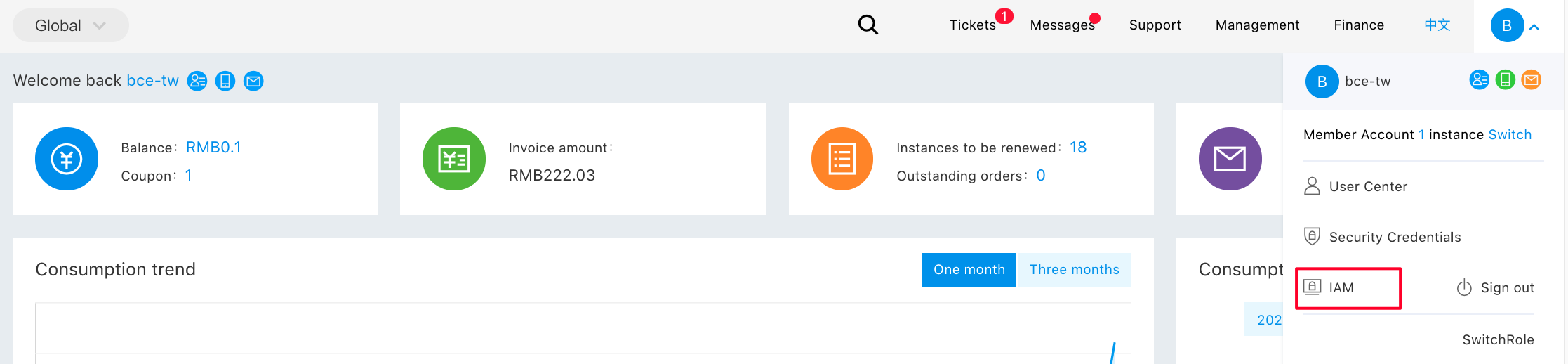
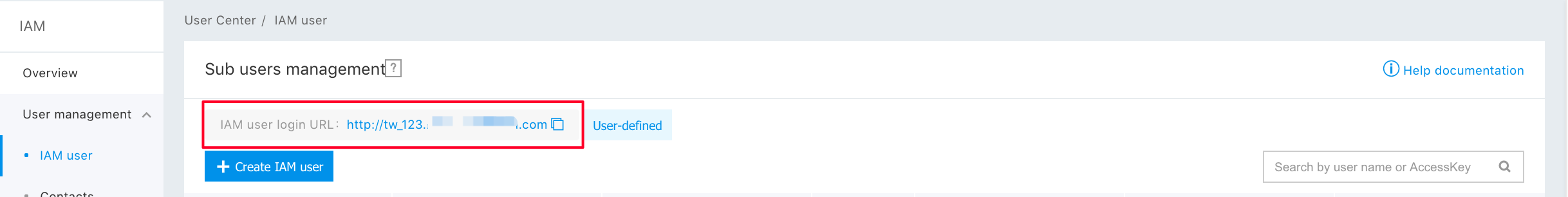
Step 2: Click "Create a sub-user". After the sub-user has been created successfully, the login link is as shown in the picture;
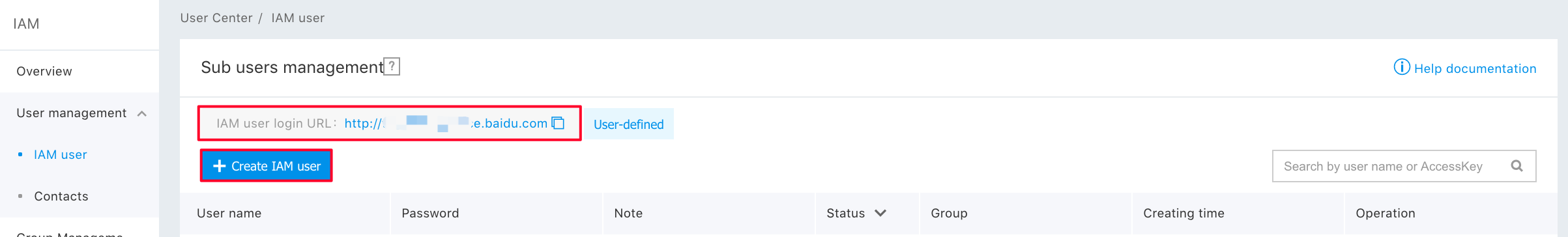
See Documentation on the multi-user IAM for more details.
Create a Custom Policy
Step 1: Click “Policy Management” on the left side, click “Create a Policy”, and then click “Create by Policy Generator”;
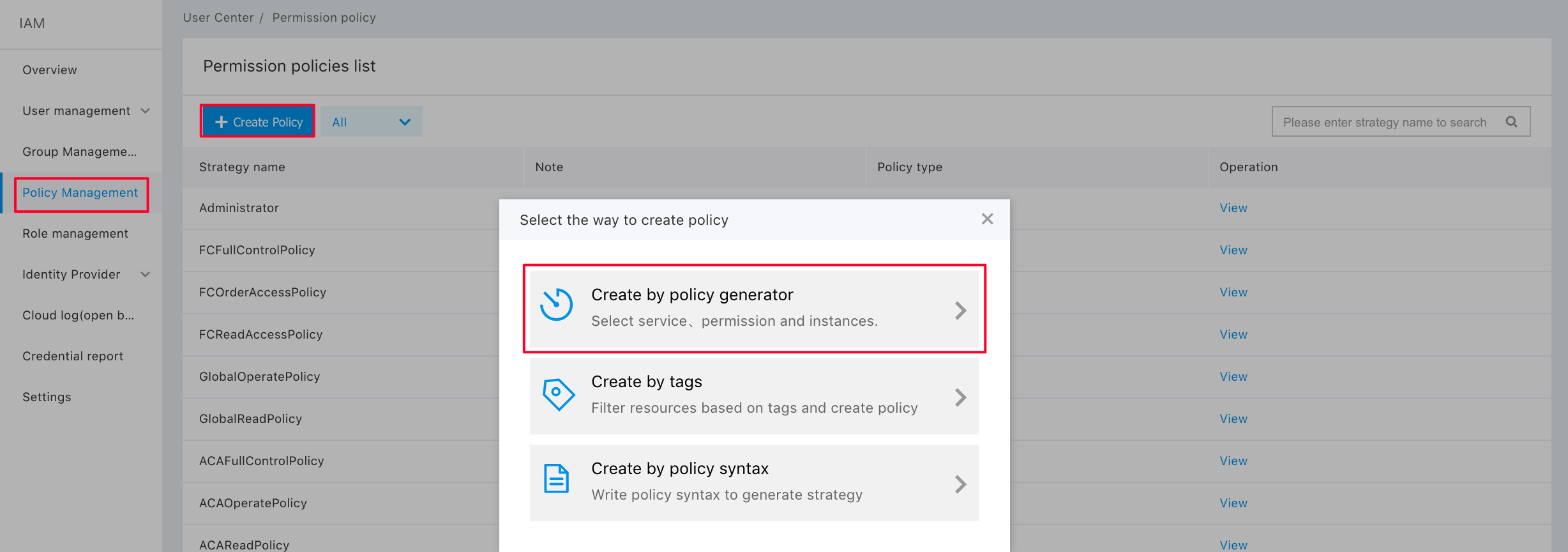
Step 2: Click “Add a Privilege”;
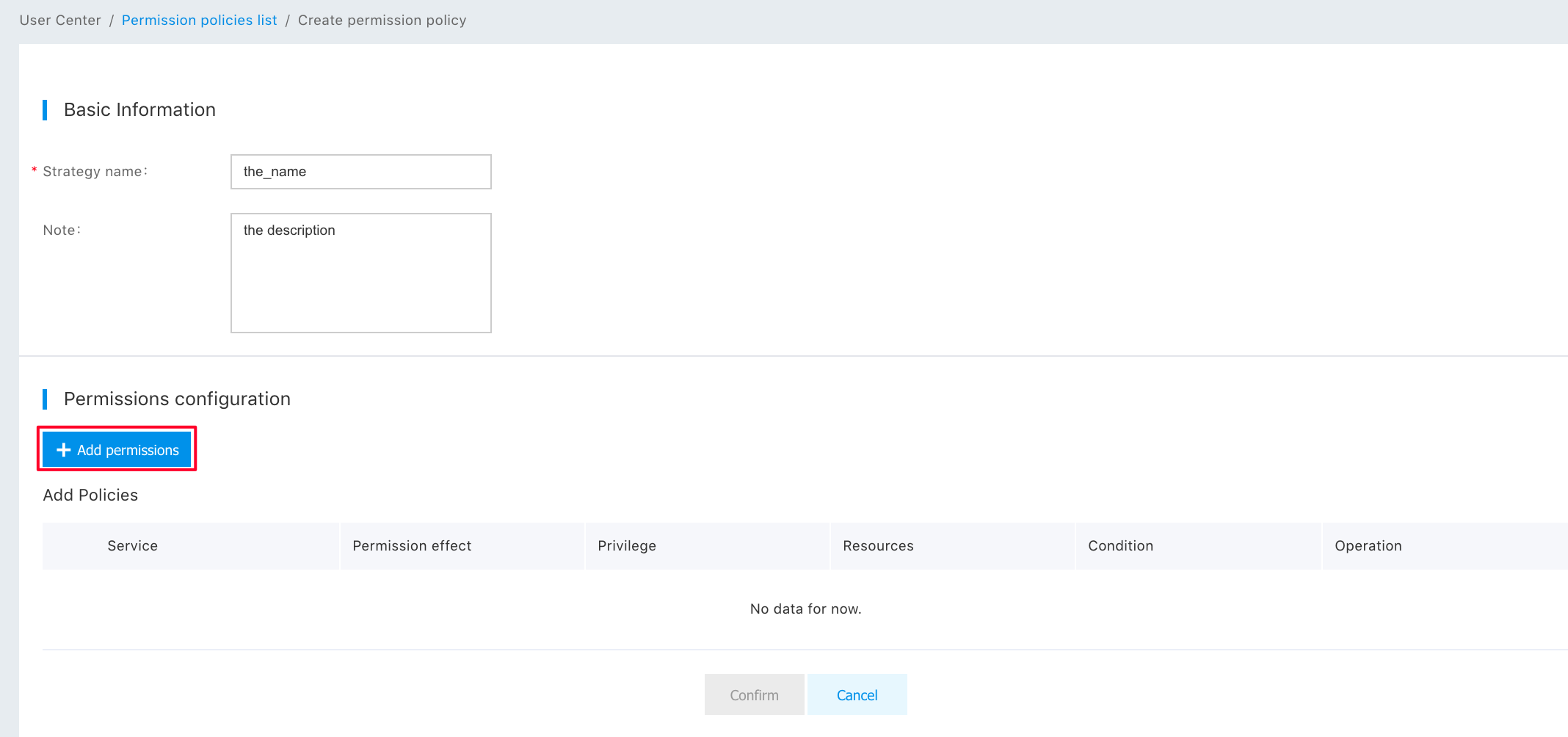
Step 3: Select "BLS", select “Privilege” and “Resources”, and then click "Finish";
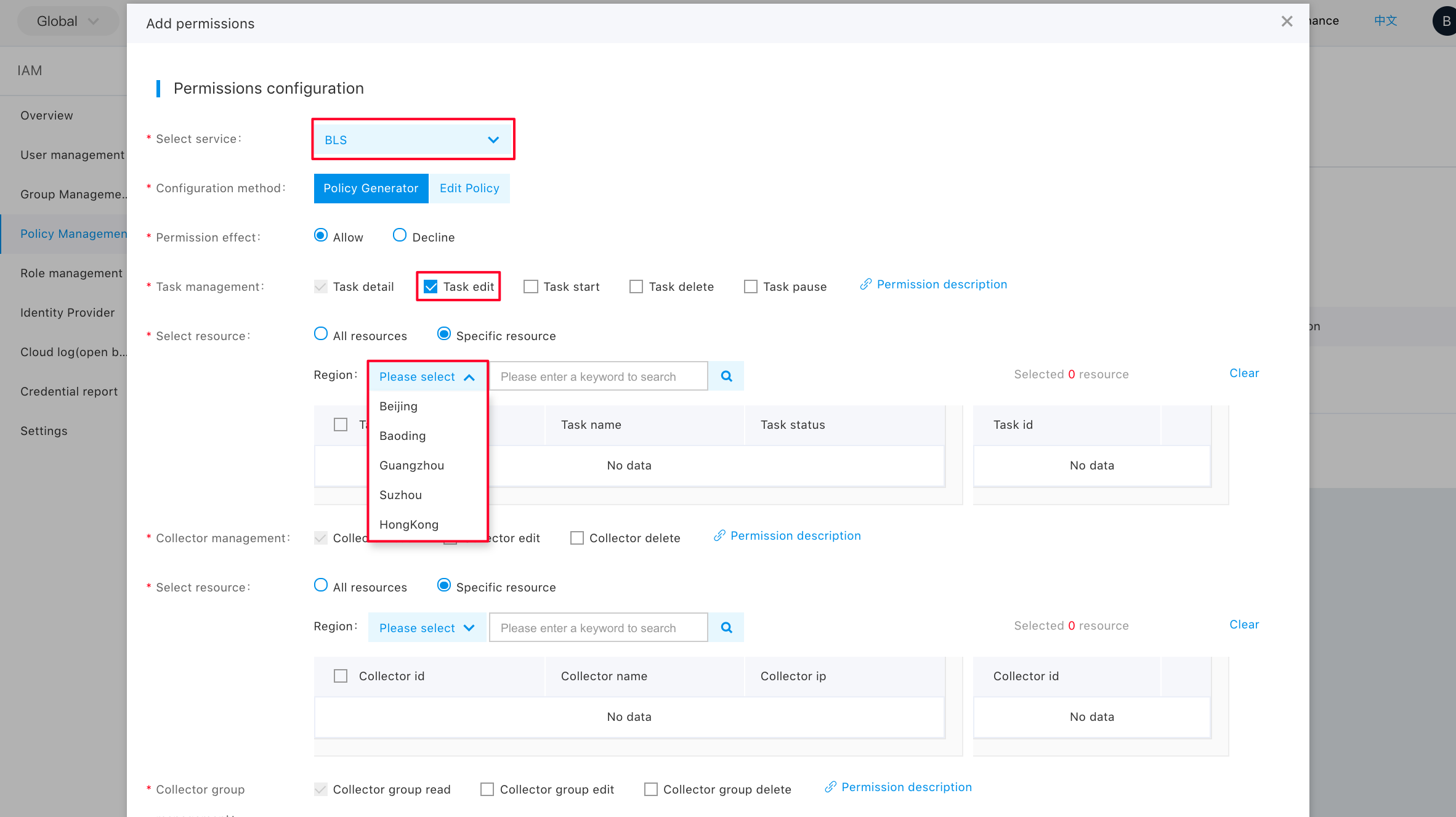
Step 4: Click "Finish" again;
Grant privileges to a sub-user
Step 1: Click "Add a Privilege";
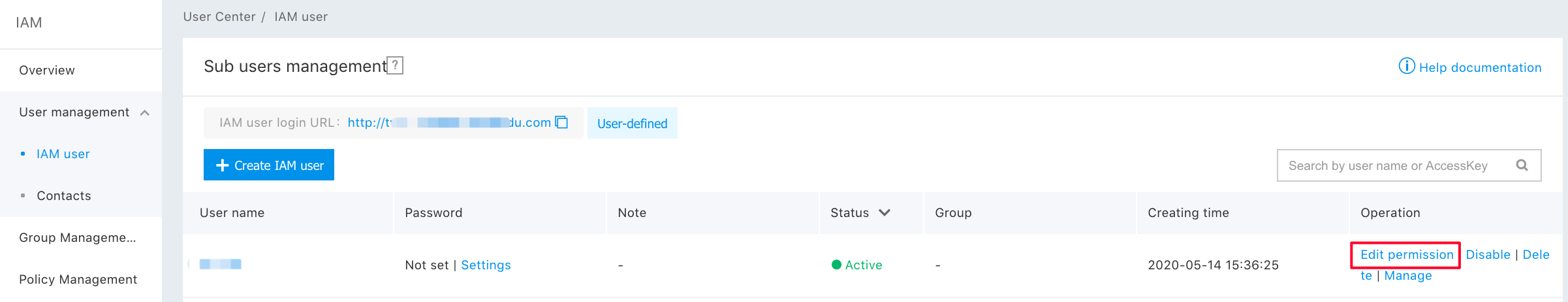
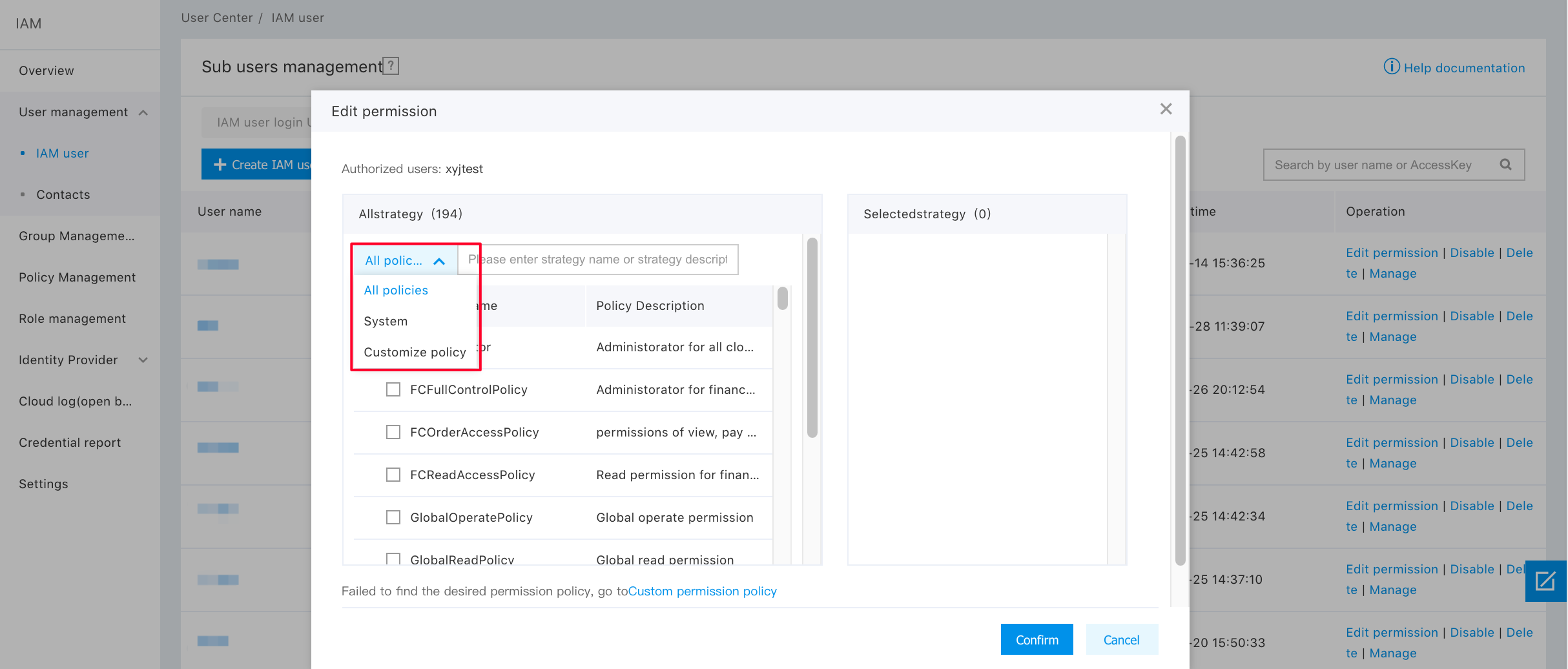
Step 2: Search for "bls", so that you can add "System Policy" and "Custom Policy” here; and then click "OK";
Console Login of sub-user and Product Access
Step 1: Visit the sub-user login link;
Step 2: Click BLS and access the product;
