Web Application Firewall (WAF)
- Overview
- Features
- Advantages
- Application Scenarios
Overview
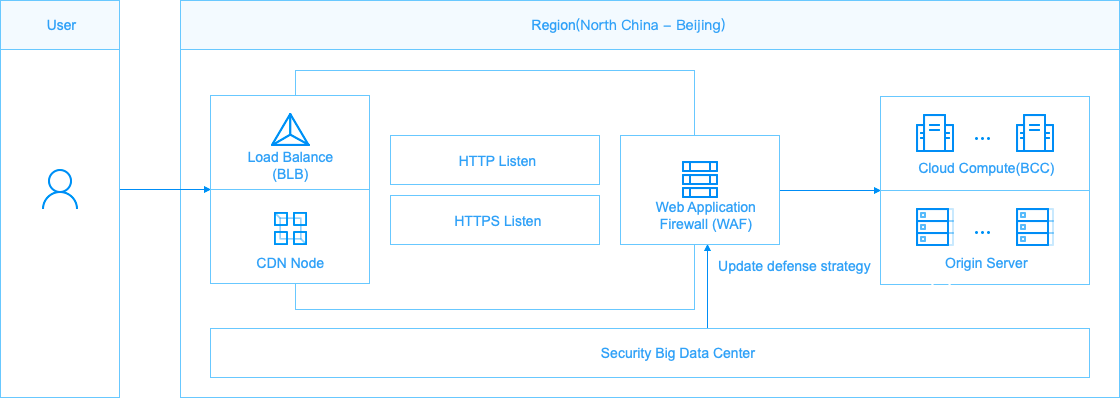
The Web Application Firewall (WAF), a Web security protection product provided by AI Cloud to users, can effectively protect against Web attacks, help users customize access rules, and improve the security of businesses including websites. With the original new WAF technical framework, you can deploy the WAF instances to individual Web business entries. Thus, it protects the source site from hacker attacks by bypassing the agent under the traditional cloud WAF framework. Also, integrating the cloud security big-data capacity enables the WAF to be more effective and convenient to help customers improve website security and availability.
Features
Provide Web service attack protection features for the HTTP/HTTPS businesses, including SQL injection, XSS cross-site, Webshell upload, unauthorized access.
AI Cloud security and operation experts can get zero-day vulnerability information for the first time, update the Web application firewall rules library timely, and mitigate the influence imposed by the zero-day vulnerabilities.
You can set the bypass observation mode. Also, you can record the attacks only, but cannot block them. This feature facilitates the customer to evaluate the working condition of several rules (including total definition) in actual businesses.
The user can perform a combination match for several kinds of HTTP fields to form custom rules for your business. It supports simple logic syntaxes.
Advantages
Unique and Innovative Cloud Framework
Where you deploy the WAF instance to your cloud IT network framework, it is possible to eliminate the exposure of traditional cloud WAF source sites thoroughly.
Accurate and Effective Rules and Policies
The WAF policy has been subject to tests for many years in several businesses. The rules and policies are accurate and effective and have excellent vulnerability coverage rates and detection rates.

Easy to Use
You need not perform complicated DNS settings. It is easy to operate.

Event Tracing
It can completely record various elements of the attack event to facilitate customers to analyze and know attack status.
Application Scenarios
- Data Theft Prevention
- 0-day Vulnerability Attacks
Data Theft Prevention
The hacker can scan the Internet application to discover the application security vulnerabilities, and make use of the security vulnerabilities to invade the server and database and steal the core data of the businesses.
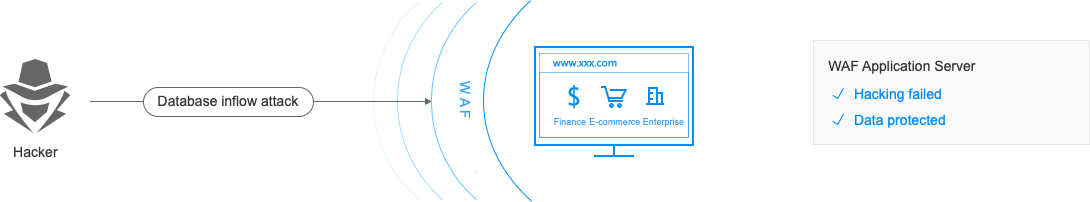
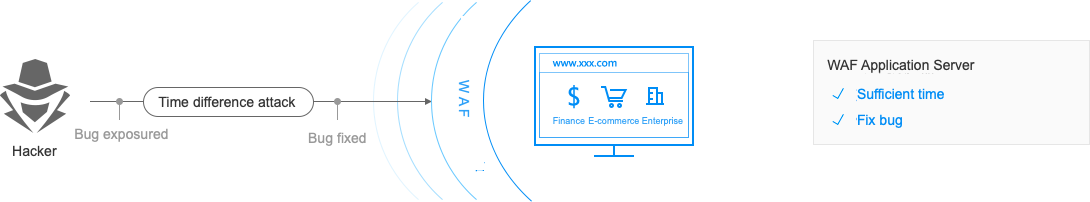
Protection Against the Zero-day Vulnerability Attacks
After making an announcement that the system software has a Web security vulnerability, the WAF operation personnel releases the protection policy as soon as possible to intercept the attack code. Thus, it saves valuable time for installing a patch to fix the vulnerability.