Identity and Access Management
Introduction
Identity and Access Management (IAM) helps users manage access rights to resources under cloud accounts. It applies to different roles in the enterprise and can give different rights to different employees to use products. It is recommended that you use identity and access management when your enterprise has multi-user collaborative operation resources.
Applicable to the following scenarios:
- Customers of medium and large enterprises: Perform the authorized management of multiple employees in the company;
- Technology-based vendor or SAAS platform providers: Manage the resources and rights of the proxy clients;
- Small and medium developers or small enterprises: Add the project members or collaborators to manage the resources.
The identity and access management enables coordinated management and use of BMR resources by different persons or different departments in the company or organization. In the BMR, the clusters and scheduled tasks are resources. In the coordination, the master user creates the sub-user and assigns the access policy.
Overview of access policy:
The access control policies consist of the dimensions of permission and resource. The permission means the user's executable actions, such as creation, deletion, check, and modification; the resource means the cluster or scheduled task. The permissions comprise the types of coarse granularity and fine granularity. The coarse granularity permission does not limit resources, and it can correspond to different fine granularity permissions; the fine granularity permission needs to select one or more resources. The sub-user granted with a certain strategy has access to corresponding resources.
Policy example:
ACL{ //the policy has READ coarse granularity permission to all resources;
"resource": ["*"], //resource
"permission": [ //permission
"READ"
]
};
ACL{ //the policy has ScaleCluster (expand/reduce capacity) fine granularity permission to a cluster;
"resource": ["cluster/ clusterID"], //resource
"permission": [ //permission
" ScaleCluster"
]
}.Notes:
- Master user owns all resources of BMR, and the master user assumes the expenses on resources created or deleted by the sub-user.
- The sub-user and master user have the same permissions to the operation of cluster templates, which have no permission control.
- The policy change takes effect after 5 minutes.
Create Sub-users
- After the user having a primary account number logs in, select "Identity and Access Management" in the console to enter the user administration page.
- Click "User Management" in the left navigation bar, and click "New User" on the "Sub-user Management List" page.
- In the popped up "New User" dialog box, enter and confirm "User Name", and return to "Sub-user Management List" to view the new sub-user.
Configuration Policies
The permission policy has two types: [System Privilege Policy](#System Policy) and [Custom Privielge Policy](#Custom Policy). They are used to control BMR's product-level permission and resource-level permission, respectively.
- System policy: A permission set predefined by Baidu AI Cloud system to manage resources. Such policies can directly grant permission to the sub-user, which is used rather than modified by the user.
- Custom policy: It is created by users, more detailed permission set for managing resources, which can configure permission for a single instance, and can ensure differentiated permission management of accounts to different users more flexibly.
System Policies
Click "Resources Management" to enter the policy management page. The system policy is preset for users by BMR and cannot be modified by users. You can enter "bmr" in the right search box to view all BMR system policies.
The four system policies provided by BMR and their permissions are as follows:
| System Policies | Privileges Included | Description |
|---|---|---|
| BMRListAllStepAccessPolicy | LIST_ALL_STEP | Privilege to view the list of all BMR jobs |
| BMRUseOnlyAccessPolicy | READ | Privilege to use BMR policy only, including permission to use BMR only |
| BMRCreateAndDeleteOnlyAccessPolicy | "ReadCluster", "ReadExecutionPlan", "CREATE_DELETE" |
Privilege to create and delete cluster and scheduled task policies only, including permission to create and delete BMR resources only and permission to read cluster and scheduled task |
| BMROperateOnlyAccessPolicy | "ReadCluster", "ReadExecutionPlan", "OPERATE" |
Privilege to operation and maintenance of BMR policies only, including permission to operation and maintenance of BMR and permission to read cluster and scheduled task |
| BMRFullControlAccessPolicy | "FULL_CONTROL" | Privilege to full control and management of BMR policies, including permission to full control and management of BMR |
Custom Policies
By clicking "Custom Policy", entering the policy name, and selecting service type of "Baidu MapReduce BMR", the sub-user can add the custom policy to add custom permissions. You can add custom policies by configuring policy generator or editing policy files. The fine granularity permission is the only option for policy generator, and coarse granularity permission and fine granularity permission are two options for editing policy files. You can set and modify the policy according to specific permissions.
Policy Generator
For the policy generator, there are two resources: cluster and scheduled task. The resource box represents the fine granularity permission for that resource. After selecting the permission, you can click different regions in "Select resources" to see the resources under the region. Click "Finish" after selecting the resources.
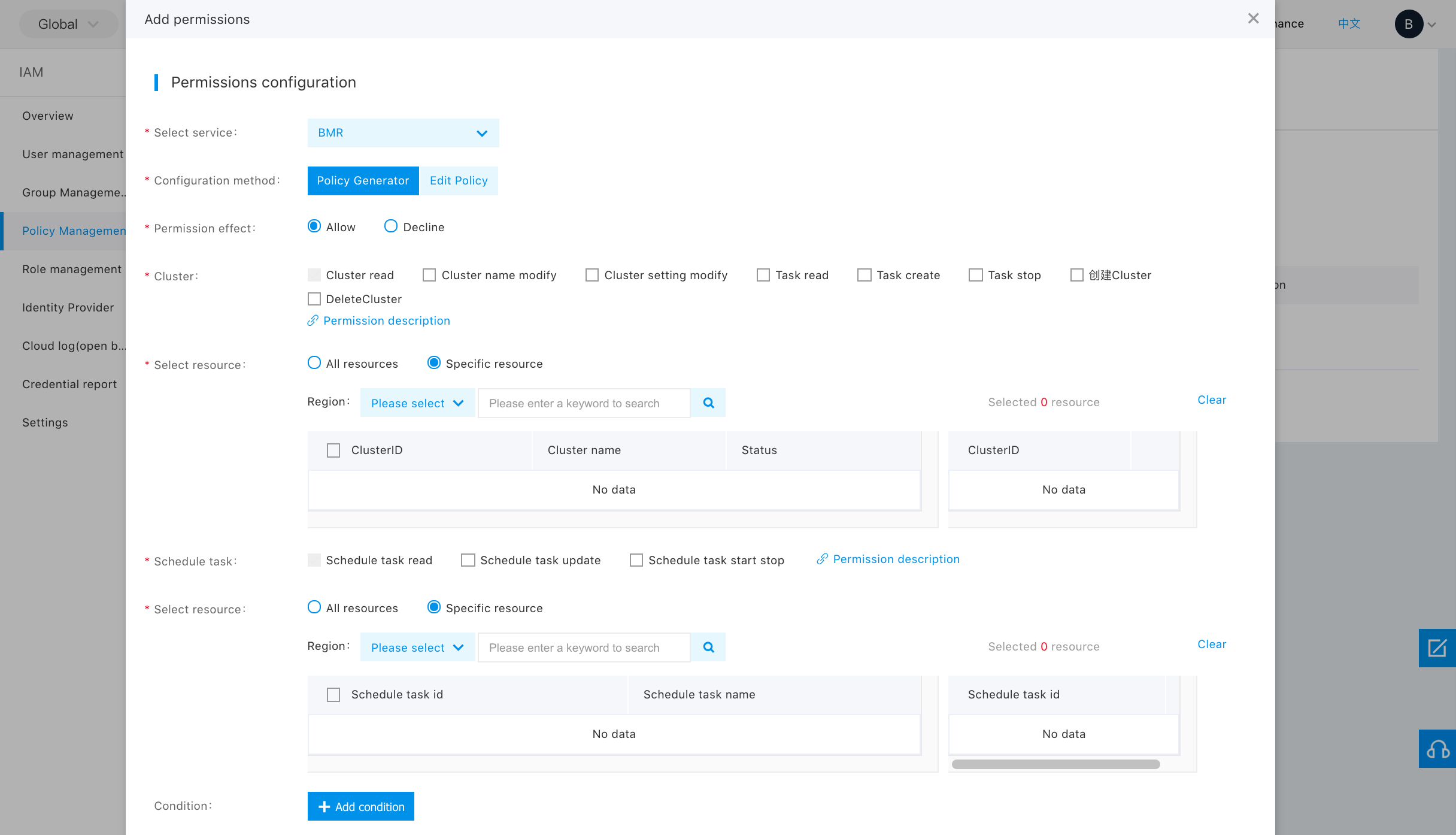
Note: Cluster and scheduled tasks are parallel resources. In the policy, you can configure the permission to one or both of such resources.
Editing Policy Files
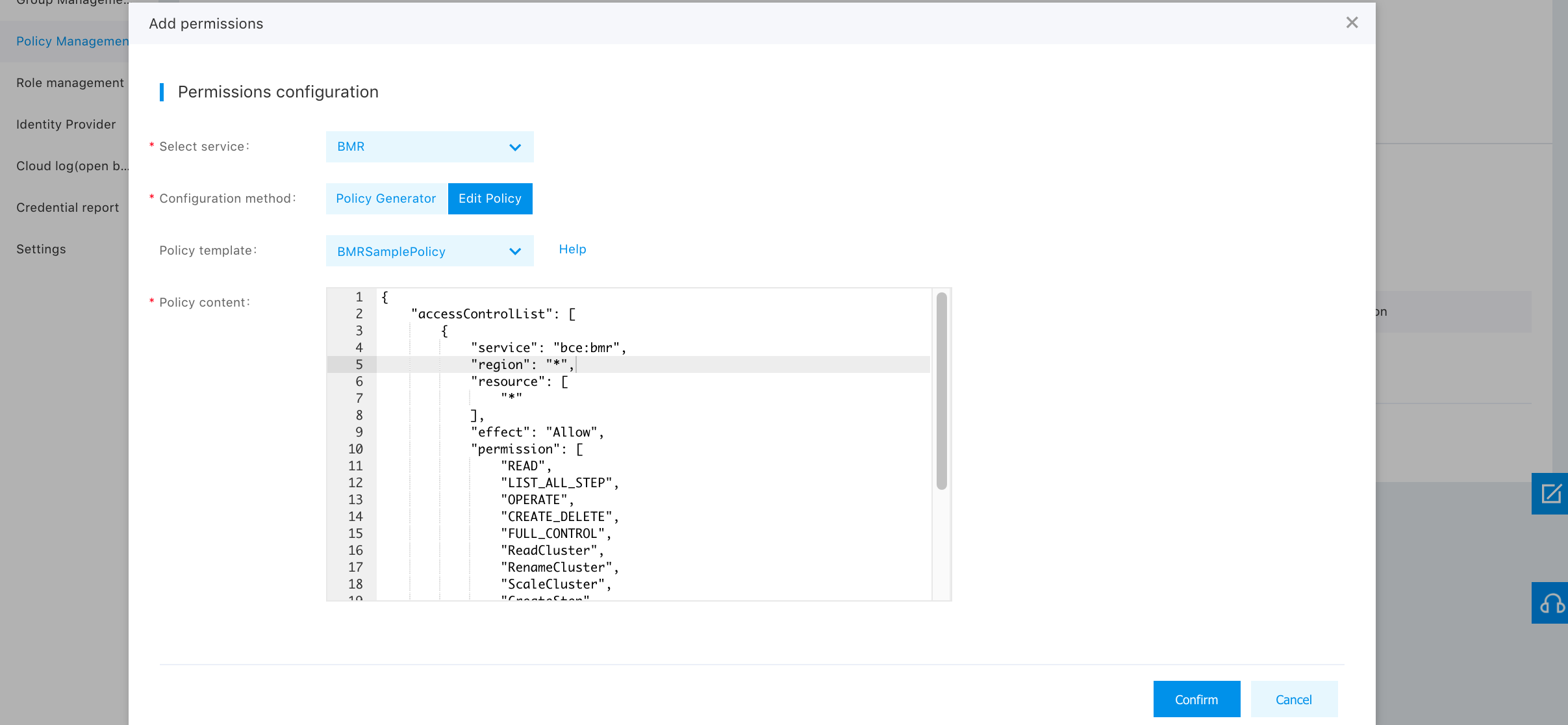
Essentially, the policy file is a JSON file, and permission and resource in the file are used to define permission and resource. For easy editing, the permission list shows all coarse and fine granularity permissions by default, and you can delete elements in the list as needed.
Note:
You cannot add or delete any field (such as service and region) in the policy file, and you cannot change the field name.
The definition of all fields in the policy file is as follows:
| Field Name | Data Type | Description |
|---|---|---|
| accessControlList | list | Identify the start of main body of Access Control List (ACL), consisting of one or more configuration items. |
| service | string | Service component influenced by the configuration item, and BMR fixed value is "bce:bmr" and cannot be changed. |
| region | string | Region influenced by the configuration item, and the value is "bj", "gz", "su", "bd", "hkg" and "?". Among them, "bj" represents the Beijing region, "gz" represents the Guangzhou region, "su" represents the Suzhou region, "bd" represents the Baoding region, "hkg" represents the Hong Kong region, and "?" represents all regions. The value is inside quotes, and the punctuation is in English semi-angle format. |
| effect | string | Specify whether to run the Request matching the configuration item, and the value is "Allow" or "Deny". "Allow" means execution and "Deny" means no execution. |
| permission | list | Privilege included in the configuration item, and the value is the default element in the permission list. |
| resource | list | Resources included in the configuration item, and the options include wildcard "?" and specific resource ID. "?" means all instances, different instances can be configured for resource ID, and the values are inside quotes in English semi-angle format and spaced with commas. Naming of resource ID: "cluster/cluster ID" or "executionPlan/scheduled task object ID". The scheduled task object ID can be selected from scheduled task resources of policy generator. |
User Authorization
Select "Add Privilege" in the "Operation" column of the corresponding sub-user in "User Administration-> Sub-User Administration List" page, and select and authorize the system privileges or custom policies for users.
Note:
If you modify the permissions of the sub-user without modifying the existing policy rules, you can only delete the existing policies and add policies, but you cannot cancel the added policy permissions.
Service Authorization
For the sub-users to use BMR services, you need to authorize permission to other services in Baidu AI Cloud. The permission policy and influence the scope of services are as follows:
| Service Policy Name | Description | Influence Scope |
|---|---|---|
| FCOrderAccessPolicy | Full control over order service permission | Query and create cluster |
| VpcFullControlPolicy | Full control over VPC service permission | Create Clusters |
| SubnetFullControlPolicy | Full control over subnet service permission | Create Clusters |
| BosFullAccessPolicy | Full control over BOS service permission | Choose to store logs in BOS when creating cluster |
System policies cover all policies above.
Sub-user Login
After the user having a primary account number has authorized the sub-user, it can send the link to the sub-user; the sub-user can log in to the management console of the main account through the IAM user login link, and operate and view the main account resources based on authorized policies.
For other detailed operations, please see Identity and Access Management.
Privilege Model
| Name of Coarse Granularity Privilege | Description | Name of Corresponding Fine Granularity Privilege | Description |
|---|---|---|---|
| READ | Privilege to use BMR only | ReadCluster | Read cluster |
| - | - | ReadStep | View job details |
| - | - | CreateStep | Create step |
| - | - | CancelStep | Terminate step |
| - | - | ReadExecutionPlan | Read scheduled task |
| - | - | UpdateExecutionPlan | Update scheduled task, including adjusting the execution policy and adding and deleting jobs on the scheduled task |
| LIST_ALL_STEP | Produce job lists | No | - |
| CREATE_DELETE | Privilege to create and delete BMR resources only | No | - |
| OPERATE | Privilege to operation and maintenance of BMR only | RenameCluster | Change cluster name |
| - | - | ScaleCluster | Modify cluster configuration, i.e., capacity expansion and reduction |
| - | - | SwitchExecutionPlan | Start-stop of scheduled task |
| FULL_CONTROL | Privilege to full control and management of BMR | No | - |
Selecting a coarse granularity permission policy means selecting all fine granularity permissions corresponding to the coarse granularity permission. From the way of naming, it can be seen the name of coarse granularity permission includes uppercase characters only, and the name of fine granularity permission is camel case.
Notes:
- LIST_ALL_STEP coarse granularity permission means access to all job lists, including job lists on the cluster page;
- READ coarse granularity permission or ReadStep fine granularity permission for specified cluster ID means access only to job lists on the cluster page, and you can view job details with such permission.
