Ranger
Ranger Introduction
Apache Ranger provides a centralized access control framework to perform fine granularity access control over HDFS/Hive/YARN components in Hadoop ecology and facilitates the administration through the Web UI page.
Create Clusters
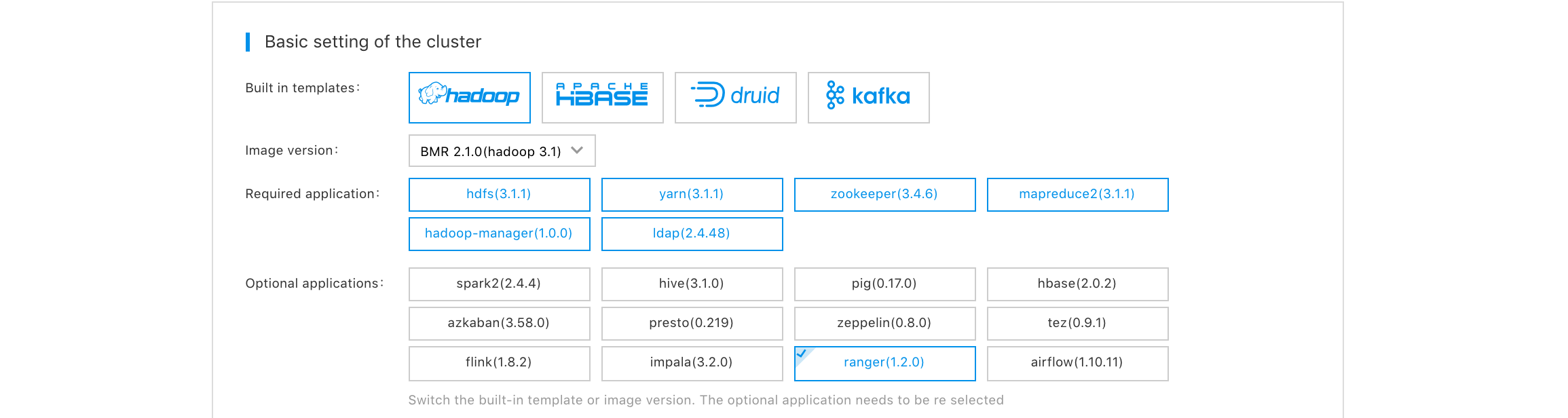
BMR of version 1.2.0 and above supports the integration of Ranger components. You can select Ranger components when purchasing the cluster, as the following figure shows:
Access Cluster’s Ranger Web Page
Use SSH Tunnel to access Ranger Web page
- During the creation of a cluster, you can add Ranger application when configuring software.
- Create an SSH Tunnel and configure the browser. For more information, please see all steps in [Preparation] (BMR/Operation Guide/Access Cluster Service Page.md#Environment Preparation for Using SSH Tunnel to Access Cluster).
- After proxy setup, you can execute hostname command on the Master node to obtain the CVM server name.
- You can log in to Ranger UI interface by accessing link http://hostname:6080, and the default user name/password is admin/admin, as the following figure shows:

Change Password
After initially logging in to the background, the administrator needs to change the password of the admin account, as the following figure shows:

Permission Configuration
BMR Ranger component enables hdfs/yarn/hive plug-in by default. After logging in to Ranger administration background, you can see HDFS service/YARN service and HIVE service created by default.

Enter the Access Manager page to configure permissions for HDFS, YARN, and HIVE components, among other services.
HDFS Configuration
As the following figure shows, you can click HDFS service created by default and enter the policy configuration administration page to configure the policies.
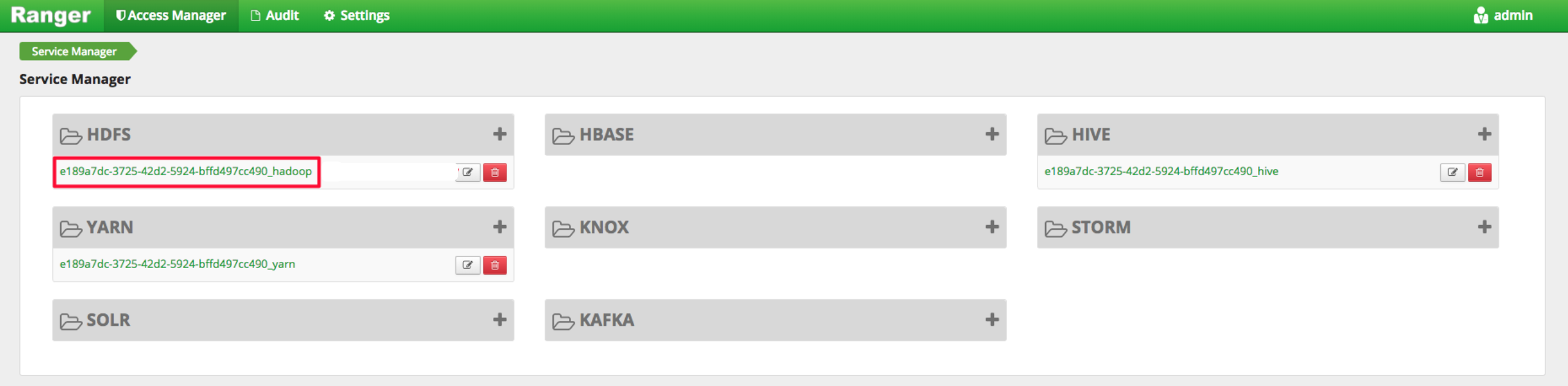
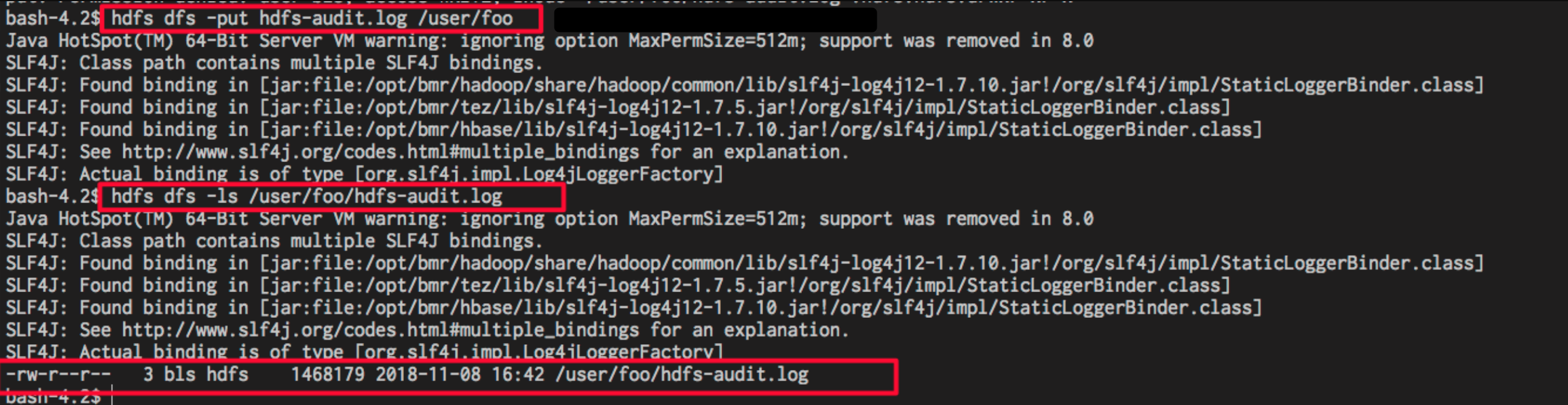
For example, you can grant bls users the read/execute permission to /user/foo; /user/log path.
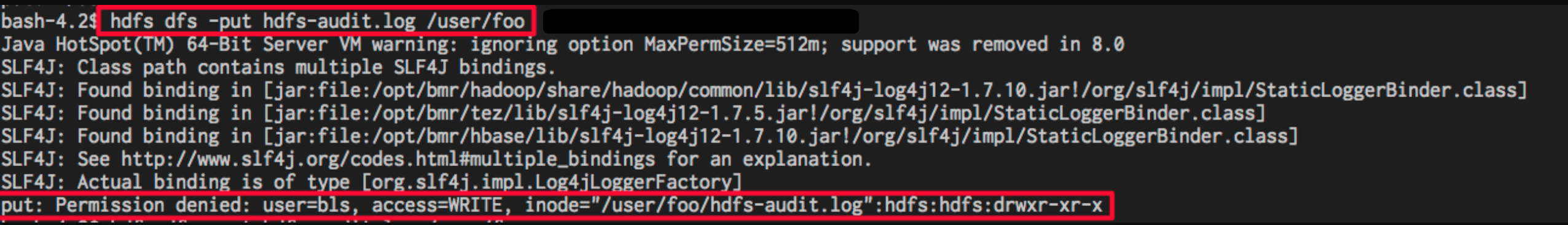
After adding a Policy based on the above steps, you realize the authorization to bls. Under the above setups, bls user only has read and execute permissions to HDFS path for /user/foo. The error of permission denied is reported if the user uploads files. The effect is as follows:
After obtaining the write permission, the bls user can put files to the path. For example:

The effect is as follows:
HIVE Configuration
The user can access Hive data in ways of HiveServer2, Hive Client, and HDFS, so it is required to conduct access control over such three ways.
- HiveServer2 way: The access control over the Hive table/column supported by Ranger Hive plug-in is only limited to the application scenario of HiveServer2 (through beeline and jdbc).
- Hive Client way: Hive’s official access control (Storage Based Authorization) specific to application scenario of Hive Client. Essentially, the read-write permission to HDFS path for the table in SQL is used to determine if the user can perform DDL/DML operations.
- HDFS way: You can use Ranger to add access control over HDFS files specific to the underlying HDFS path of the Hive table.
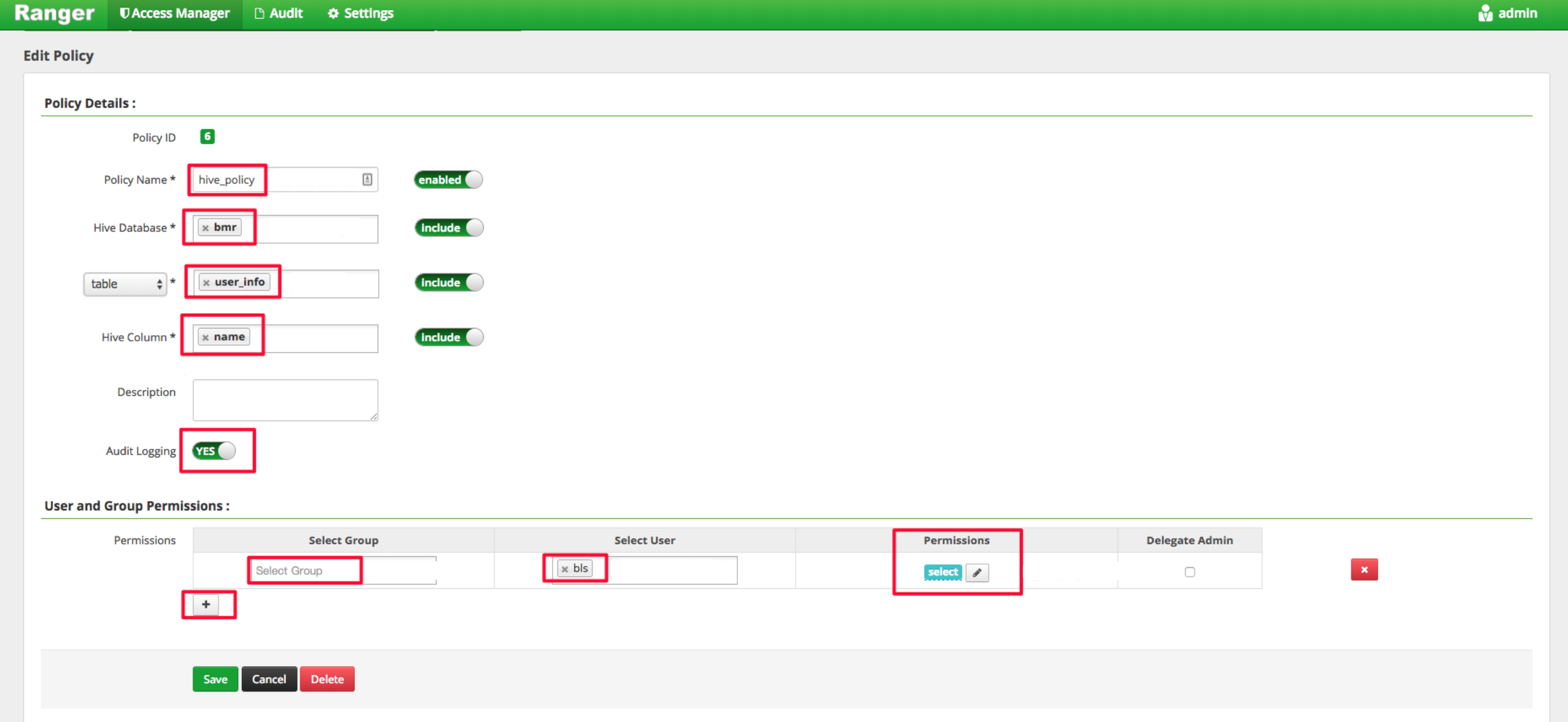
Specific to the application scenario of HiveServer2, the ranger can set permissions to Hive table/column. As the following figure shows, you can click Hive Service created by default and enter the policy configuration administration page to configure the policies.
For example, you can grant bls user the select permission to the name field of table bmr.user_info.
The ranger is only valid for access control over hiveServer2, and the beeline tool is taken as an example to describe how to access hiveServer2. Firstly, we connect hiveServer in the following way. If security mode is enabled, you need to configure the principal.
/opt/bmr/hive/bin/beeline -u "jdbc:hive2://localhost:10000/default;principal=yarn/ng6c79765-master-instance-fh2qdy0g.novalocal@BAIDU.COM"The following exception is reported if the bls user without Hive action permission creates a database:

When you grant the bls user the select permission to the name field of bmr.user_info, please query the following:

The following exception is reported in case of execution of select *:

YARN Configuration
Log in to Ranger administration interface as the following figure shows, click yarn service created by default, and enter the policy configuration administration page to configure the policies.
By default, no users other than holders of yarn service accounts can submit steps to the queue. For example, the following exception occurs when hdfs submits steps:

The following figure shows how to permit holders of hdfs and bls accounts to submit steps to yarn’s root.default queue resources.
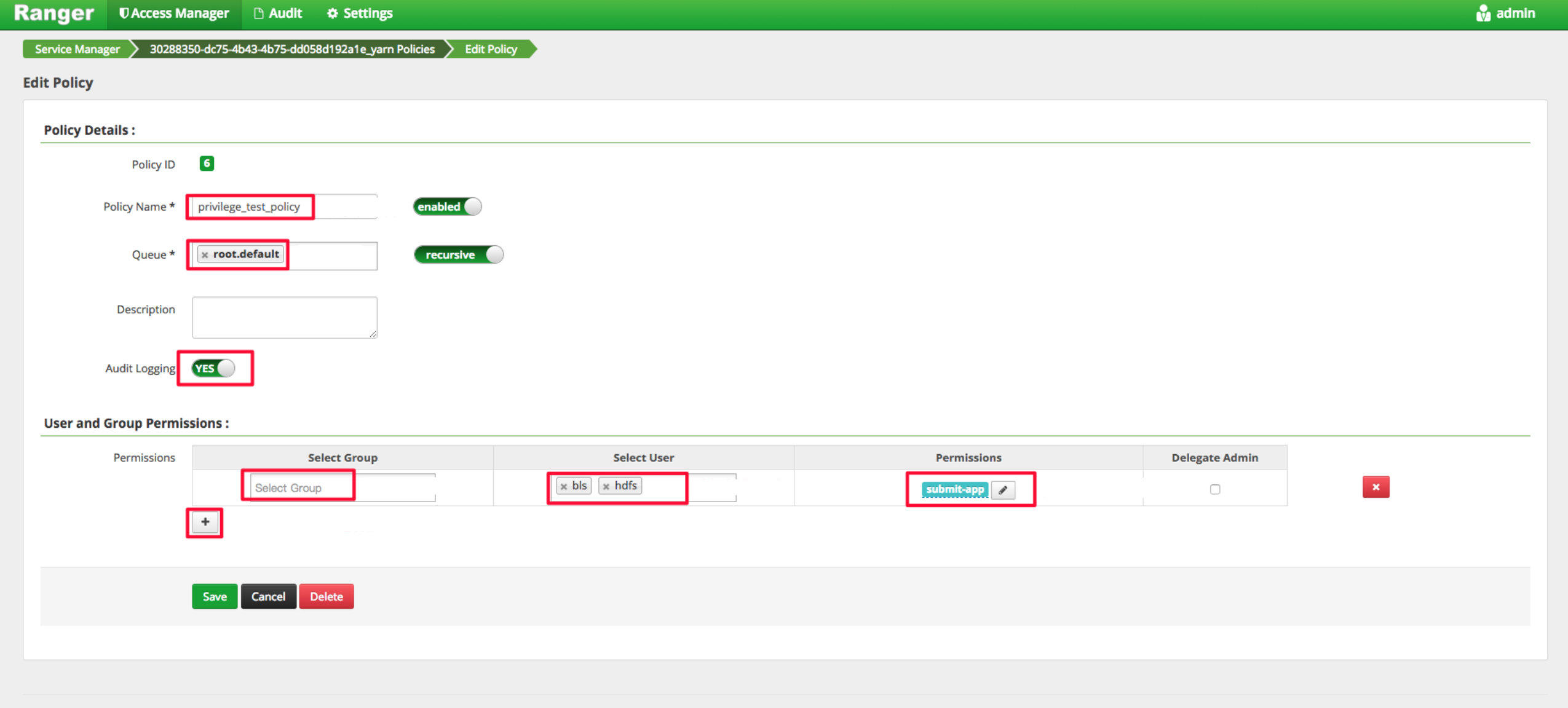
After obtaining the permission, the holder of hdfs account waits for a moment and then submits steps successfully, as the following figure shows:

