Cluster Security Mode
Overview
From the version 1.0.0, BMR supports the creation of a cluster of security types, that is, the open-source components in the cluster are started up in Kerberos's security mode, and in that security environment, only the verified client has access to the services in the cluster (e.g., HDFS and HIVE).
Note: In the current version of BMR, the components such as HDFS, YARN, SPARK, HIVE, and HBase support Kerberos.
Create Secure Clusters
Enable the security mode under the configuration tab of the cluster creation page, as the following figure shows:
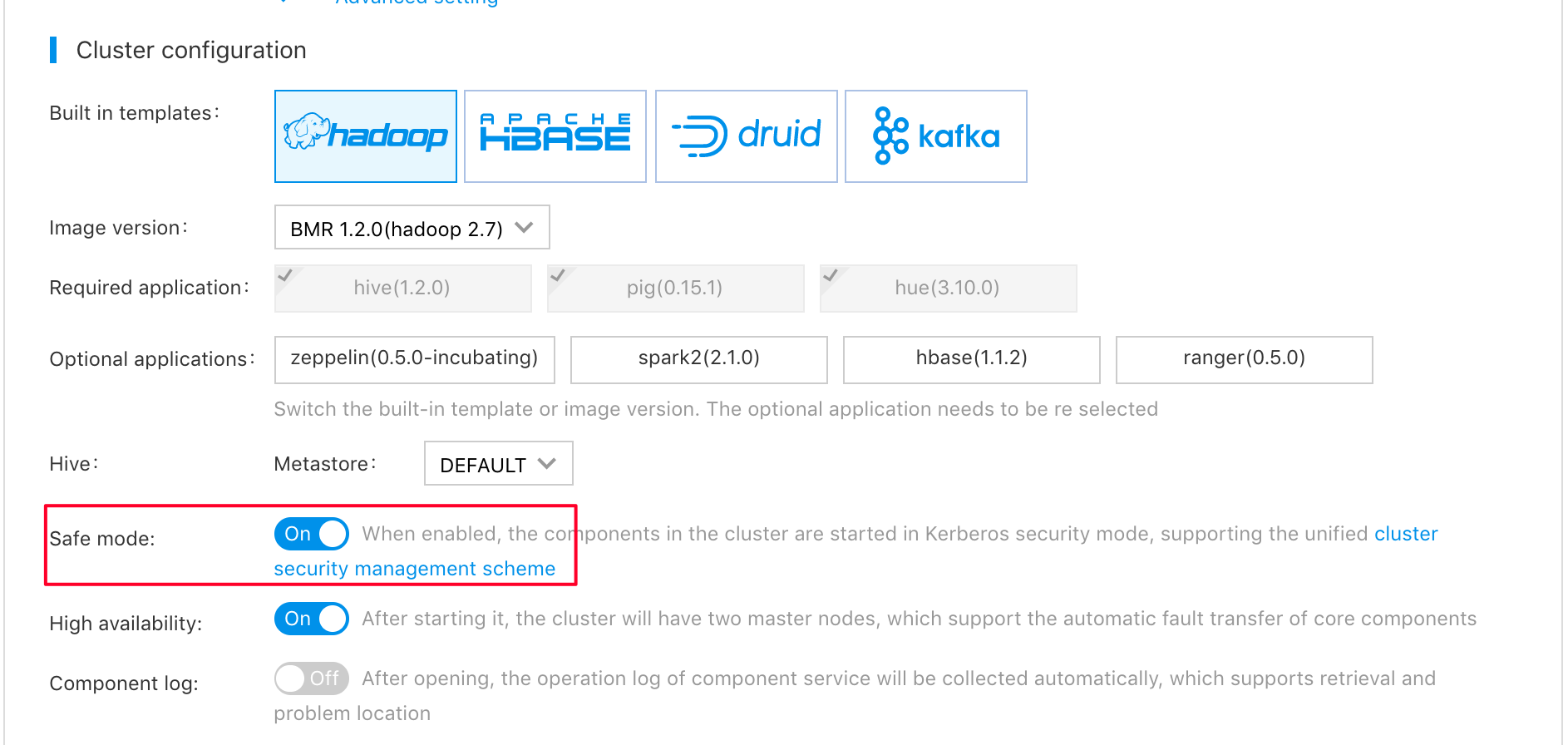
Kerberos Identity Authentication Principles
Kerberos is an identity authentication protocol based on symmetric key technologies. As an independent third-party identity authentication service, it provides identity authentication to other services and supports SSO (access to services such as HBase/HDFS after the client identity authentication).
The Kerberos protocol consists of two phases. The first phase is KDC's identity authentication to the Client, and the second phase is Service's identity authentication to the Client.
KDC's Identity Authentication to Client
Before the access to any service integrating Kerberos, the client user (principal) needs to pass the identity authentication of KDC (kerberos's server program). After passing the identity authentication of KDC service, the client user obtains a TGT credential (Ticket Granting Ticket, valid for 24 hours by default), which is used for the later access to the services integrating kerberos.
Service's Identity Authentication to Client
When the client user accesses the Service integrating kerberos, the Client uses the TGT and the name of the Service to access (such as HDFS) to obtain the TGS (Ticket Granting Service) from KDC and then uses the TGS to access the Service. Based on the information, the Service authenticates the identity of the Client, and the latter can access the Service after passing the authentication.
Guide on Kerberos General Commands
Administrator Login
Log in to administrator account: In the case of the BMR cluster node, the root account allows for the direct login through the kadmin.local command.
$ kadmin -p admin/admin
Password for admin/admin@BAIDU.COM: (BMR cluster’s default password: hadoop)Add, Delete, Change and View Accounts
In the administrator state, you can use the addprinc/delprinc/modprinc/listprincs command to administer the users. You can use "?" to list all commands.
# add allen users
kadmin: addprinc allen
Enter password for principal "allen@BAIDU.COM":
Re-enter password for principal "allen@BAIDU.COM":
Principal "allen@BAIDU.COM" created.
# generate keytab for user allen: Use the xst command or the ktadd command
kadmin: ktadd -k /etc/security/keytabs/allen.keytab allen
Entry for principal allen with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/keytabs/allen.keytab.
Entry for principal allen with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:/etc/security/keytabs/allen.keytab.View Users of Current Authentication
$ klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: admin/admin@BAIDU.COM
Valid starting Expires Service principal
2018-09-27T12:06:07 2018-09-28T12:06:07 krbtgt/BAIDU.COM@BAIDU.COMAuthenticate Users Through keytab Files
kinit -kt /etc/security/keytabs/allen.keytab allen
Delete Caches of Users of Current Authentication
kdestroy
BMR Secure Cluster Practices
If the KDC service is initially used, the cluster administrator needs to log in to the master machine, and then executes the kadmin.local command to create the principal and password (or to generate the keytab file, with attention to the owner and access privilege of the file) for the client user.
BMR cluster uses the MIT KDC, so the created client user principal needs to have the one-to-one mapping relation with the UNIX account. The mapping is especially important to the deployment of BMR clusters containing Ranger components because the Ranger UserSync in BMR adopts the UNIX account synchronization mechanism.
For example, the administrator firstly creates the UNIX user allen in the nodes of the BMR cluster:
$ useradd allen
After then, the administrator adds a principal named allen/_HOST@BAIDU.COM as follows:

Log in to the UNIX allen account, In the case of requirements for submitting steps to the cluster's YARN queue resources, make sure the account exists in all nodes of the cluster when the security mode is enabled. Otherwise, the user is notified of the submitted yarn tasks not existing, and such tasks fail to run. After then, execute the kinit command to obtain the initially valid TGT credential (valid for 24h by default).

Access the services in the cluster (e.g., HDFS, YARN, and HIVE) after the kerberos authentication.
