Identity and access management
Basic concepts
The Cloud File System (CFS) has been integrated with the Baidu AI Cloud IAM platform, allowing users to create IAM users for refined management and use of cloud services.
Baidu AI Cloud IAM users have these features:
- All IAM user resources are owned by the primary account. While IAM users with specific permissions can create resources, the billing responsibility remains with the primary account.
- IAM users can independently access and utilize the management console and APIs.
- The primary account can grant permissions to IAM users. In IAM, this is achieved by associating policies with users, and a single IAM user can have multiple policies assigned.
IAM user application scenarios
Users can utilize CFS resources on Baidu AI Cloud more flexibly through the IAM user system.
- Enterprise IAM user management and permission separation: Enterprise A has acquired various cloud resources (such as BCC instances, CFS instances, BLB instances, BOS storage, etc.) using its Baidu AI Cloud account. A’s employees need to manage these resources, including tasks like purchasing, operations and maintenance, and deploying applications online. Employees in different roles have diverse responsibilities requiring specific permissions. For security reasons, A opts not to share the root account's access keys directly with employees but instead creates IAM users corresponding to their roles. IAM users can only operate resources within the scope of their permissions and do not require separate billing. All charges are attributed to A’s root account. At any time, A’s root account can revoke the permissions of IAM users or delete them as necessary.
- Cross-enterprise resource operation and authorization management: Let A and B represent different enterprises. Enterprise A has acquired various cloud resources (such as BCC, CFS, BLB, BOS, etc.) to support its business. To focus on its core operations, A delegates tasks such as resource maintenance and monitoring to Enterprise B. Enterprise B can establish IAM users for its employees, assigning them appropriate permissions to manage A's resources efficiently. A’s resources remain under its control, as it can revoke B’s access if their partnership ends.
Policy description
CFS provides two policy modes on the cloud: system policy and custom policy.
System policy: After being authorized by the primary user, IAM users can perform corresponding operations on all CFS resources under the primary user’s name. There are three types of system policies as follows:
- CFSFullControlAccessPolicy: Grants full management permissions for the Baidu AI Cloud File System (CFS).
- CFSOperateAccessPolicy: Grants permissions for the maintenance and operation of the Baidu AI Cloud File System (CFS).
- CFSReadOnlyAccessPolicy: Grants read-only access to the Baidu AI Cloud File System (CFS).
The permissions corresponding to the three system policies and their API mappings in CFS are as follows:
| System policies | Operable APIs |
|---|---|
| Management | All CFS read operation APIs and write operation APIs |
| Operation and maintenance | All CFS read operation APIs , some CFS write operation APIs, including the following: |
| Read-only | All CFS read operation APIs |
Custom policies: The primary user can authorize sub-users with custom read-only and operation and maintenance permissions, or authorize specific operation permissions. The supported specific operation APIs are as follows:
| Operation type | Specific operation APIs |
|---|---|
| Read operations | DescribeCfs: Query CFS details |
| GetCfs: Get CFS list | |
| DescribeMountTarget: Query mount point details | |
| ListTagResource: Query CFS resources associated with tags | |
| More read operations are being supported... | |
| Write operations | CreateCfs: Create a CFS |
| DropCfs: Remove a CFS | |
| UpdateCfs: Update CFS | |
| UpdateTagAssociation: Update CFS Tag | |
| CreateMountTarget, create a mount target | |
| DropMountTarget: Delete a mount target | |
| UpdateMountTarget: Update a mount target | |
| CreateAccessGroup: Create access group | |
| DropAccessGroup: Delete access group | |
| UpdateAccessGroup: Update access group | |
| CreateAccessRule: Create access group rule | |
| DropAccessRule: Remove permission group rule | |
| UpdateAccessRule: Update access group rule | |
| RecoverBackup: Restore backup | |
| AddItemToShoppingCart: Add storage package to cart | |
| More write operations are being supported... |
Operation steps
- Click the account avatar in the upper right corner and select Multi-user Access Control.
- Select Policy Management to enter the Policy Management page, then click Create Policy.

- If you want to create a custom permission policy for read-only or operation and maintenance, select Create via Policy Generator. On the Policy Generator page, set the policy name and description, select File Storage CFS in the service, and set the permission effect (allow or deny are supported), operations (read-only or operation and maintenance are supported), resources, conditions (time, ipAddress, sourceVpc are supported), etc.

- If you want to create a permission policy for specific operations, select Create via Policy Syntax. On the Create Permission Policy page, set the policy name, description and custom policy content.
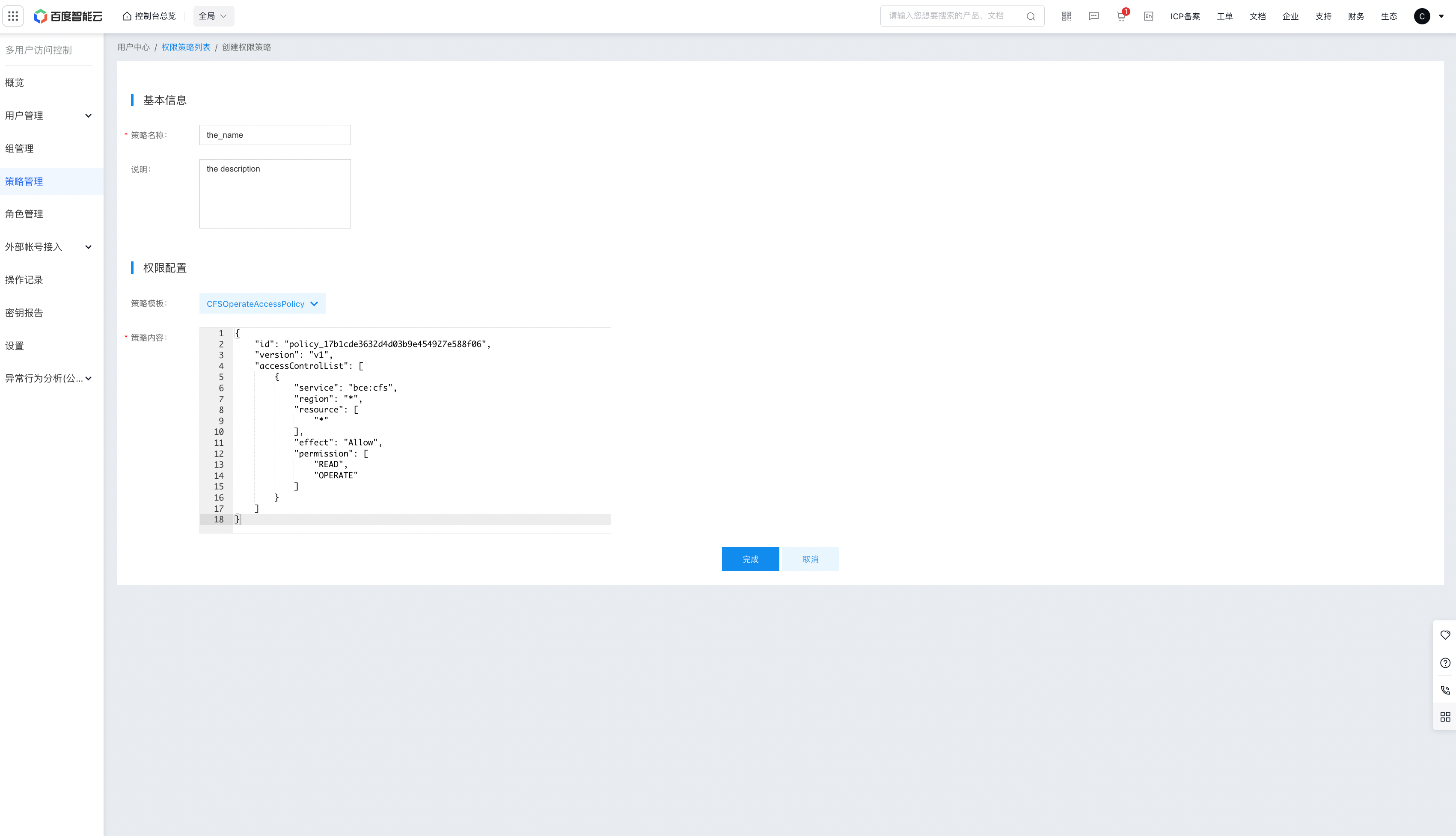
1# Policy example: Prohibit sub-users from deleting CFS file systems
2{
3 "id": "policy_ea5e180cf9c34ed9be78449d76765f4a",
4 "version": "v1",
5 "accessControlList": [
6 {
7 "service": "bce:cfs",
8 “region”: “*”, ## Region, such as bj, bd, * (all regions), etc.
9 "resource": [
10 "*"
11 ],
12 “effect”: “deny”, ## Effects, such as allow and deny
13 “permission”: [ ## Operation, the specific operation APIs currently supported for setting can be found in the policy description chapter
14 "DropCfs"
15 ]
16 }
17 ]
18}- Once being created, the newly created custom policy will be displayed in the Permission Policy List .
- On the User Management - Sub-users page, select the corresponding sub-user, click Edit Permissions, check the permissions you want to grant to the sub-user, and click OK to assign the permissions to the sub-user.
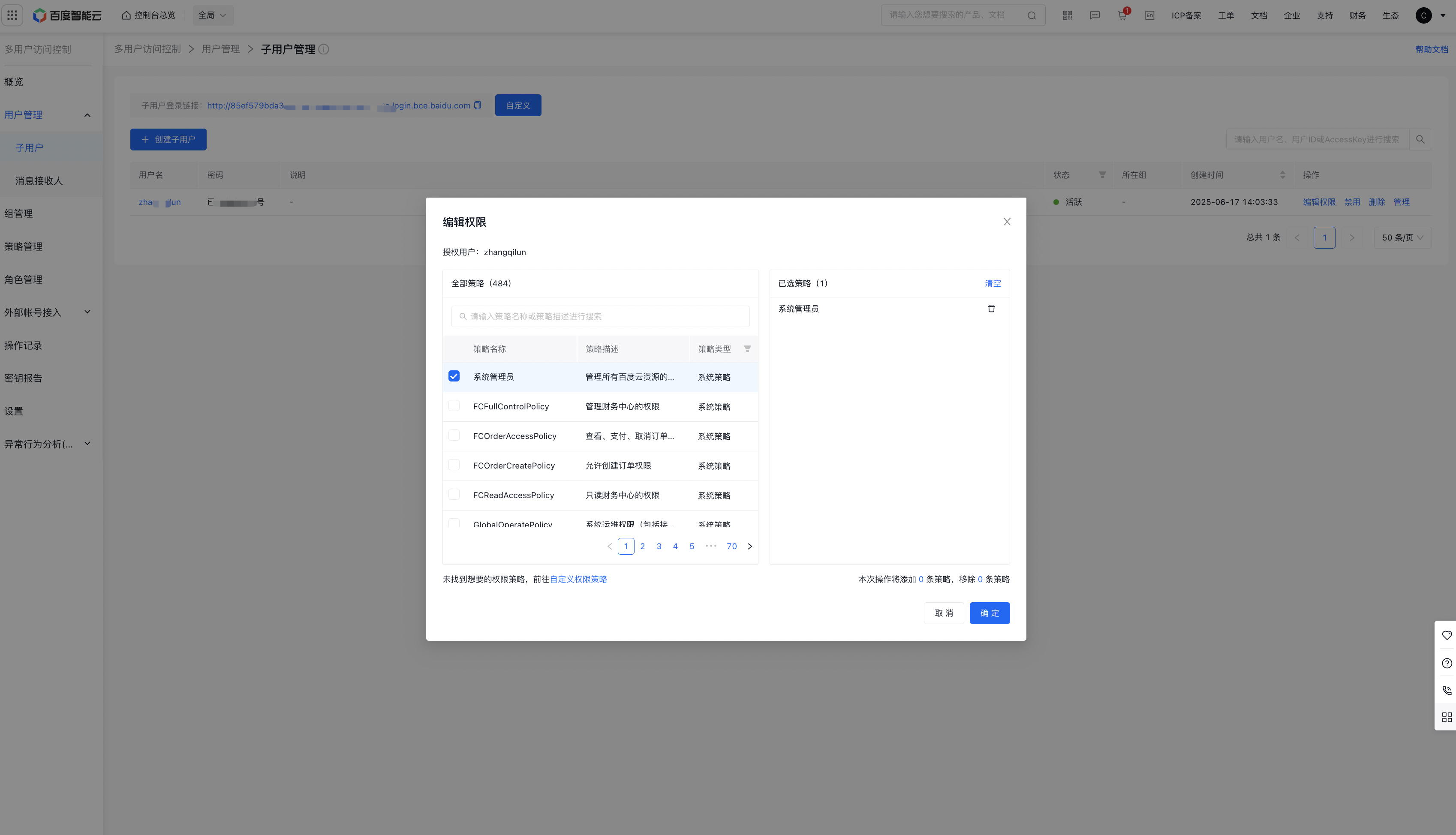
- If you want to delete the sub-user’s permissions, follow the same steps as Step 4: delete the corresponding permission from the selected policies and click OK to remove this permission from the sub-user’s permissions.
