Identity and Access Management
Introduction
Identity and Access Management (IAM) is mainly used for Baidu AI Cloud's identity management and access control to solve the problems of centralized authorization and management of cloud accounts, resource sharing and multi-user collaboration. IAM is applicable to different functional roles in the enterprise. You can give different employees different rights to the product to share resources in your account and complete their work. When your business needs multiple users to work together and share resources, it is recommended that you use IAM.
The following are typical scenarios for IAM:
- Medium and large enterprise customers: Centralized resource and authority management of different employees in multiple departments within the company;
- Independent Software Vendor (ISV) or SaaS Vendor: Centralized resource and authority management of agency clients;
- Small and medium developers or small businesses: Add project members or collaborators for resource and authority management.
Create User
- After the master account user logs in, select "Identity and Access Management" on the console to enter the user management page.
- In the pop-up "Create User" dialog box, fill in the "User Name" and confirm, and return to the "Sub User Management List" region to view the newly created sub user.
Configure Policy
CNAP supports system policies and custum policies to control its product-level privileges and workspace-level privileges, respectively.
- System policies: A set of privileges predefined by Baidu AI Cloud System to manage resources. They can directly authorize sub-users. Users can only use them and cannot modify them.
- Custum policies: A more detailed set of privileges created by users themselves to manage resources. They can be configured for a single work space so as to more flexibly meet the account's differentiated privileges management for different users.
System policy
The system policy covers three privileges: management, read and write, and read-only. The scope of privileges is as follows:
| Policy name | Privilege description | Scope of privilege |
|---|---|---|
| CNAPFullControlPolicy | Full control over CNAP | Workspace change and review, cluster resource change and review, application environment change and review, application change and review, repository change and review, configuration change and review, component change and review, microservice change and review |
| CNAPWritePolicy | Read and write CNAP | Workspace view, cluster resource view, application environment change and view, application change and view, repository change and view, configuration change and view, component change and view, microservice change and view |
| CNAPReadPolicy | Read-only CNAP | Workspace view, cluster resource view, application environment view, application view, repository view, configuration view, component view, microservice view |
Custum Policy
Self-defined policy conducts authorization from the workspace dimension. Unlike system policy, it only takes effect on selected workspace.
Sub-users first enter [Policy Management] through the left navigation bar, switch to the [Custum policy] type, and then click "Create Policy", where the policy generation method is the policy generator. After entering the policy creation page, click [Add privilege]. Users fill in the policy name and select the service type as Cloud-Native Application Platform (CNAP), and then select [Workspace] and privileges.
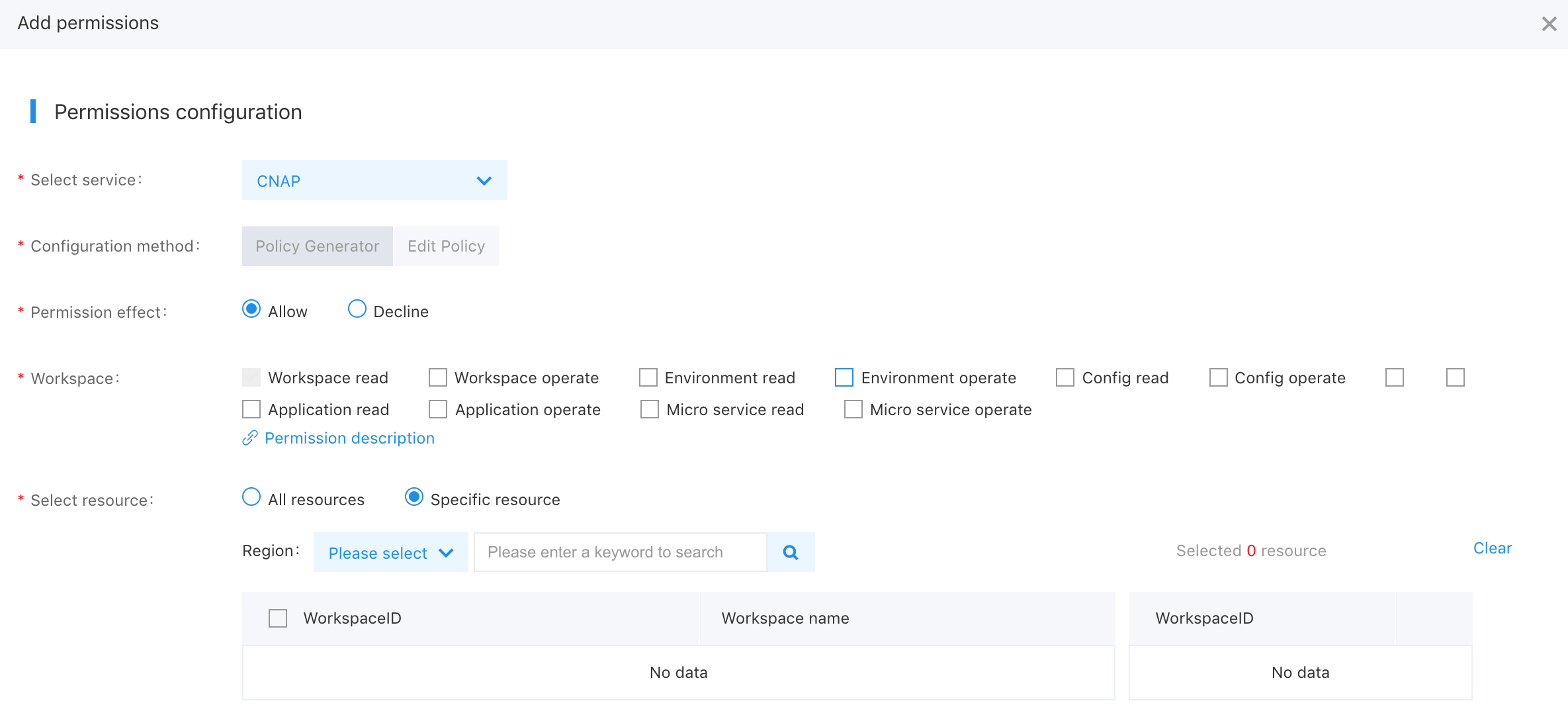
The details of custum privileges are as follows:
| Privilege description | Scope of privilege | Whether to support all resource types only |
|---|---|---|
| Workspace change | Workspace creation, update, deletion | No |
| Workspace read-only | Read workspace details, read space application list, view tracking events | No |
| Cluster change | Creation, update and deletion of cluster | Yes |
| Cluster read-only | View cluster list | Yes |
| Environmental change | Creation, update and deletion of environment | No |
| Environment read-only | View environment list, read environment details | No |
| Configuration change | Creation, update, deletion and release of configuration information | No |
| Configuration read-only | View configuration information, view configuration version, view configuration effective range | No |
| Repository change | Creation, update and deletion of image repository | No |
| Repository read-only | View list of image repository | No |
| Apply change | Application, deploy group, access mode, creation, update and deletion of online change order, using webshell | No |
| Application read-only | View application, deploy group, access mode, online order, and view container log | No |
| Micro service change | View service list, micro service instance list, service details, service ip information, service governance (routing, throttling, circuit break) rule | No |
| Micro service read-only | Service governance rule (routing, throttling, creation, update and deletion of circuit break; | No |
| Component change | Creation, update and deletion of component | Yes |
| Component read-only | View component list | Yes |
User Authorization
Select "Add privilege" in the "Action" column of the corresponding sub-user in the "User Management > Sub-User Management List Page", and select system privileges or custum policy for users to authorize.
Note: You can only delete existing policies and add new policies to modify the privileges of a sub-user without modifying the existing policy rules. You cannot uncheck the policy privileges that have been added.
Sub-user Login
After the master account authorizes the sub-user, the link can be sent to the sub-user; the sub-user can log in to the management console of the master account through the IAM user login link, and operate and view the master account resources according to the authorized policy.
For other detailed operation, please see Identity and Access Management.
