Common scenarios
Roles are commonly used to address cross-account resource access and temporary authorization issues for IAM users within the same account, without sharing user credentials. This section introduces several typical use cases.
Authorize third-party accounts to access your cloud resources
Users can authorize third-party accounts to grant permissions to their IAM users or services, allowing them to assume roles in your cloud account and access authorized resources. Similarly, users can switch to roles granted by other cloud accounts to access their resources.
The following practical example illustrates how to achieve cross-account resource access:
Company A has created Account111111111 in Baidu AI Cloud and deployed a BCC server, Server001, in this account. The administrator of Company A wants to delegate the operation and maintenance of this server to Company B, which owns account Account222222222.
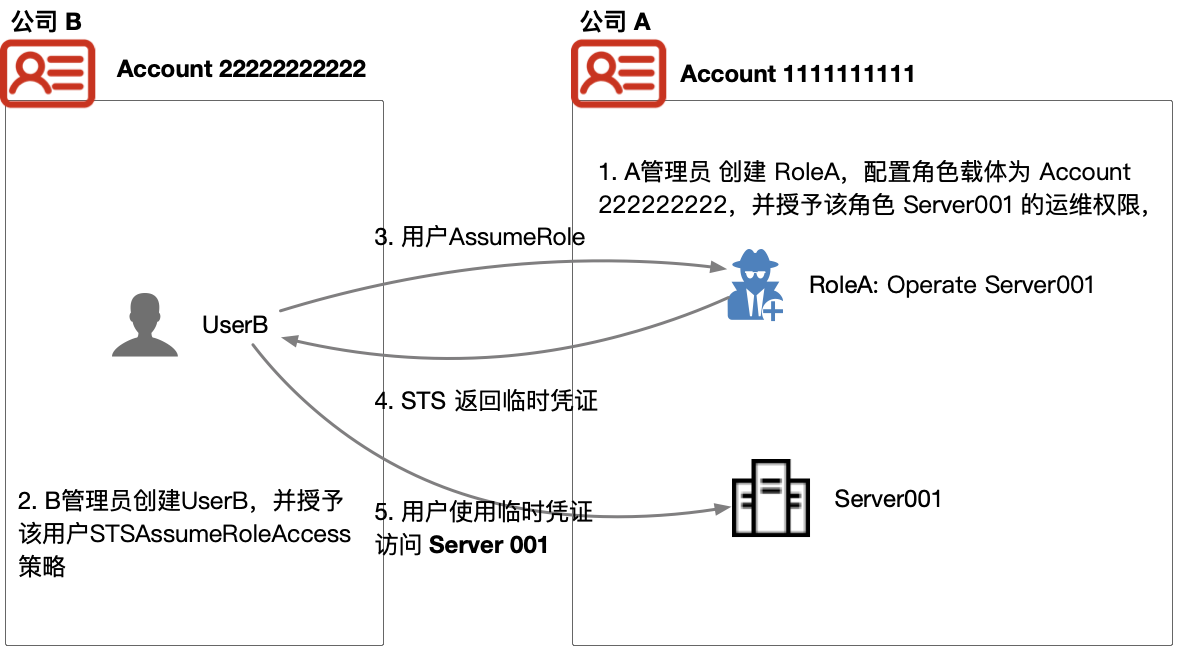
To satisfy Company A's management requirements in this scenario, the following steps are required:
- Company B provides its cloud account ID or alias to Company A's administrator;
- Company A’s administrator creates RoleA in Account111111111, sets the role entity to other cloud accounts, and enters Company B's cloud account ID or alias;
- Company A grants the Server001 operation and maintenance policies to RoleA;
- Company B's administrator created an IAM User named UserB and granted the user the _STSAssumeRoleAccess_ policy;
- UserB can switch to RoleA by calling [Security Token Service (STS)](IAM/API Reference/STS-Related Interfaces.md)_AssumeRole_ API, thereby obtaining the permission to operate and maintain Server001.
Temporary authorization in the same account
You can grant permissions for IAM users to switch to roles within your account or to roles in third-party accounts that trust you.
The following example illustrates how roles solve intra-account permission elevation:
If your account contains a core BCC server instance and, for security reasons, you are not willing to allow your IAM users to directly manage it (e.g., deletion) via the console, you may grant the server management permission to a role (refer to [Create Role](IAM/Operation guide/Role Management/Create role.md) for details) and authorize specific IAM Users to assume the role (refer to [Use Role](IAM/Operation guide/Role Management/Using Roles.md) for details). This adds the following layers of protection to the server instance:
- You must explicitly grant the IAM user the permission to assume this role
- The current IAM user must use the API of Baidu AI Cloud to assume the role
This method follows the principle of least privilege, ensuring higher-security permissions are only granted when users perform specific tasks, reducing the risk of unintentional actions or modifications to sensitive environments or services.
