Using Roles
Through the [Create Role](IAM/Operation guide/Role Management/Create role.md) operation, the user has obtained a role granted specific permissions, which can be used by a cloud account. This section explains, from the perspective of a trusted account, how trusted users can assume roles to access the cloud resources of the trusted account. For clarity, assume that the cloud resource and role are in account ID 111111111. The role named RoleA has operation and maintenance permissions for BCC server Server001. The trusted cloud account is 222222222, which intends to grant IAM user UserB the permission to assume RoleA.
Prerequisites
- It has
System Administratorpermissions for the trusted account 222222222; - IAM user UserB possesses valid [Obtain AKSK](Reference/Retrieve AK and SK/How to Obtain AKSK.md);
- IAM user UserB has the ID and role name of the target account.
Operation steps
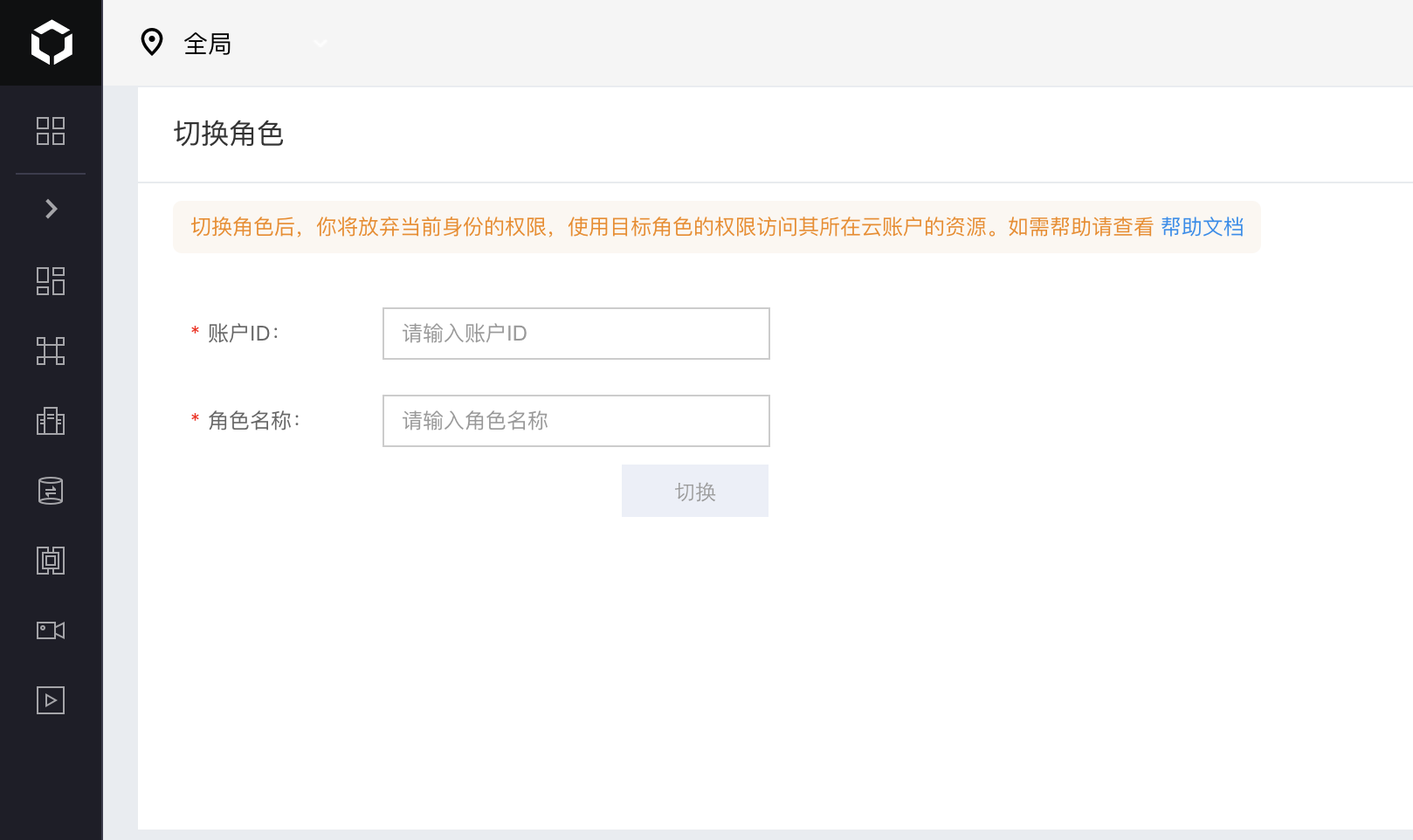
Assume role via console
- Sign in to the Baidu AI Cloud Console by administrator credentials of account 2222222;
- Grant the
STSAssumeRoleAccesspolicy permission to IAM user UserB. For specific operations, please refer to [User Authorization](IAM/Operation guide/Permission Policies/Authorization.md); - IAM user UserB signs in to the console, moves the cursor to the avatar in the upper-right corner, and clicks the Switch Role button to redirect the page;
- On the redirect page, enter the ID and role name of the target account, and then click Switch to enter the target role space;
- To return to the account where IAM user UserB is located, hover over the avatar in the upper-right corner on the page, and click the Return to UserB button.
Assume a role using API
- Sign in to the Baidu AI Cloud Console by administrator credentials of account 222222222;
- Grant the
STSAssumeRoleAccesspolicy permission to IAM user UserB. For specific operations, refer to [User Authorization](IAM/Operation guide/Permission Policies/Authorization.md); -
IAM user UserB uses the [AssumeRole](IAM/API Reference/STS-Related Interfaces.md#AssumeRole) API, replacing parameter
accountIDwith 111111111 androleNamewith RoleA, thereby assuming RoleA in account 111111111. By default, role sessions last 2 hours. When usingAssumeRoleAPI, you may specify the exact duration of parameterdurationSeconds, which cannot exceed 2 hours; - At this point, IAM user UserB will obtain temporary credentials of RoleA, temporarily relinquishing its permission in account 222222222 and gaining permission to operate and maintain Server001. When accessing Server001, you need to replace the AK/SK with the temporary
AK/SKreturned by theAssumeRoleAPI, and replace the Token with the returnedSessionToken.
