Common Scenarios
The role is often used to resolve the problems in cross-account resource access, or in temporary authorization of the IAM user in the same account, without sharing any user's credential information in your account. This section describes several common business scenarios.
Authorize Third-party Accounts to Access Your Cloud Resource
You can trust the third-party accounts, and authorize permission to IAM users or services of the account, so as to substitute in the role of your cloud account, and access to the cloud resources that the role is authorized. You can also switch to the role that you are authorized by other cloud accounts to access to the cloud resources of other accounts.
The following is a practical example on how to access the resource across accounts:
Company A creates the Account111111111 in Baidu AI Cloud, and creates BCC server Server001 under the account, and the administrator of Company A hopes to transfer the server to Company B(which has the Account222222222) for Operations.
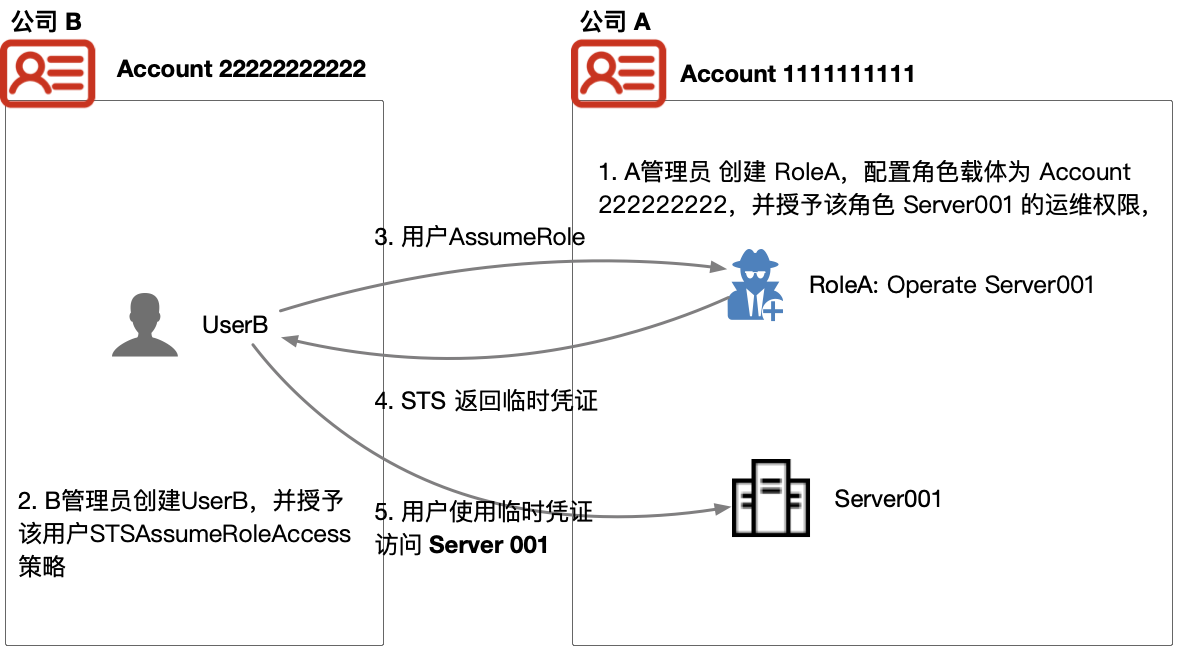
Under such scenario, the following steps are required to meet the management requirements of Company A:
1.Company B provides its cloud ID or alias for the administrator of Company A;
2.The administrator of Company A creates a new role RoleA in Account111111111, and sets the role carrier as other cloud account, and inputs the cloud account ID or alias of Company B;
3.Company A grants the Operations policy to Server001;
4.The administrator of Company B creates UserB, and grants the use with _STSAssumeRoleAccess_ policy;
5.UserB can switch to Role by calling Security Token Service (STS) _AssumeRole_ API, and then it has the permission to operate and maintain Server001.
Temporary Authorization in the Same Account
You can authorize permission to IAM user to switch to a role in your account, or a role in a third-party account that trusts you.
The following is an example on how to use the role to solve the problem in improving permission within the same account:
Assuming that your account has a core BCC server, and for the sake of security, you do not hope your IAM user to manage this server (such as deletion) through the console; at this point, you can grant the management permission of this server to a role (please refer to Create Role for detailed operations), and authorize the permission to use the role to specific IAM user, with reference to Use the Role for detailed operation, so that you can add the following protections to the server instance:
- You must explicitly grant the permission to the IAM user to perform the role
- The current IAM user must use the API of Baidu AI Cloud to substitute in the role
If the principle of minimum permission is exercised in the manner described above, only when a user needs to perform a specific task, can the permission of a higher security level be used to prevent a IAM user from automatically operating or changing a sensitive environment or service.
