Use Role
Through Create Role, you have a role that can be granted specific permission, and the role can be used by a cloud account. This section describes how to use the role as trusted user to access the cloud resources of trusted accounts from the perspective of the trusted account. For convenience of understanding, it is assumed that the account ID of the cloud resource and role is 111111111, with the role name of RoleA, and has the Operations permission of BCC server Server001; the ID of trusted cloud account is 222222222, hoping the IAM user UserB is granted the permission to substitute the role RoleA.
Prerequisite
1.Have the System Administrator permission of the trusted account 222222222;
2.The IAM user UserB has valid Access AKSK;
3.The IAM user UserB has the account ID and role name of the target account.
Operation Steps
Substitute the Role in Console
1.Use the administrator account of account 2222222 to log in the Baidu AI Cloud Console, select Identity and Access Management;
2.Grant the IAM user UserB with the policy permission STSAssumeRoleAccess. Please refer to User Authorization for specific operations;
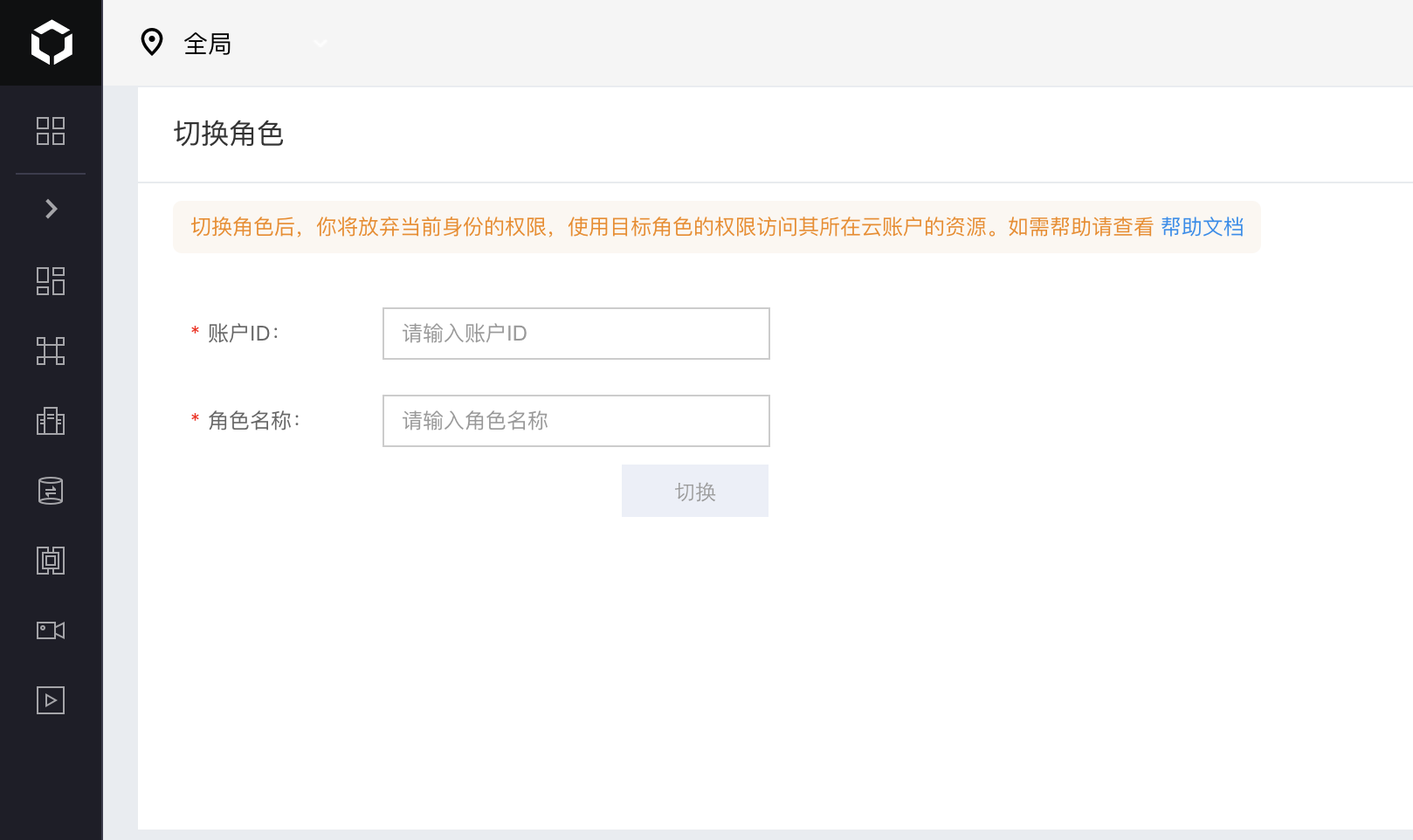
3.The IAM user UserB logs in to the console, moves the mouse to the head portrait at the top right corner of the page, and click the button Switch Identity to jump the page;
4.Input the account ID and role name of the target account, click to switch the identity and then enter the space of target role;
5.To return to the account of the IAM user UserB, move the mouse to the head portrait at the top right corner of the page, click the button Return to UserB.
Use API to Substitute the Role
- Use the administrator account of account 222222222 to log in Baidu AI Cloud Console;
2.Grant the IAM user UserB with the policy permission
STSAssumeRoleAccess. Please refer to User Authorization for specific operations; 3.The IAM user UserB replaces the parameteraccountIDwith 111111111 through AssumeRole API, with theroleNameof RoleA, which can be substituted into the account 111111111.By default, the role session lasts for 2 hours, and you can also set the specific period of validity of the parameterdurationSecondswhen usingAssumeRoleAPI, and such period of time cannot be more than 2 hours; 4.At this point, the IAM user UserB can get the provisional credentials for the role RoleA, and give up the permission in the account 222222222 temporarily, and have the permission of the Operations server Server001. When you access Server001, you need to replace AK/SK to the temporaryAK/SKreturned byAssumeRoleAPI, and replace Token toSessionTokenreturned.
