Tag-based Authorization and Authentication
Overview
Baidu AI Cloud provides public Label Management Services to facilitate the grouping management of the resources on the cloud; you can well plan the label for the resources in the account, and add the same label for the resource that needs association or the resources within the same project to improve the efficiency of the resource management.
For the labeled label, you can use label-based authorization of IAM to configure Custom Policy for the resources with association relationship quickly, and grant to the user that needs the resource permission under the label. Please refer to Product Line Supported Currently for the services that have supported the label authorization
Label-based Permission Features
The label-based authorization and authentication can provide you with the following permission management features, so as to help you improve your management efficiency:
- Grouping authorization: The rapid authorization of different service instances with association relationship;
- In the case that the service does not have the permission to create resources out of thin air, such as "Addition or Creation", etc., implement the operations out of thin air or the authorized user can get the permission to the created resources automatically;
Commonly Used Scenarios
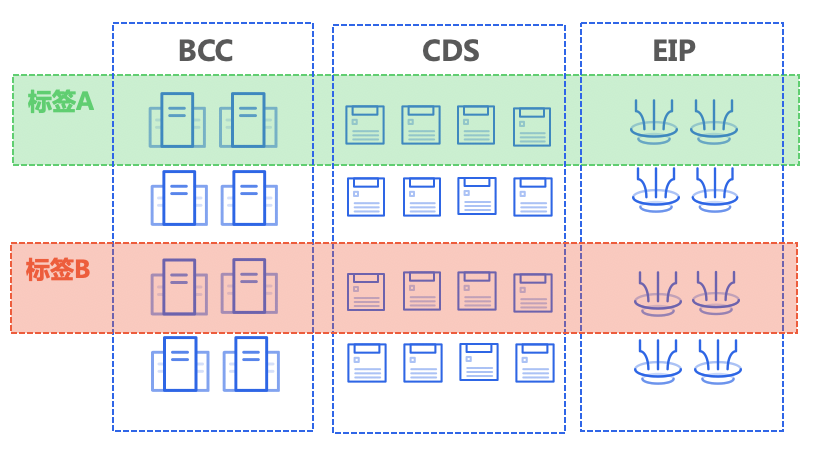
Scenario 1: Grouping management of different service resources for a large enterprise customer
When a large enterprise customer configures a new project, the enterprise needs to make plan for 60 sets of BCC and 120 blocks of CDS disks, and before the label authorization management is used, the disk relationship between BCC and CDS can only be maintained manually, but the manual allocation of resource permission for multiple users affects the efficiency greatly. After the label authorization is used, the user only needs to add the same label for the associated resources when creating BCC and CDS, and allocate the permission for the user quickly by means of label authorization; meanwhile, for the new BCC and CDS resources added in this project, the user only needs to add the same label, and his IAM user can get the permission of the new machine automatically, which can greatly improve the management efficiency.
Scenario 2: A large enterprise customer expects that its IAM user can create the CDN domain name and the get the permission of the new domain name created by himself automatically
The administrator of a large enterprise customer expects to assign the management permission of the domain name to the account of the IAM user, with the detailed requirements as follows: 1.The IAM user can add the domain name himself, and has the permission of the domain name he adds; 2.The domain name resources between the IAM users are isolated from each other; for example, IAM user A cannot view the domain name added by IAM user B without authorization; 3.The root user can view and manage the domain name added by all the IAM users;
The label authorization can meet the above-mentioned product demands, with the specific operation mode shown as follows:
Step 1.The Administrator plans the label. For example, the Administrator plans the label Key: department/Value: 123 for IAM user A, and plans the label Key: department/Value: 456 for the IAM user B, and creates corresponding label in the label management;
Step 2.The "Administrator enters IAM identity and access management>Policy Management, clicks "Create a Policy, and selects the mode to create policies as "Label-based Creation**;
Step 3.The Administrator fills in the basic information of policy. For example, the naming policy is policy_for_user_A_with_tag123, and the label Key: department/Value: 123 is selected in the permission configuration, with the service selected as "Content Delivery Network CDN" and operation as "Management permission", and the resource scope displays all the resources that have the attribute of such label, and click completion to save;
Step 4.The Administrator creates a tag456-based policy policy_for_user_B_with_tag456 according to the process specified in Step 3;
Step 5.The Administrator creates the "IAM user A, such as User A, and grants the policy permission policy_for_user_A_with_tag123 to User A; the Administrator creates the IAM user B, such as UserB, and grants the policy permission policy_for_user_B_with_tag456 to UserB;
Step 6.The Child Use UserA logs in the console, enters CDN and selects the Domain Name Management>Add a New Domain Name, such as "cloud.baidu.com", it defaults to bind the label Key: department/Value: 123 at the wizard Step 3 "Label", click completion to finish the creation of domain name; in addition, the IAM user UserA has the permission to manage the domain name cloud.baidu.com, and has no any permissions to other domain names. If the IAM user UserA needs giving the access permission to other domain names, the UserA needs additional authorization in IAM by Administrator . The IAM user UserB shares the same way.
Label-based Authentication
Essentially, the label is a condition or an attribute of the permission policy, and the label-based policy belongs to the user's custom Policy; in terms of permission type, it belongs to resource-based policy, and please refer to the Policy Authentication Evaluation Logic for the authentication evaluation logic when the user is granted with the label resource permission.
