Practice of the Security Group Configuration (Getting Started)
Introduction
The security group of Baidu AI Cloud is "Stateful Whitlist Firewall Service" applied in the cloud server, realizes the strict security control of multiple cloud services in the business traffic ingress and egress at the IP+ port level to fully guarantee the high security of users and business. This document aims to list several scenarios to demonstrate the security group white list and the application methods of stateful firewall.
Scenario 1
The users should set flexible security policies for each module of the same business system or among different business systems to guarantee a higher security of its business system.
Example scenarios
As shown in the figure below, the hierarchical business architecture includes Class A, Class B and Class C cloud servers:
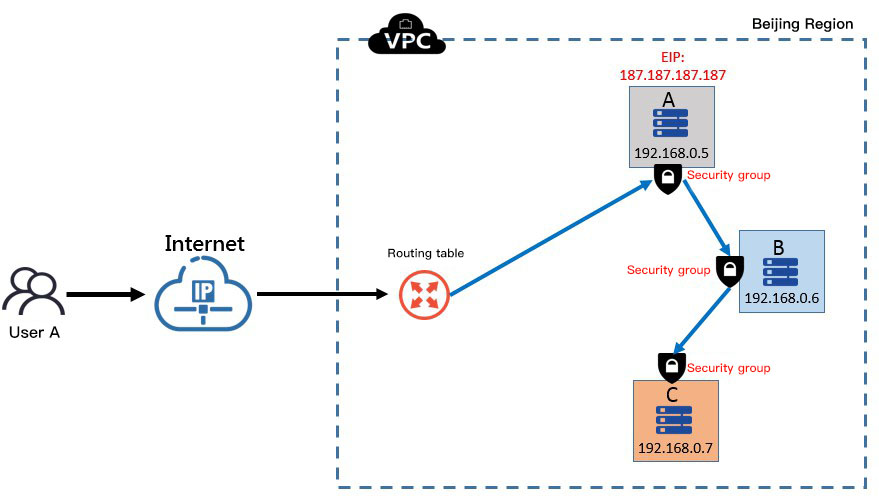
- As an access service, the Class A cloud server provides the WEB access service, and only opens 80 and 443 ports to the outside;
- As an APP server, the Class B cloud server responds to the service request transmitted from Class A server, and can only actively access the Class C server;
- As a DB service, the Class C server responds to the data operation request from the Class B server, and cannot actively access other services.
In order to guarantee the security of the architecture, different security policies should be configured for 3 servers, and the minimum access permission should be set for each business.
Operation steps
-
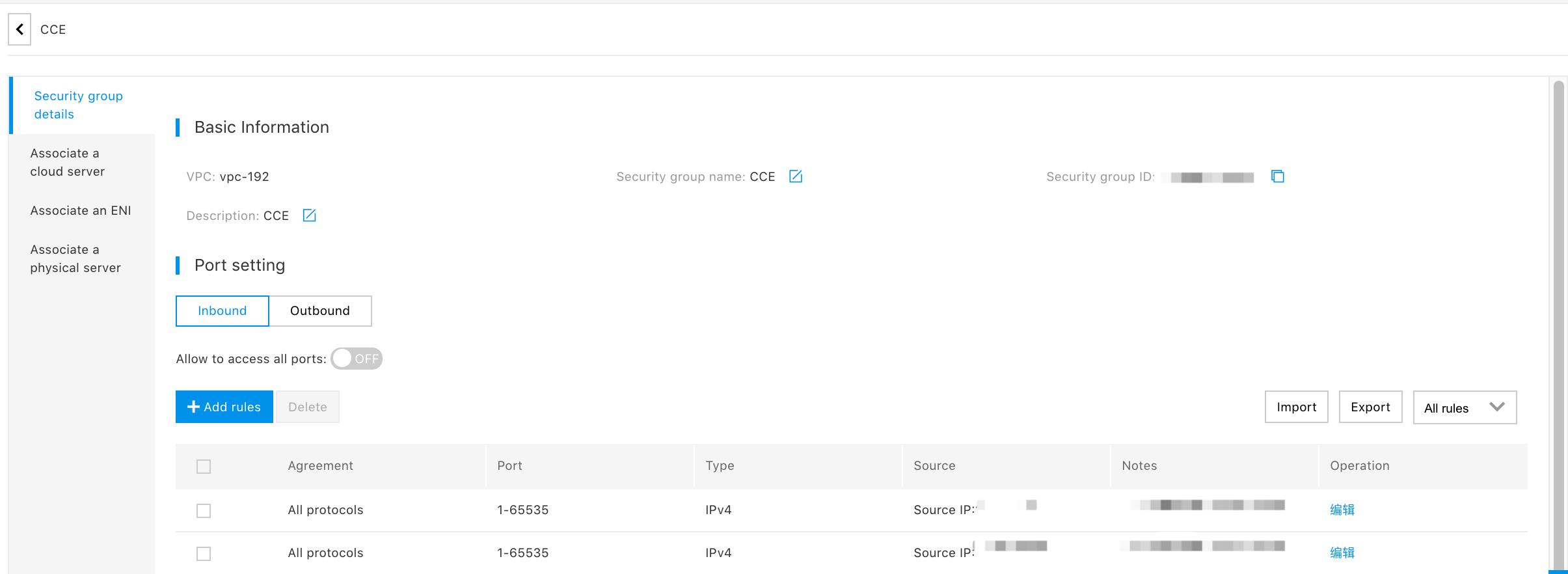
As a WEB server, the Class A cloud server opens HTTP and HTTPS services to Internet users. So a security group (AccessSG) is created and applied to the Class A server. The configuration (ingress and egress) rules for AccessSG are as follows:
- Ingress security policy for AccessSG:
- Outgress security policy for AccessSG:
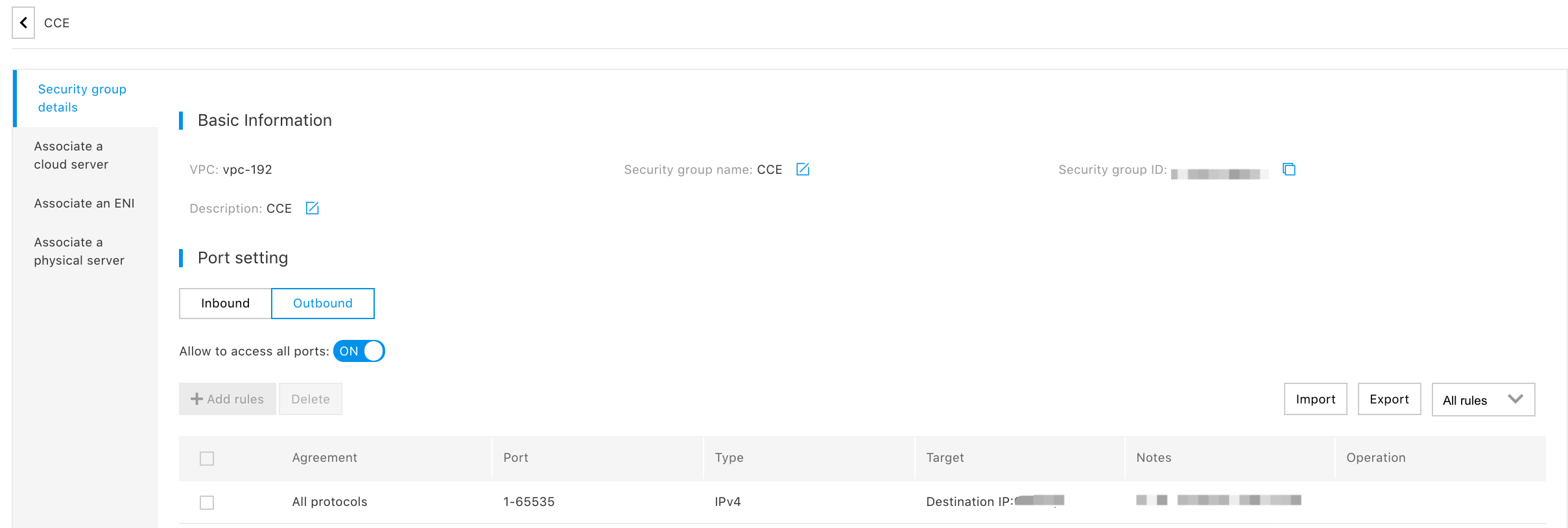
-
As an APP server, the Class B cloud server only accepts the request from the Class A cloud server, and can only actively access the Class C server. So a security group (AppSG) is created and applied to the Class B server. The configuration (ingress and egress) rules for AccessSG are as follows:
- Ingress security policy for AppSG:

- Egress security policy for AppSG:

-
As a DB server, the Class C cloud server only accepts the request from the Class B cloud server, and cannot actively access any server. So a security group (DbSG) is created and applied to the Class C server. The configuration (ingress and egress) rules for DbSG are as follows:
- Ingress security policy for DbSG:

- Egress security policy for DbSG:

The method above is used to realize the vertical layering of the system. The setting of the access permission for each business layer greatly increases the security of the system.
Scenario 2
Example scenarios
As shown in the figure below, based on [Scenario I](#Scenario I), the role of administrator is added:
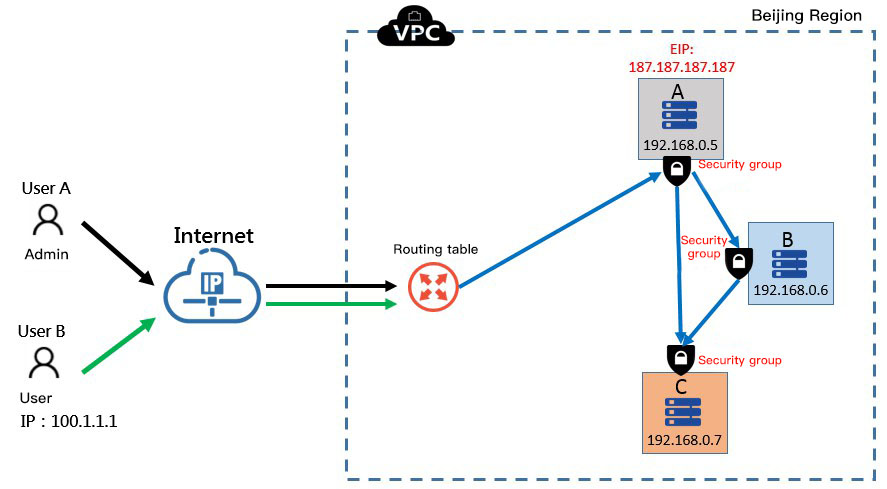
- As the access server for operation and maintenance management, the Class A server supports the daily operation and maintenance management of the administrator. The administrator can log in to the Class A, Class B and Class C cloud servers by SSH in the extranet to complete the operation and operation management. The security group rules are set for the added operation and maintenance permissions. Refer to [Scenario I](#Scenario I) for the setting of other access request permissions.
- Because of log-in by SSH, the Class A cloud server can actively access the 22 ports of Class B and Class C cloud servers in the intranet, and the Class C cloud server can still not actively access the Class A and Class B servers.
In order to guarantee the security of the architecture, different security policies should be configured for 3 servers, and the minimum access permission should be set for each business.
Operation steps
-
The Class A cloud server is the access server for operation and maintenance management. An configuration is added in the ingress of the Access security group to allow 100.1.1.1 to access 22 port, and a rule is added in the egress to allow the access to 22 port of 192.168.0.7.The configuration (ingress and egress) rules for AccessSG are as follows:
- Ingress security policy for AccessSG
- Outgress security policy for AccessSG
- Because the permission of the Class B server is not adjusted, the security rules for AppSG may not be adjusted.
-
An configuration is added in the ingress (DbSG) of the security group of the Class C server to allow 192.168.0.5 to access 22 port, and the rules in the egress of the security group doesn't change, with the configuration as below:
- Ingress security policy for DbSG
Up to this point, the Class A server becomes the access server for operation and maintenance management to enable the administrator to log in to 3 servers by SSH to complete the operation and operation management.
