Security Risk Detection
View Safety Inspection Records
Application scenarios
Users can view the number of web vulnerabilities and the number of open ports for all cloud resource instances.
Operation steps
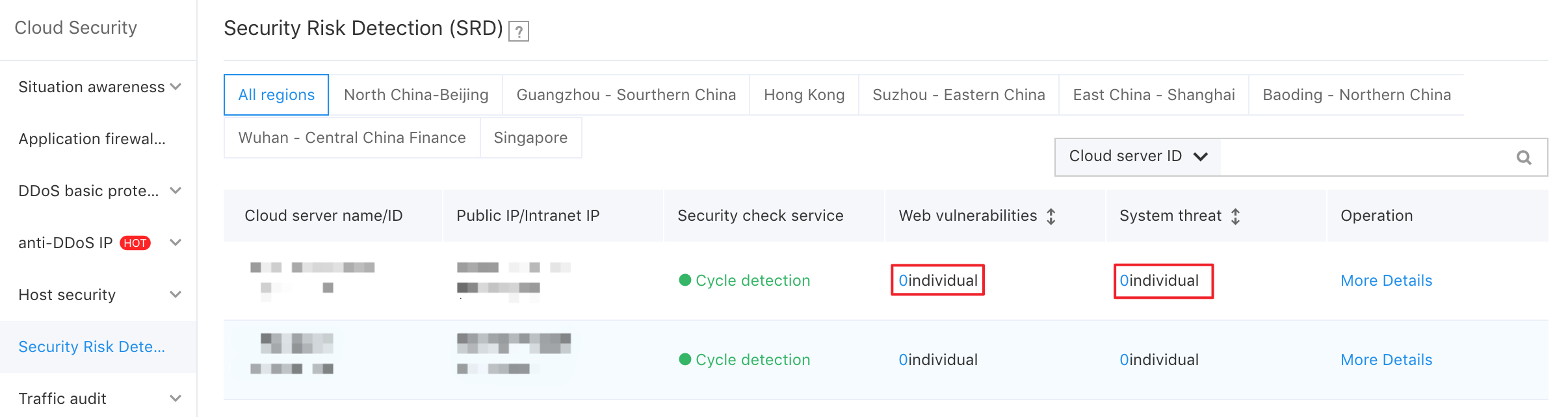
- In the left navigation, select "Security Risk Detection" to enter the inspection list.
- You can view the number of web vulnerabilities and the number of open ports of the cloud service instance. Click the corresponding data to enter the corresponding details page.
Web Vulnerability Detection
Background information
Web vulnerability detection can detect the vulnerability of user websites in real time. If vulnerabilities are found, you can verify whether the repair is complete by rechecking. By setting the notification method, users can be notified of website vulnerability information in a timely manner.
Note:
The security detection service initiates detection from the public network. Cloud servers without public IP addresses cannot be detected.
Record Web Vulnerability Detection
Application scenarios
Users can view the WEB vulnerability scan records of a single BCC instance.
Operation steps
1.In the left navigation, select "Security Risk Detection" to enter the service list page.
2.Select the instance you want to view and click "View Details" to enter the "Web Vulnerability" tab.
3.View the scan record of the corresponding instance.
Handle Web Vulnerability Detection Results
Application scenarios
Users can follow up on a web vulnerability scan record.
For a pending or ignored Web vulnerability, the supported operations include re-detection.
Operation steps
1.For the operation, please see Record Web Vulnerability Detection.
2.In the "Action" column, click
Set the Web Vulnerability Detection Result Notification Method
For details, please see Set Alarm.
System Threat Detection
Background information
System threat detection, including "Specific Software Threats" and "Weak Password Threats", prompts for ports with service vulnerabilities and the names of services running on the ports, and finally provides a repair plan.
Record System Threat Detection
Application scenarios
Users can view system threat scan records of a single BCC cloud server.
Operation steps
1.In the left navigation, select "Security Risk Detection" to enter the service list page.
2.Select the instance you want to view and click "View Details" to enter the "System Threat" tab.
3.View the scan record of the corresponding instance.
Set System Threat Scan Notification Method
Application scenarios
Users can uniformly set alarm methods and policies for different security services.
Users can set alarm methods and SMS alarm time for different security services: Email or SMS.
Operation steps
1.Select "Alarm Setting" on the left navigation to enter the "Cloud Security-Alarm Settings" interface.
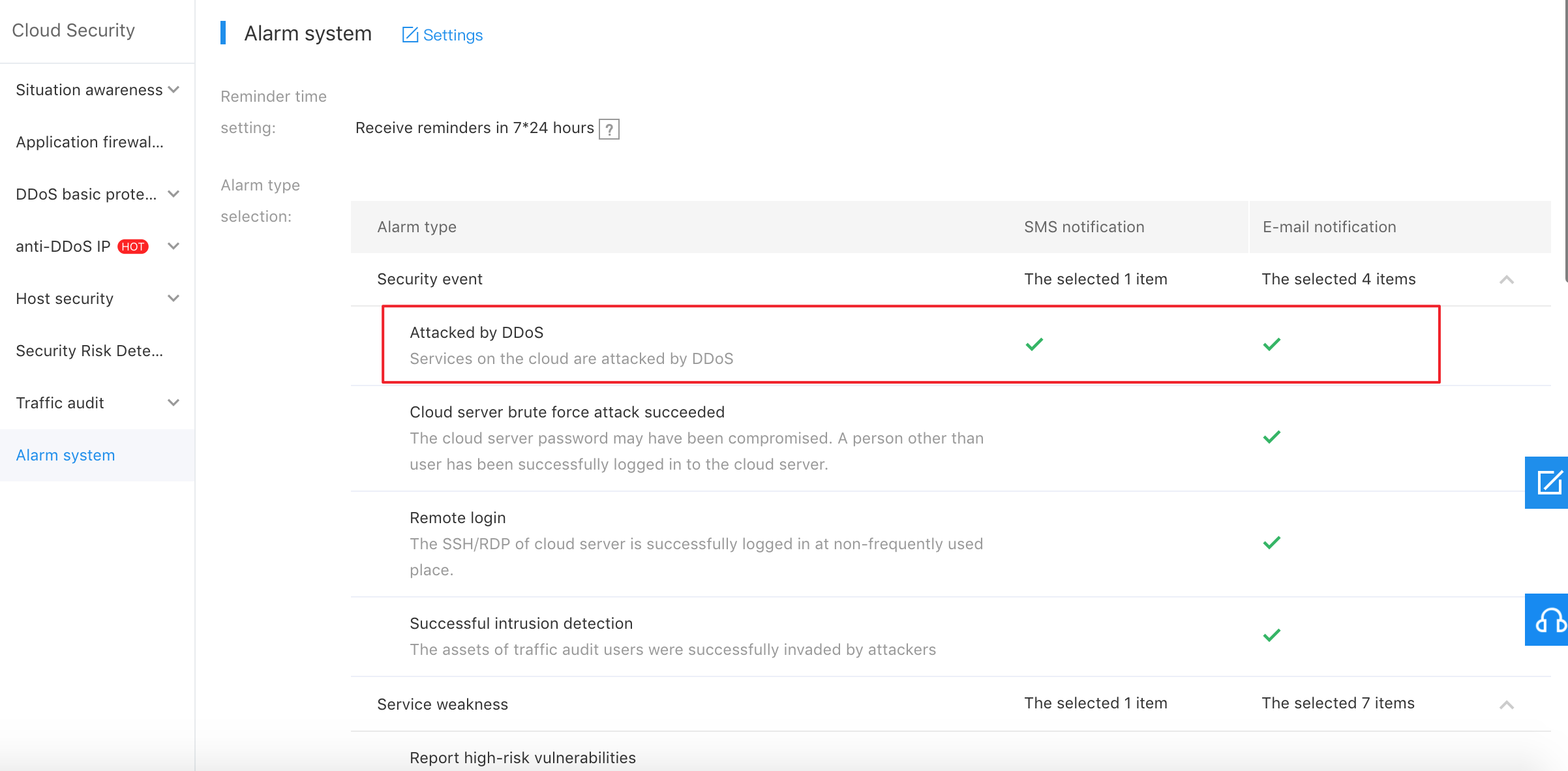
3.According to the actual situation, select the notification method, SMS or email, and set the reminder time.
4.Click "OK" to complete the alarm setting.
