Identity and Access Management
Introduction
Identity and Access Management (IAM) is used to help users manage resource access privileges under cloud accounts. The IAM applies to different roles in the enterprise and can grant different employees different privileges of using products. If any resources need multi-user collaborative operation in your enterprise, you are highly recommended to use the IAM.
The IAM applies to the following scenarios:
- Medium and large-sized enterprises: Grant multiple employees the authorization for management in the enterprise;
- Technology-based vendors or SAAS platform providers: Perform resource management and access control for proxy customers;
- Small and medium developers or small-sized enterprises: Add project members or collaborators to perform resource management.
Create a User
- After the primary account user logs in to its account, it selects the "Identity and Access Management" in the console to enter the user administration page.
- Click the "User Administration" in the left navbar, and then click the "New User" on the "Sub-User Administration List" page.
- In the pop-up "New User" dialog, enter and confirm the "User Name", and then return to the "Sub-User Administration List" area to view the created sub-user.
Configure a Policy
DCC supports both the system privilege policy and user-customized privilege policy to realize privilege control of DCC at product and instance levels respectively.
- System privilege policy: A set of privileges predefined by the Baidu AI Cloud system for resource management. This policy enables the system to grant sub-users privileges directly, and users can only use them without modification.
- Custom privilege policy: A set of privileges created by users for the refined resource management. This policy enables the system to configure single instances to flexibly manage different user privileges required by different accounts.
System privilege policy
The system privilege policies are divided into three categories, that is, the privilege management policy, privilege operation policy and read-only privilege policy. The detailed privilege scope is as follows:
| Policy Name | Privilege Description | Privilege Scope |
|---|---|---|
| DCCFullControlPolicy | Privilege for full control and management of DCC | The management privilege includes the following operations, such as creating, deleting, managing, enabling and disabling products. Meanwhile, all product management APIs need to be managed uniformly in terms of finance. |
| DccOperateAccessPolicy | Privilege to operate the DCC | The operation privilege includes the following operations, such as creating, deleting, managing, enabling and disabling products. |
| DccReadAccessPolicy | Privilege to only read the DCC | The read-only privilege mainly include listing resources and displaying resource details and status. |
Custom privilege policy
The custom privilege policy is authorized from the instance dimension. Unlike the system privilege policy, it is only effective for the selected instances.
The first enter "Policy Management" from the left navbar, and then click "Create a Policy". Afterwards, the user needs to enter a policy name and select the service type for the DCC. By default, the policy is generated by the policy generator without any modification.
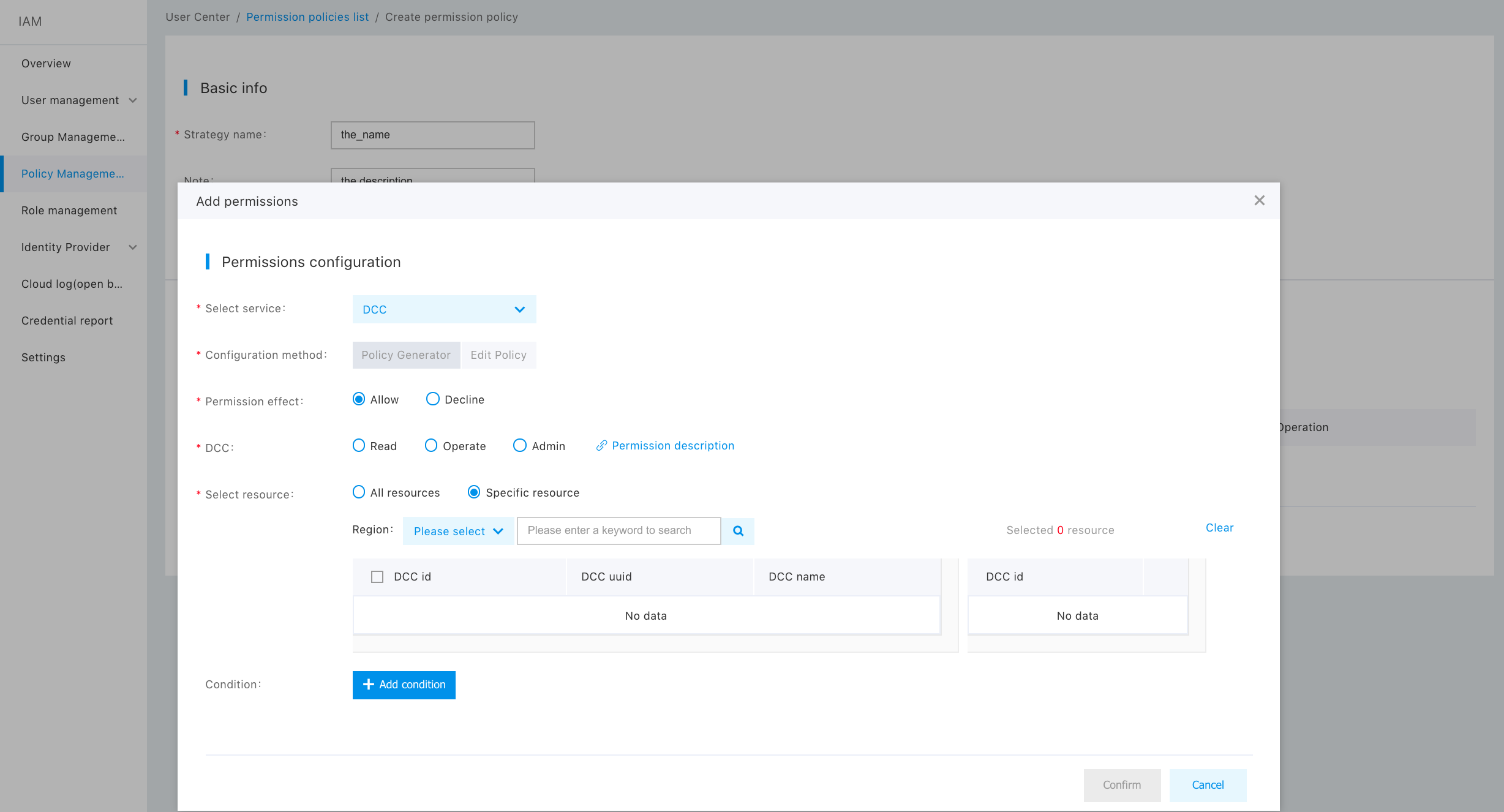
The custom privilege scope is explained in details as follows:
The privilege of the DCC is described as follows:
| Operation Type | Privilege Scope |
|---|---|
| Read-only operation | View and download the DCC list and its tag |
| OPS operation | DCC: |
The instance privilege is described as follows:
| Operation Type | Privilege Scope |
|---|---|
| Read-only operation | Only view the DCC instances, and the installed CDS disks, snapshots and security group list. |
| OPS operation |
|
User Authorization
Select "Add a Privilege" in the "Operation" column of the corresponding sub-user in the "User Administration -> Sub-User Administration List Page", and then select and authorize a system privilege policy or a custom privilege policy for users.
Note: If you modify the privilege of a sub-user without modifying the existing policy rules, you can only delete the existing policy and add a policy, but you cannot unselect the privilege policy which has been added.
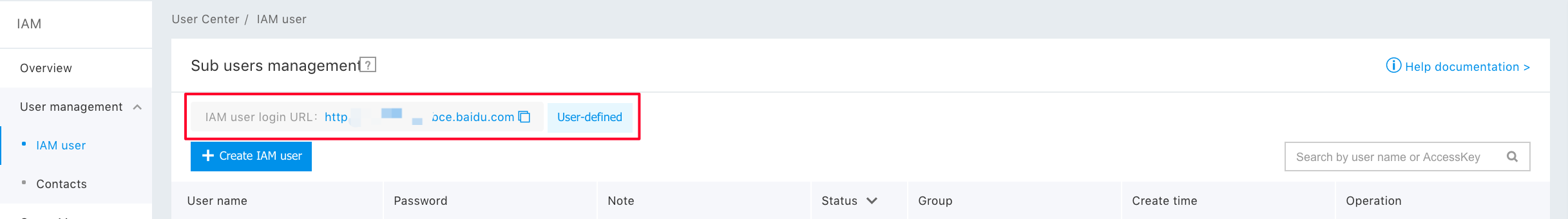
Sub-user login
After the primary account has authorized the sub-user, the link can be sent to the sub-user. In addition, the sub-user can log in to the management console of the primary account through the IAM user login link, and operate and view the primary account resources based on the authorized policy.
For more information on detailed operations, please see Identity and Access Management.
