Configuration
Log Archiving Services
Introduction
The log archiving service is closed by default, and if you have traffic log archival and other compliance requirements. After you enable the service, we will push your original traffic log to the bucket you select, with reference to BOS Billing Rules for billing. BOS storage ensures that your logs are permanently stored and are easy to manage, download and analyze.
Operation Steps
- Select "Product Service > Cloud Security > Traffic Audit > Configuration" on the navigation bar, and select Log Archiving Service on the configuration page.
-
Click the button Edit, and select to Enable the log archiving service on the pop-up menu bar, and select the address to store the logs, and click the button Confirmation to enable the log archiving service. If you have not yet created a BOS bucket in the selected storage region, please refer to Create Bucket to complete the creation.
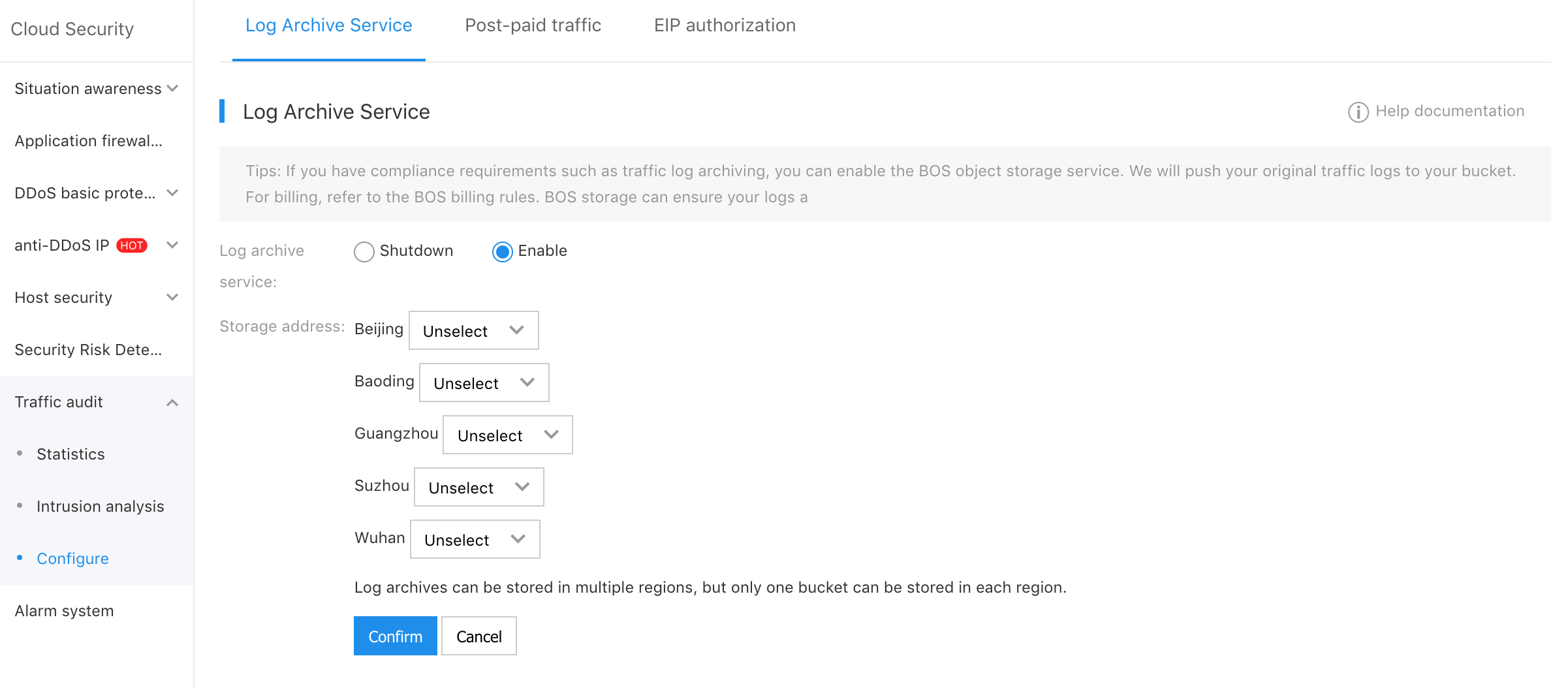
Note: The log archives can be stored in multiple regions, but each region only supports to store one bucket.
Postpaid Traffic
Introduction
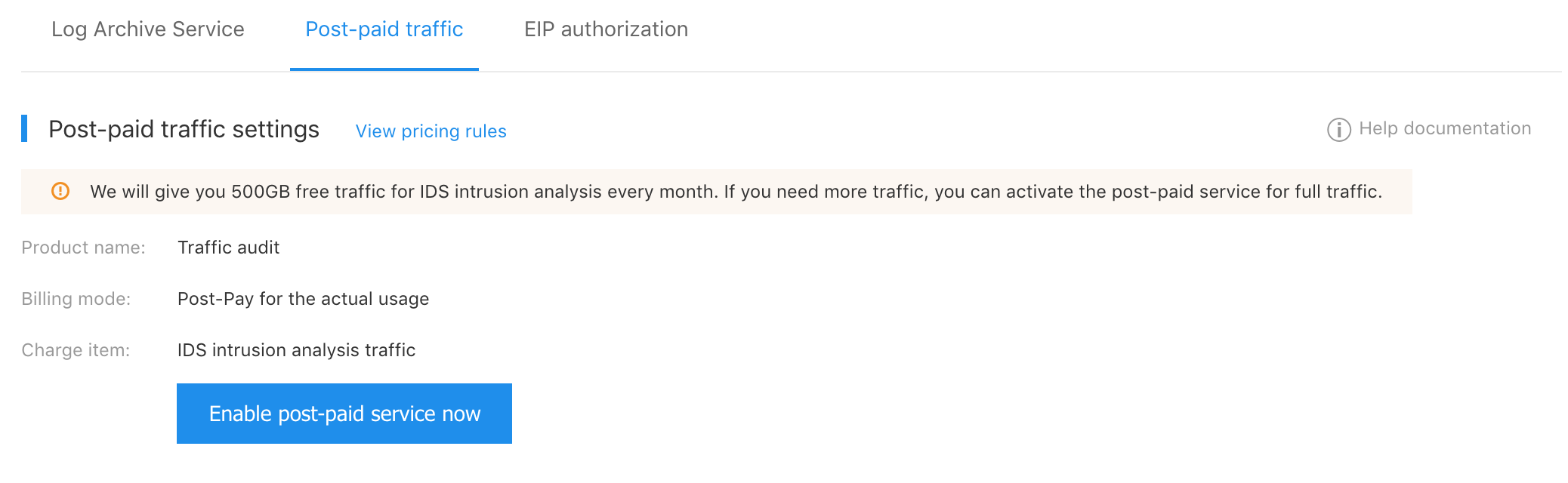
The postpaid traffic is closed by default, and we will give you 500GB IDS intrusion analysis traffic for your use; if you need more IDS intrusion detection and analysis traffic to enjoy the full service, please enable the postpaid services.
Operation Steps
- Select "Product Service > Cloud Security > Traffic Audit > Configuration" on the navigation bar, and select Postpaid traffic on the configuration page.
- Among the postpaid service items, select ON to enable the postpaid services.
EIP Authorization
Operation Steps
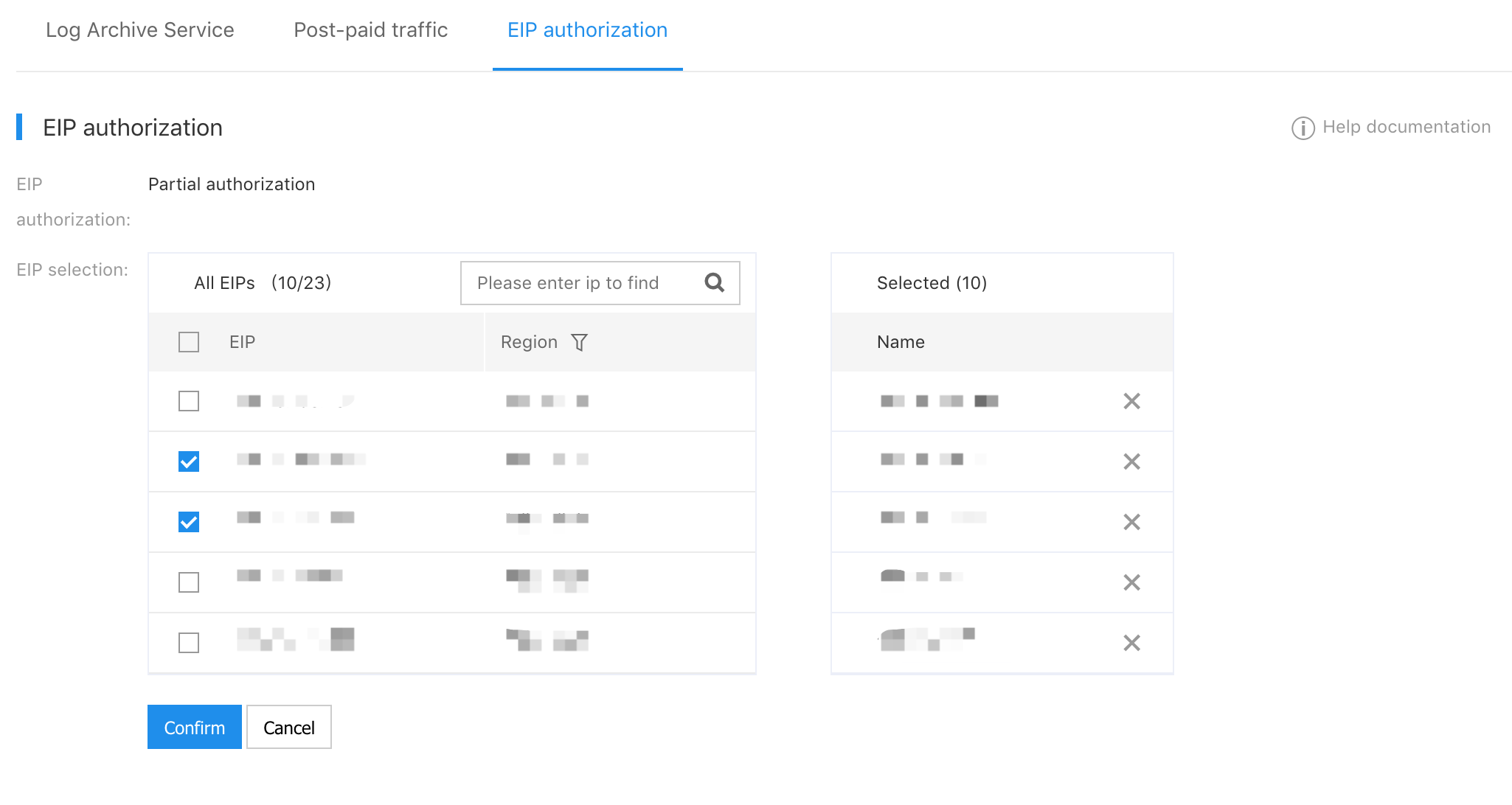
- Select "Product Service > Cloud Security > Traffic Audit > Configuration" on the navigation bar, and select EIP Authorization on the configuration page.
- Click the button Edit, and EIP authorization defaults to full authorization in the pop-up menu bar, and EIP selects to support partial selection.
-
Click Confirmation to take effect immediately.
Note: The free 500G analysis traffic per month and postpaid traffic only analyze the authorized EIP. If the user enabled EIP beforehand, and then closed after then, the statistics are retained in the statistical analysis and intrusion analysis, and there are no statistics after closure.
