Intrusion Analysis
Last Updated:2020-09-08
Report Data
The data in the report has the following meaning:
- Selection of time period: You can select the time period to view the report according to your own business demands.
- Attack source: Display the IP of the attack source you are attacked.
- Attacked assets: The EIP that you are attacked, and you are prompted for the type and region of the source to which the EIP is bound.
- Attacked domain name: Domain name attacked.
- Attack type: Type attacked.
- Attack times: Total number that the attack source attacks your resources during the polymerization period.
- Attack time: The specific time at which a source attacks your resources.
- Attack results: The intelligent judgment is made as to whether the hacker attack is successful based on HTTP bi-directional traffic.
- Trace to the source: Click "Trace to the Source", view the details of all attacks, so that you can understand how the attack has affected your business.
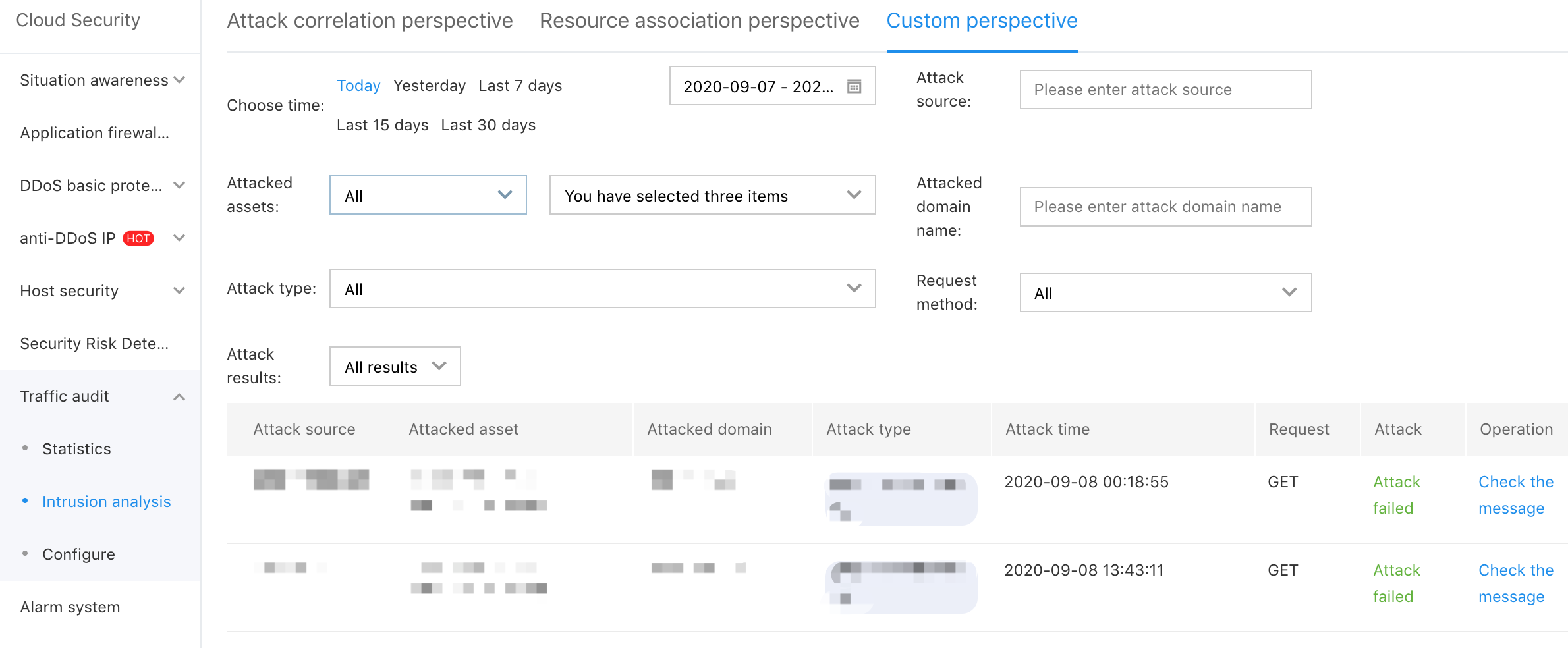
Attack Perspective
The aggregation is conducted with the attack source and time period as the dimension, which is mainly to display how an attack source attacks your resources during the selected time period, as shown in the figure below:
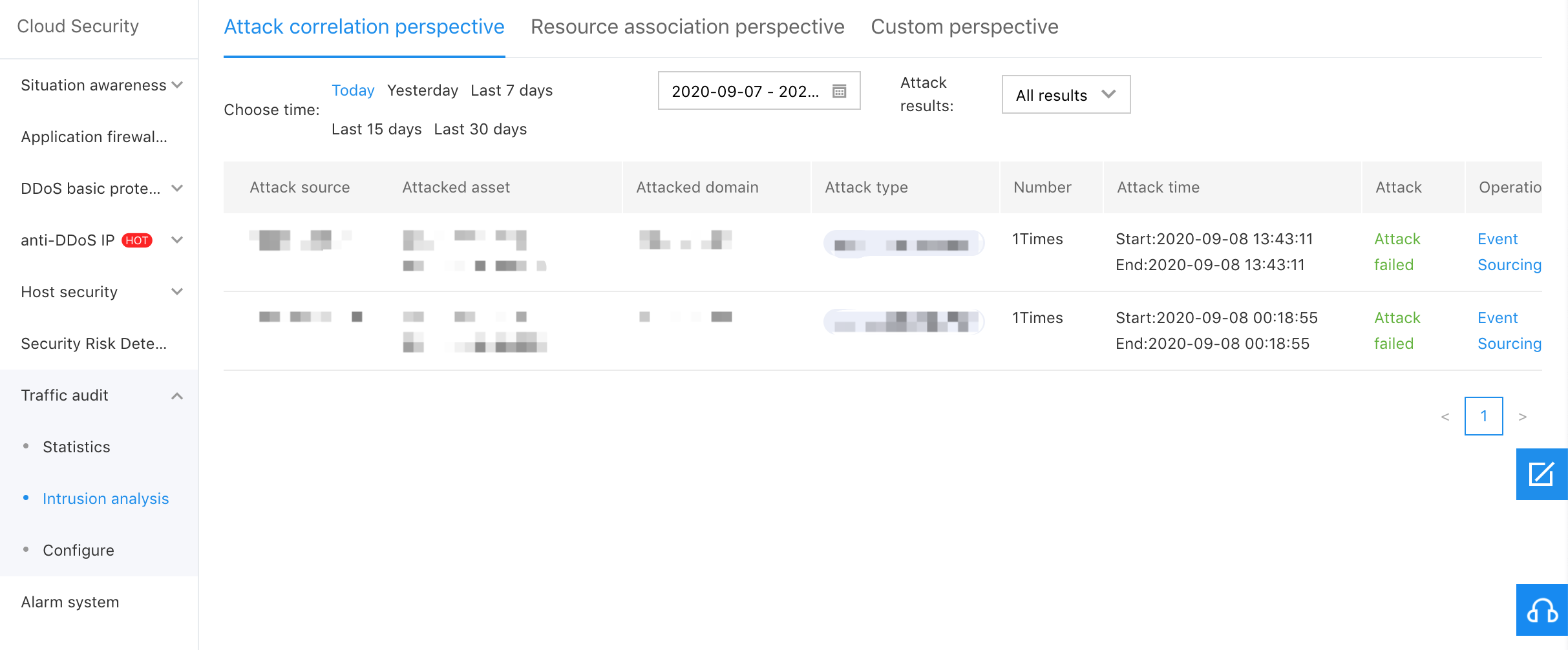
Resource Association Perspective
The aggregation is conducted with the attacked assets and time, which is mainly to display which attacks that your resource is suffered during the selected time period, as shown in the figure below:
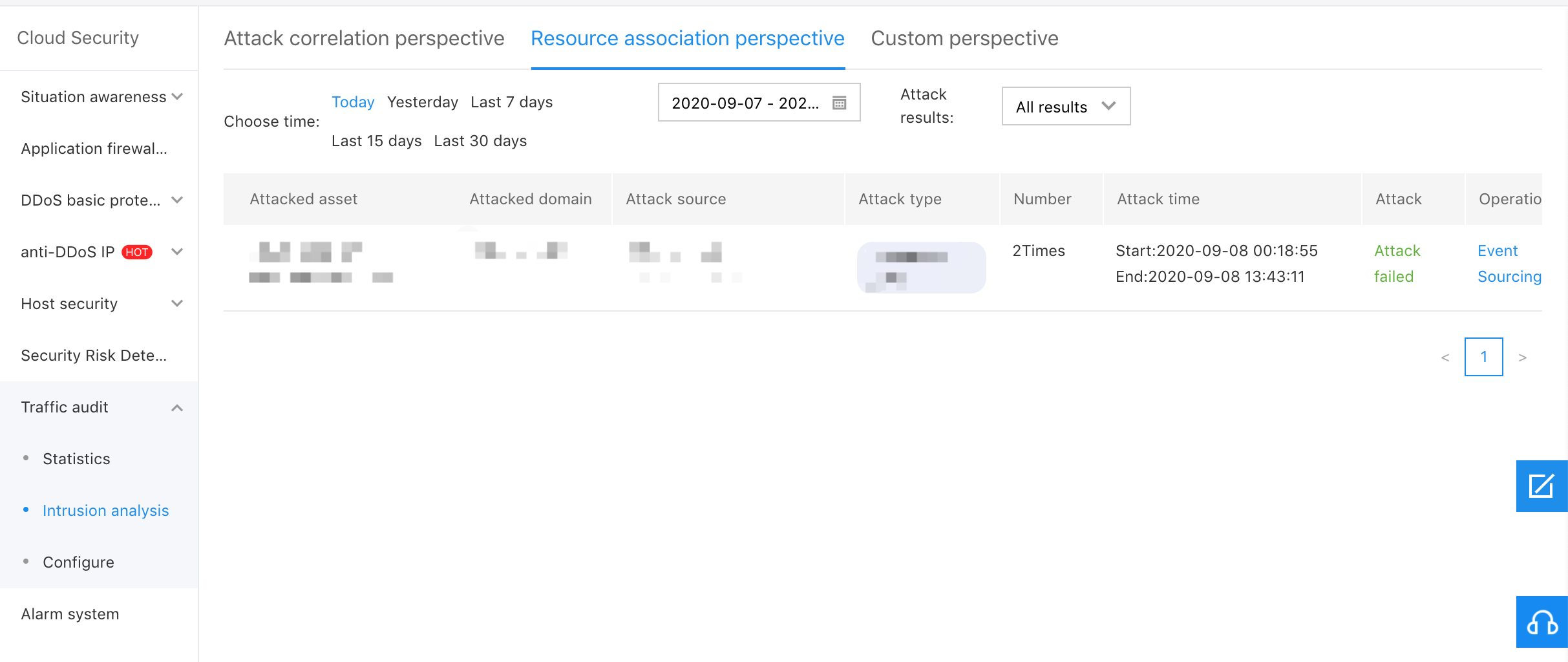
Customized Perspective
You can make customized screening for the report according to your personal needs, so as to facilitate you to locate the results you want to view, as shown in the figure below: