Identity and Access Management
Overview
Identity and Access Management (IAM) means that the original user as the primary account of the sub-account can assign the operation privilege for products or instances to the sub-account, thereby achieving fine-grained privilege management.
For example, the original user can assign the DBAudit's OPS privilege at the product level or the instance level to DBA and other front-line operators and the DBAudit's read-only privileges at the product level or the instance level to other non-operators.
Application Scenarios
- Medium- and large-enterprise customers: Perform the authorization management of multiple employees in the company;
- Technology-intensive vendors or “SAAS” platform providers: Manage the resources and privileges for the proxy clients;
- Small- and medium-size developers or small-size enterprises: Add project members or collaborators to perform resource management.
Create Subuser
-
After the primary account user logs in to his account, select the "Identity and Access Management" in the console to enter the user administration page.
- Click “User Administration” in the navbar on the left side, and click “Create Subuser” on the “Subuser” page.
- In the pop-up “Create Subuser” dialog, enter “Username”, click “OK”, and return the “Subuser Administration List” area to view the created subuser.
Configure Policy
Database Audit (DBAudit) supports system policies and user-defined policies to achieve product-level and task-level privilege control.
System Policies
The system policies are product-level privileges of Database Audit (DBAudit), including product-level management privileges, product-level OPS privileges, and product-level read-only privileges. The detailed explanation of the privilege scope is as below:
| Policy Name | Privilege Description | Privilege Scope |
|---|---|---|
| DBAuditFullControlPolicy | Management privileges for Database Audit (DBAudit) | - Audit cluster: View, add, and delete an audit cluster - Instance: Query, add, and delete an instance - Operation: Bind a policy, change a policy, and change policies in batch, enable audit, and stop audit - Audit policies: View an audit policy list, and create, edit, and delete audit policies - Others: View risk threat statistics, view audit results, view session statements, and download reports |
| DBAuditOperateAccessPolicy | OPS privileges for Database Audit (DBAudit) | - Audit cluster: View an audit cluster, and add an audit cluster - Instance: Query instances, and add instances - Operation: Bind policies, change policies, change policies in batch, enable audit, and stop audit - Audit policies: View an audit policy list, create audit policies, and edit audit policies - Others: View risk threat statistics, view audit results, view session sentences, and download statements |
| DBAuditReadOnlyAccessPolicy | Read-only privileges of Database Audit (DBAudit) | View an audit cluster, query instances, view an audit policy list, view risk threat statistics, view audit results, view session statements, and download reports |
Custom Policies
The primary user can add custom policies by clicking “Policy Management > Create Policies” to control task-level privileges. There are two ways in adding custom policies, including “Create by Policy Builder” and “Create by Policy Syntax”. The user can modify policies based on privilege settings. For the specific configuration method, see Create Custom Policy.
The scope of the custom privilege is as follows:
| Privilege Description | Privilege Scope |
|---|---|
| Management privileges | - Audit cluster: View and delete an audit cluster - Instance: Query and add instances - Operation: Bind policies, change policies, change policies in batch, and enable and stop audit - Audit policies: View an audit policy list, edit audit policies, and delete audit policies - Others: View risk threat statistics, view audit results, view session statements, and download reports. |
| OPS privileges | - Audit cluster: View an audit cluster - Instance: Query and add instances - Operation: Bind policies, change policies, change policies in batch, and enable and stop audit - Audit policies: View an audit policy list, and edit audit policies - Others: View risk threat statistics, view audit results, view session statements, and download reports. |
| Read-only privilege | View an audit cluster, query instances, view an audit policy list, view risk threat statistics, view audit results, view session statements, and download reports |
Descriptions: 1. The management privileges and OPS privileges of custom policies don’t support the privileges of adding an audit cluster and creating audit policies. 2. If the privileges of the operations are required, you can control them with product-level privileges.
User Authorization
1. Select “Add Privilege” in the “Operation” column of the corresponding subuser in “User Administration -> Subuser”.
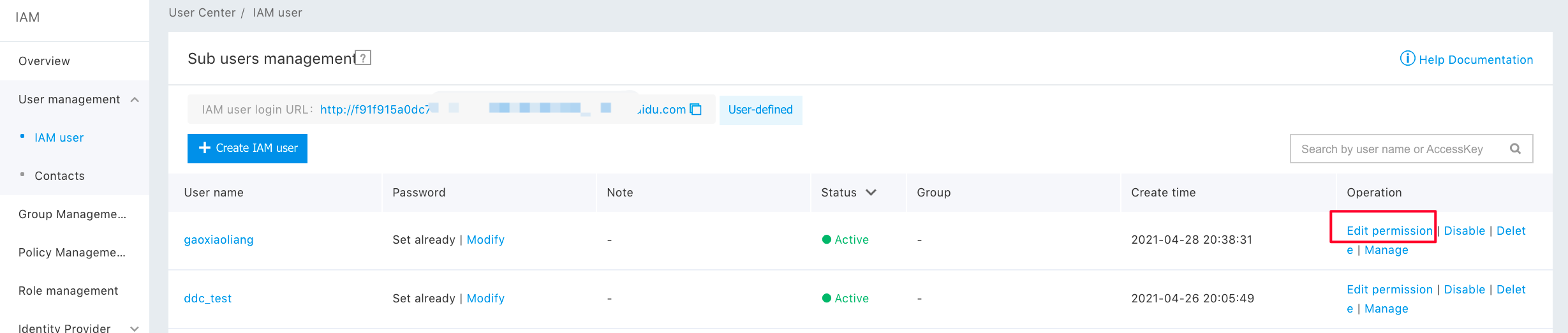
2. You can select “All Policies”, “System Privilege Policies”, or “Custom Policies” for authorization in this pop-up window.
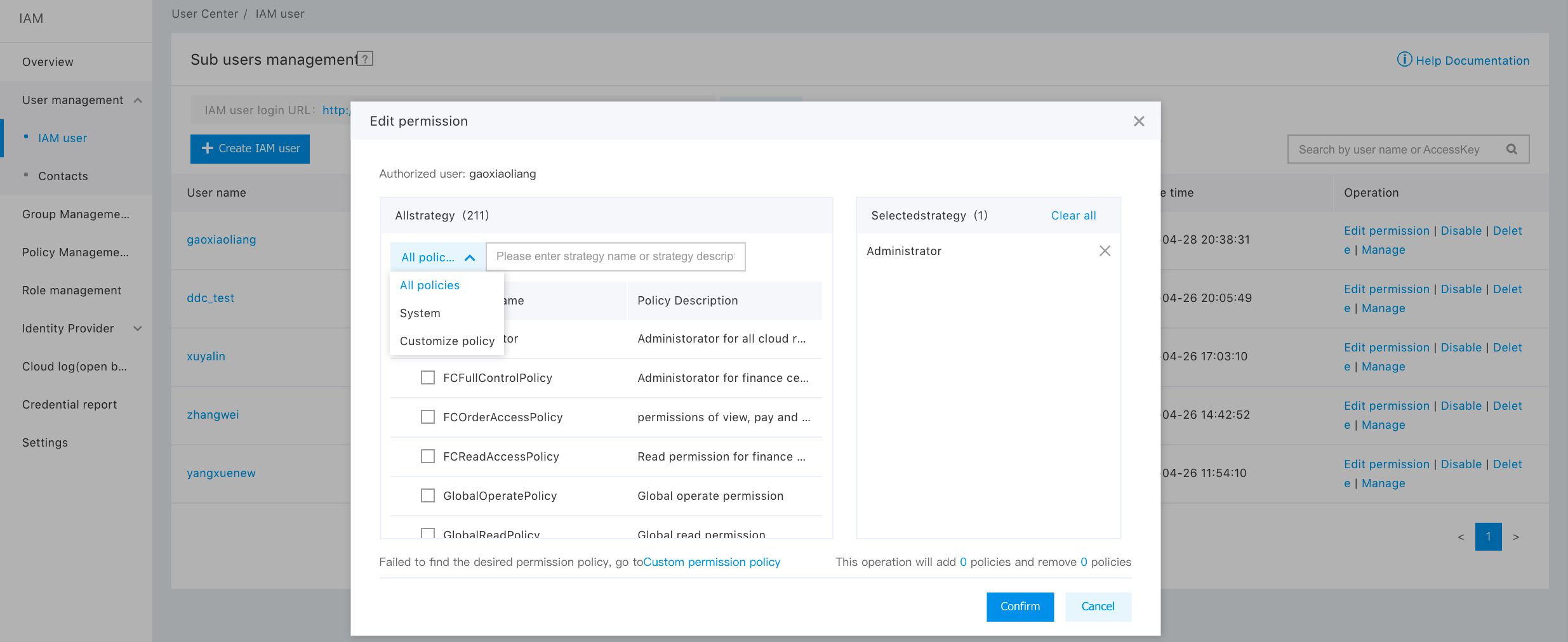
Description: If you modify the privileges of a subuser without modifying the existing policy rules, you can only delete the existing policies and add new policies, but cannot unselect the added policy privileges.
Subuser Login
After the primary account completes the authorization of a subuser, it can send the link to the subuser. Then, the subuser can log in to the Management Console of the primary account via the subuser login link, operate and view the primary account resource according to the authorized policies.
Relevant Documentations
For other operations, see Identity and Access Management.
