Identity and Access Management (IAM)
Introduction
Identity and Access Management (IAM) is used to help users manage resource access privileges under cloud accounts. The IAM is applicable to different roles in the enterprise and can grant different employees different privileges of using products. If any resources need multi-user collaborative operation in your enterprise, you are highly recommended to use the IAM.
The IAM is applicable to the following scenarios:
- Medium and large-sized enterprises: Grant multiple employees the authorization for management in the enterprise;
- Technology-based vendors or SAAS platform providers: Perform resource management and access control for proxy customers;
- Small and medium developers or small-sized enterprises: Add project members or collaborators to perform resource management.
Create User
- After the primary account user logs in to the account, the user selects the "Identity and Access Management" in the console to enter the user administration page.

- Click the "User Administration" in the left navbar, and then click the "New User" on the "Sub-User Administration List" page.
- In the pop-up "New User" dialog box, enter and confirm the "User Name", and then return to the "Sub-User Administration List" area to view the created sub-user.
Privilege Policy Configuration
The privilege policies are divided into two categories, that is, the [System Privilege Policy](#System Privilege Policy) and [Custom Privilege Policy](#Custom Privilege Policy) to realize the privilege control of BMS at the product and instance levels respectively.
- System privilege policy: A set of privileges predefined by the Baidu AI Cloud system for resource management. This policy enables the system to grant sub-users privileges directly, and users can only use them without modification.
- Custom privilege policy: A set of privileges created by users for refined resource management. This policy enables the system to configure single instances to flexibly manage user privileges required by accounts.
System Privilege Policy
The system privilege policy is a set of privileges that are frequently used but cannot be edited by users. Kafka provides three default system privilege policies for configuration, which are shown in the following table:
| Policy Name | Description | Included Privileges |
|---|---|---|
| KAFKAReadPolicy | Read-only privilege | The topic query operation privilege and certificate query operation privilege. |
| KAFKAWritePolicy | Read/Write privilege | The topic query operation privilege, topic update operation privilege, certificate query operation privilege, and certificate update operation privilege. |
| KAFKAFullControlPolicy | Full control privilege | All privileges of Kafka products |
Custom Privilege Policy
The custom privilege policy enables users to freely configure their privilege policies upon their requirements. These policies can be configured in two ways, that is, the policy generator and editing policy files.
Configure a privilege with the policy generator
The policy generator is suitable for scenarios that need to control resource access. The resources controlled by Kafka privileges include topics and certificates. The policy defined by the policy generator can control the specific resource to be accessed. For example, you can set up which certificates users can download, and which topics can be modified and deleted by users.
Scenario example: Configure a certificate that users can download.
Operation steps:
Create a privilege policy: Identity and Access Management -> Policy Management -> Create a Policy.
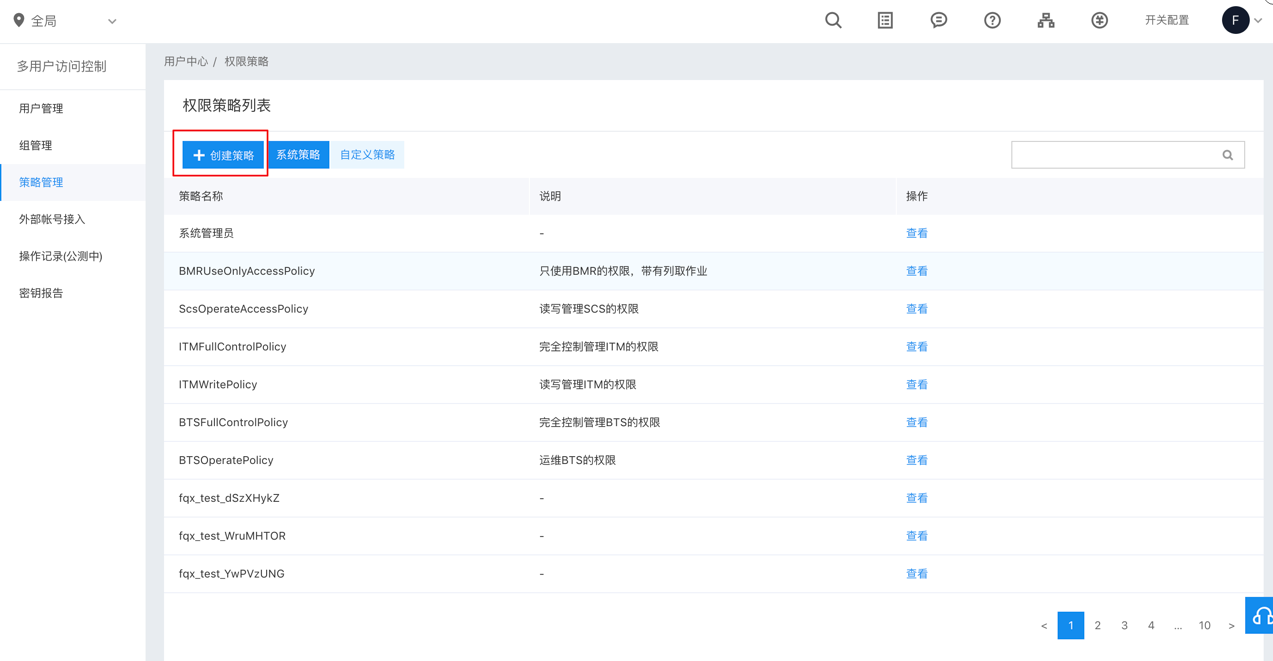
Enter a policy name and select “Baidu Messaging System Kafka” as the service type.
Select “Policy Generator” as the policy generation method.

Because we do not configure the role of topics, we do not need to configure the privilege for the Kafka topic. Instead, we need to configure the privilege of the Kafka certificate. Select the privilege to “Download a Certificate” -> Select the region where the certificate is located-> Select the certificate to be authorized. After that, click the “Finish” button to complete the policy configuration.

At this moment, you can see the policy you just defined from the “Custom Policy” list in the Policy Management.

Configure a privilege with the ACL policy file
The ACL policy configuration file can be interpreted as a JSON string for configuring privilege policy rules. Whether it is a system policy or a user-customized policy, it is eventually mapped into an ACL JSON string. With the ACL policy configuration file, users can freely define a privilege policy but need to understand the meaning of ACL strings. Kafka provides a common ACL string configuration template. Users can configure their own policies by referring to this template. For example, configure a separate privilege policy for creating a topic. For more information on the syntax of editing an ACL privilege policy, please see the documentation of the Policy Syntax.
Scenario example: Configure a privilege policy for creating a topic and grant the authorization to users.
Operation steps:
Create a privilege policy: Identity and Access Management -> Policy Management -> Create a Policy.

Fill in a policy name, and select “Baidu Messaging System Kafka” as the service type, “Edit a Policy File” as the policy generation method, and “kafka_acl” as the policy template.

Configure an ACL string, which includes creating a topic privilege with the string identifier CreateTopic. For more information on other privilege labels, please see the privilege labels in the Privilege Models as follows.

After clicking “Finish,” you can view the created policy in the “Custom Policy” list.

User Authorization
Select "Add a Privilege" in the "Operation" column of the corresponding sub-user in the "User Authorization -> Sub-User Administration List Page," and then select and authorize a system privilege policy or a custom privilege policy for users.

Note: If you modify the privilege of a sub-user without modifying the existing policy rules, you can only delete the existing policy and add a policy, but you cannot unselect the privilege policy which has been added.
Sub-User Login
After the primary account has authorized the sub-user, the link can be sent to the sub-user. In addition, the sub-user can log in to the management console of the primary account through the IAM user login link, and operate and view the primary account resources based on the authorized policy.

For more information on detailed operations, please see Identity and Access Management.
Kafka Privilege Model
The Kafka privilege model is mainly used to describe the range and granularity of operation privileges users can control.
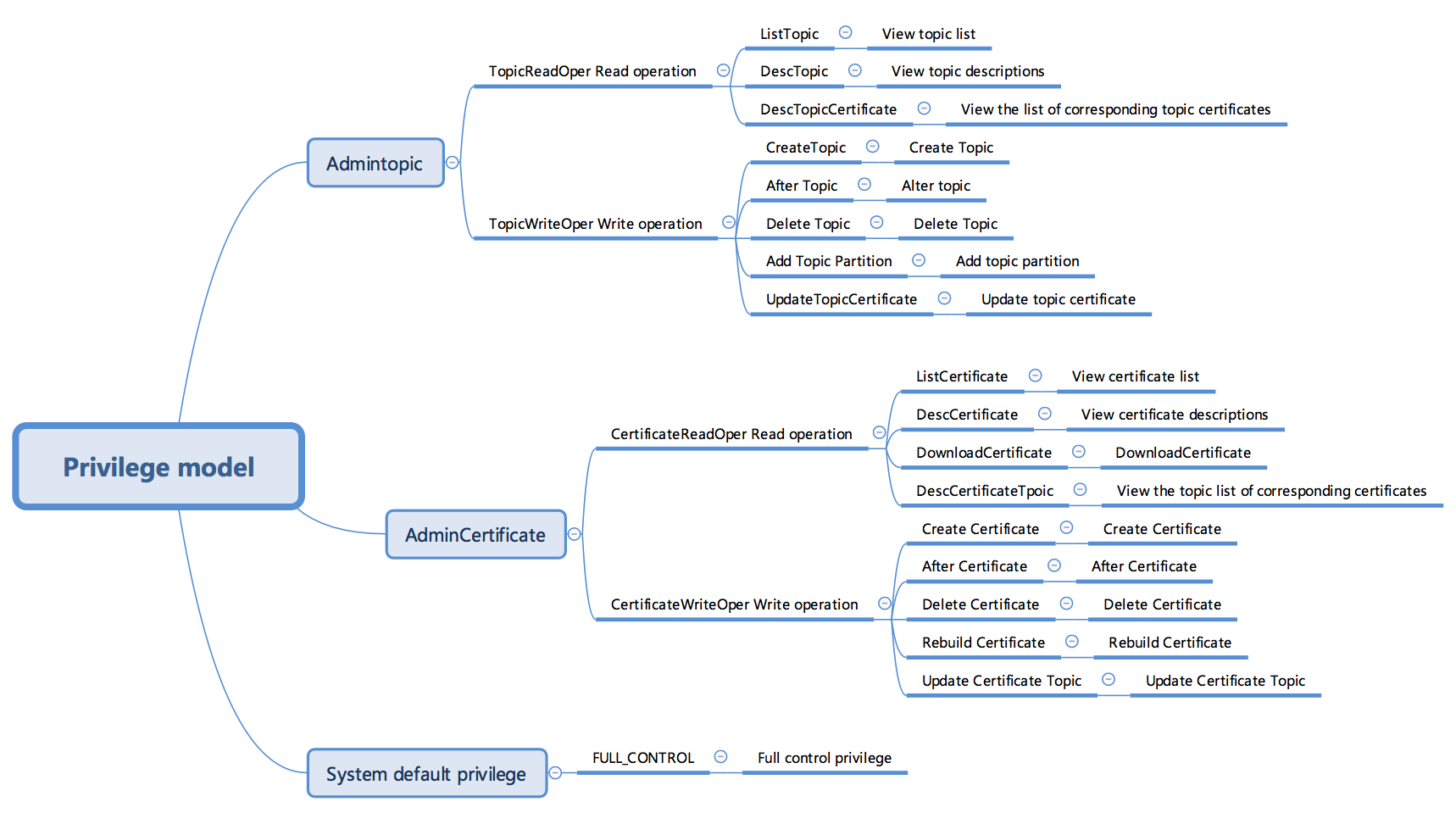
- The Kafka privilege model involves two types of resource privilege management, namely the topic privilege management and the certificate privilege management. The first one means that which operation privileges sub-users have for a topic, while the second one means that which operation privileges sub-users have for a certificate.
-
As shown in the figure above, the entire privilege model is divided into three layers. Among them, the leaf node is the privilege with the finest granularity, and a string label is the only identifier of each privilege, which is used to distinguish different privileges when different privilege policies are defined. The meaning of different privileges is listed in the following table:
Privilege Label Layer Description FULL_CONTROL 1 all of the privileges that the "Parent account” has. AdminTopic 1 the privileges to add, delete, modify, and query a topic, including all the topic operation-related privilege with the fine granularity, for example, creating a topic. AdminCertificate 1 the privileges to add, delete, modify and query a certificate, including all the certificate operation-related privilege with the fine granularity. TopicReadOper 2 the privilege to query a topic, including the privilege to query the topic list, topic details, etc. TopicWriteOper 2 the privilege to update topic-related operations, including creating, modifying, and deleting a topic. CertificateReadOper 2 the privilege to query a certificate, including the privilege to query the certificate list, download a certificate, etc. CertificateWriteOper 2 the privilege to update certificate-related operations, including creating, modifying, deleting and regenerating a certificate. ListTopic 3 the privilege to view the topic list on the page of the topic list. DescTopic 3 the privilege to view the topic details on the page which is entered after you click a topic name in the topic list. DescTopicCertificate 3 the privilege to view the topic list authorized by the topic, corresponding to the operation of “View a Certificate” on the page of the topic list. CreateTopic 3 the privilege to view the topic list authorized by the topic, corresponding to the operation of “Create a Topic” on the page of the topic list. AlterTopic 3 the privilege to modify the topic meta-information, of which the corresponding operation is not available in the current console. DeleteTopic 3 the privilege to delete a topic, corresponding to the operation of “Create a Topic” on the page of the topic list. AddTopicPartition 3 the privilege to add a partition to the topic, corresponding to the operation of “Make Partitions with Expanded Capacity” on the page of the topic list. UpdateTopicCertificate 3 the privilege to modify the authorization of the topic certificate, corresponding to the operation of editing the certificate privilege on the page of “View a Certificate” on the page of the topic list. ListCertificate 3 the privilege to view the certificate list on the page of the certificate list. DescCertificate 3 the privilege to view the certificate details, of which the corresponding operation is not available in the current console. DownloadCertificate 3 the privilege to download a certificate from the key downloading link on the page of the certificate list. DescCertificateTopic 3 the privilege to view the topic list corresponding to a certificate on the page opened by the operation of “View a Topic” on the page of the certificate list. CreateCertificate 3 the privilege to create a certificate, corresponding to the operation of “Create a Certificate” on the page of the certificate list. AlterCertificate 3 the privilege to modify a certificate, corresponding to the operation of modifying the certificate name on the page of the certificate list. DeleteCertificate 3 the privilege to delete a certificate, corresponding to the operation of “Delete a Certificate” on the page of the certificate list. RebuildCertificate 3 the privilege to regenerate a certificate, corresponding to the operation of “Regenerate a Certificate” on the page of the certificate list. UpdateCertificateTopic 3 Modify the certificate privilege of accessing a topic, corresponding to the operation of editing the certificate privilege on the page of “View a Topic” on the page of the certificate list.
